Burp Suite Certified Practitioner Roadmap - BSCP

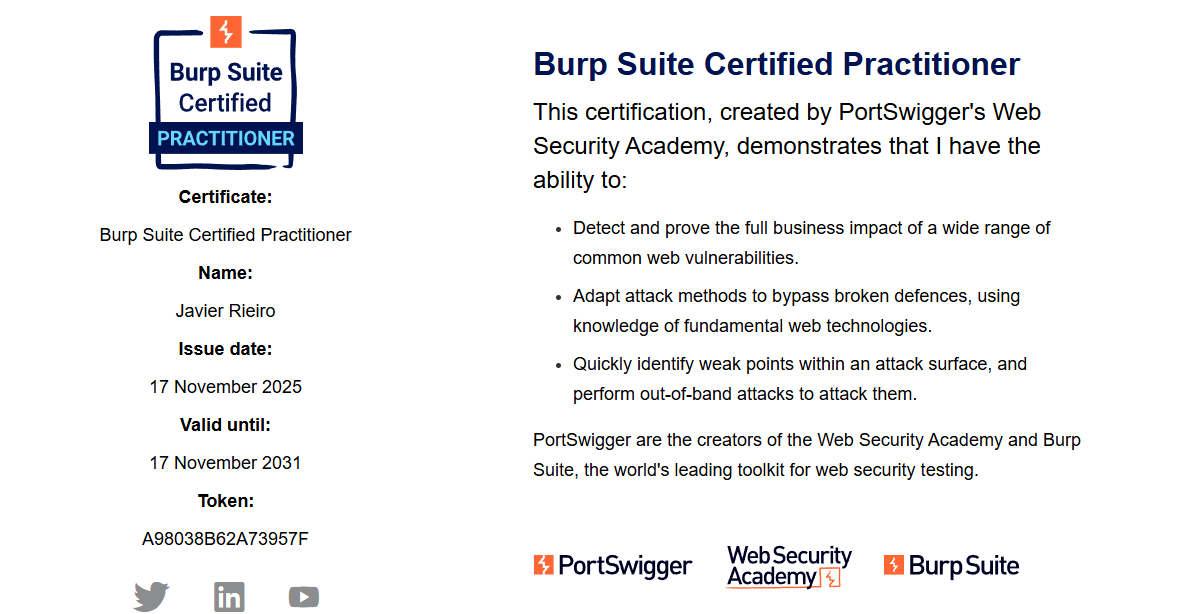 Roadmap to complete the Burp Suite Certified Practitioner (BSCP) certification.
Roadmap to complete the Burp Suite Certified Practitioner (BSCP) certification.

 Roadmap to complete the Burp Suite Certified Practitioner (BSCP) certification.
Roadmap to complete the Burp Suite Certified Practitioner (BSCP) certification.

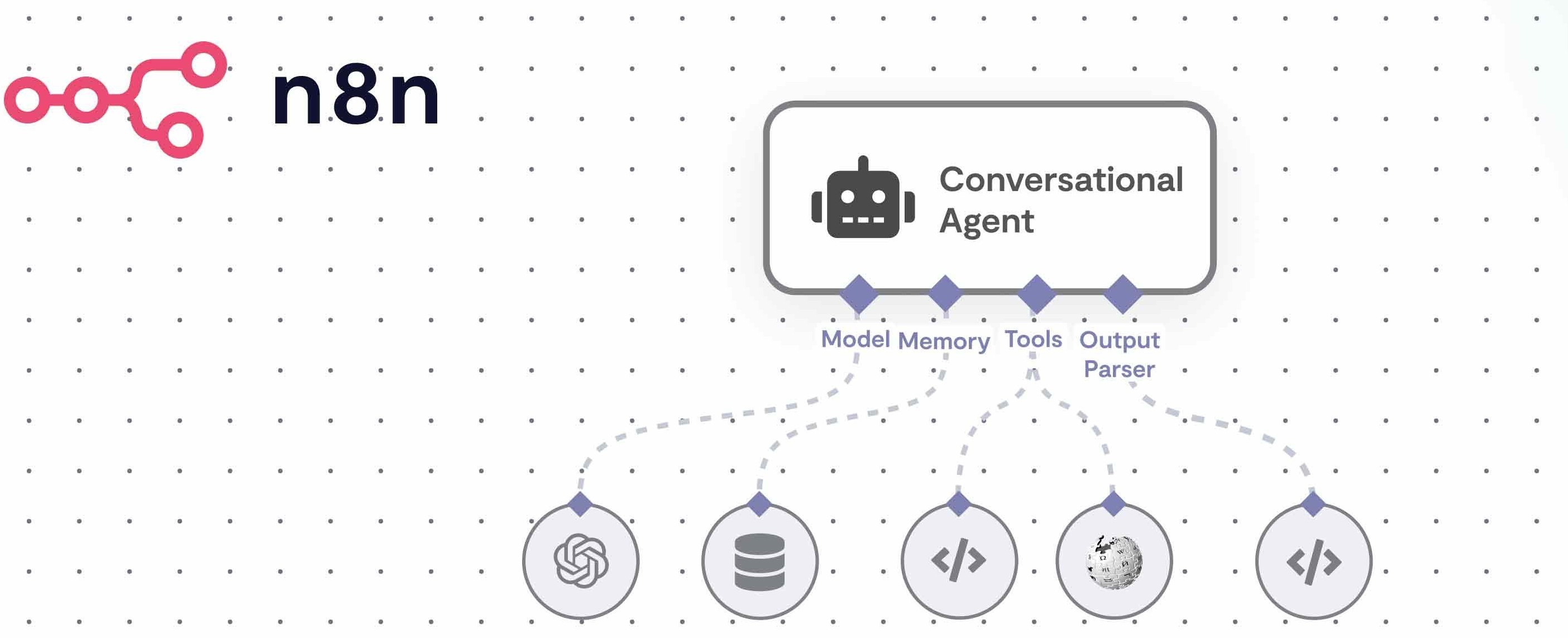 Plantilla para crear promts en agentes de IA.
Plantilla para crear promts en agentes de IA.

 All Prototype Pollution labs of PortSwigger.
All Prototype Pollution labs of PortSwigger.

 All GraphQL API vulnerabilities labs of PortSwigger.
All GraphQL API vulnerabilities labs of PortSwigger.

 All API testing labs of PortSwigger.
All API testing labs of PortSwigger.

 All File upload vulnerabilities of PortSwigger.
All File upload vulnerabilities of PortSwigger.

 All Path Traversal labs of PortSwigger.
All Path Traversal labs of PortSwigger.

 All OS Command Injection labs of PortSwigger.
All OS Command Injection labs of PortSwigger.

 All Access control vulnerabilities labs of PortSwigger.
All Access control vulnerabilities labs of PortSwigger.

 All Server-side request forgery labs of PortSwigger.
All Server-side request forgery labs of PortSwigger.