Burp Suite Certified Practitioner Roadmap - BSCP

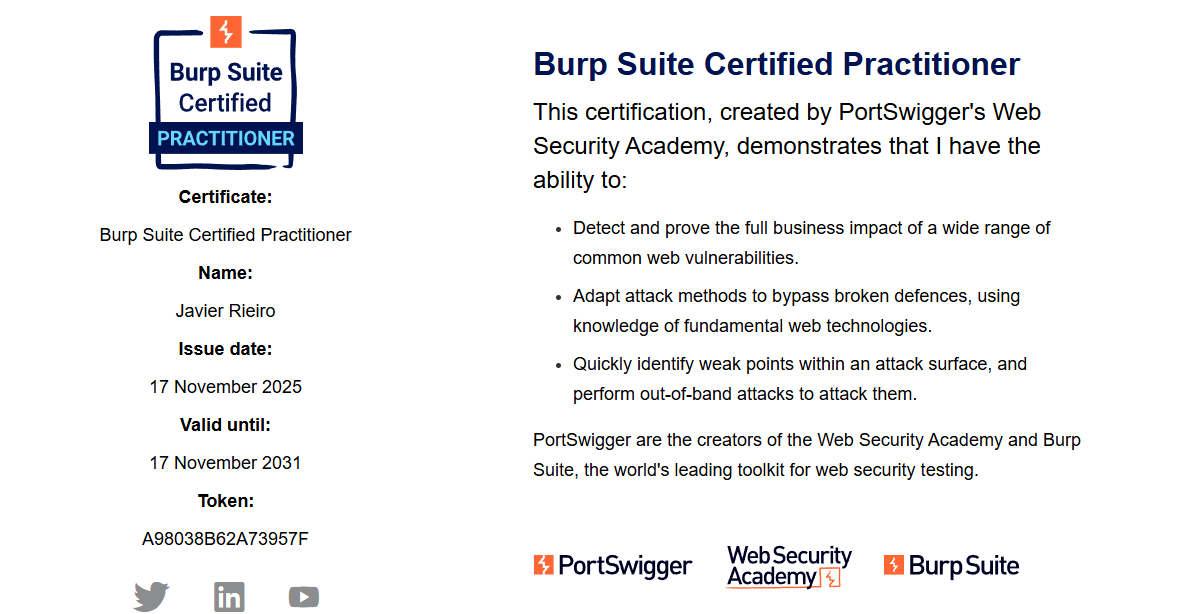 Roadmap to complete the Burp Suite Certified Practitioner (BSCP) certification.
Roadmap to complete the Burp Suite Certified Practitioner (BSCP) certification.

 Roadmap to complete the Burp Suite Certified Practitioner (BSCP) certification.
Roadmap to complete the Burp Suite Certified Practitioner (BSCP) certification.

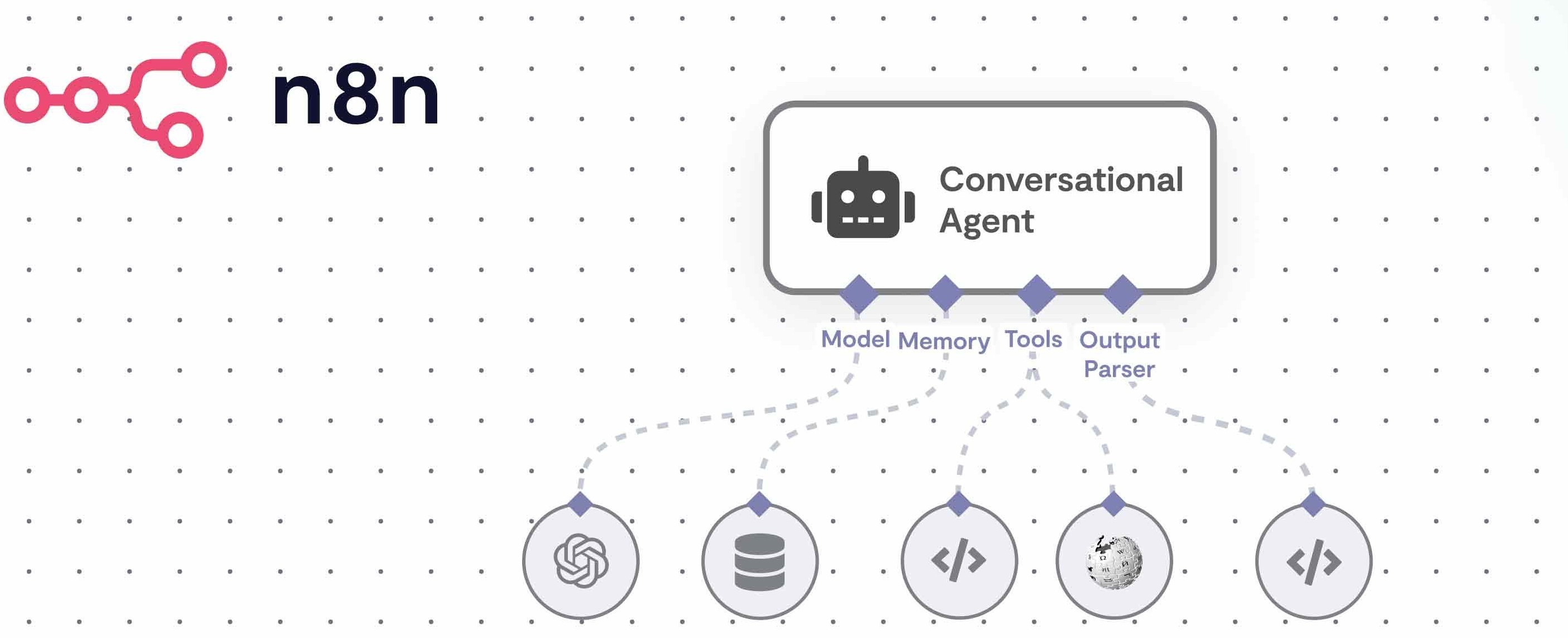 Plantilla para crear promts en agentes de IA.
Plantilla para crear promts en agentes de IA.

 All Prototype Pollution labs of PortSwigger.
All Prototype Pollution labs of PortSwigger.

 All GraphQL API vulnerabilities labs of PortSwigger.
All GraphQL API vulnerabilities labs of PortSwigger.

 All API testing labs of PortSwigger.
All API testing labs of PortSwigger.

 All File upload vulnerabilities of PortSwigger.
All File upload vulnerabilities of PortSwigger.

 All Path Traversal labs of PortSwigger.
All Path Traversal labs of PortSwigger.

 All OS Command Injection labs of PortSwigger.
All OS Command Injection labs of PortSwigger.

 All Access control vulnerabilities labs of PortSwigger.
All Access control vulnerabilities labs of PortSwigger.

 All Server-side request forgery labs of PortSwigger.
All Server-side request forgery labs of PortSwigger.

 All XML external entity labs of PortSwigger with additional CheetSheet.
All XML external entity labs of PortSwigger with additional CheetSheet.

 All Cross-origin resource sharing (CORS) labs of PortSwigger.
All Cross-origin resource sharing (CORS) labs of PortSwigger.

 All DOM-Based Vulnerabilites labs of PortSwigger.
All DOM-Based Vulnerabilites labs of PortSwigger.

 The challenge code performs unsafe YAML deserialization (yaml.load) on user-controlled input without proper validation or sandboxing, allowing remote code execution (RCE) via crafted payloads. A token-based access control is implemented comparing a guest token with a generated root token, but the check is flawed or bypassable, enabling an attacker to pass the authentication and reach the vulnerable YAML deserialization code. However, an attacker can bypass or control these tokens (e.g., via predictable token generation using the current time as seed), allowing access to the deserialization block where yaml.load is called with yaml.Loader. This allows arbitrary command execution via the !!python/object/apply:os.system YAML tag or similar techniques.
The challenge code performs unsafe YAML deserialization (yaml.load) on user-controlled input without proper validation or sandboxing, allowing remote code execution (RCE) via crafted payloads. A token-based access control is implemented comparing a guest token with a generated root token, but the check is flawed or bypassable, enabling an attacker to pass the authentication and reach the vulnerable YAML deserialization code. However, an attacker can bypass or control these tokens (e.g., via predictable token generation using the current time as seed), allowing access to the deserialization block where yaml.load is called with yaml.Loader. This allows arbitrary command execution via the !!python/object/apply:os.system YAML tag or similar techniques.

 All Cross-site request forgery labs of PortSwigger.
All Cross-site request forgery labs of PortSwigger.

 All Cross-site Scripting labs of PortSwigger with additional CheetSheet.
All Cross-site Scripting labs of PortSwigger with additional CheetSheet.

 Denial of Service vulnerability in Instagram causing a specific message thread to become unusable. Out of scope for Meta’s bug bounty program due to available self-mitigation (e.g., deleting the thread).
Denial of Service vulnerability in Instagram causing a specific message thread to become unusable. Out of scope for Meta’s bug bounty program due to available self-mitigation (e.g., deleting the thread).

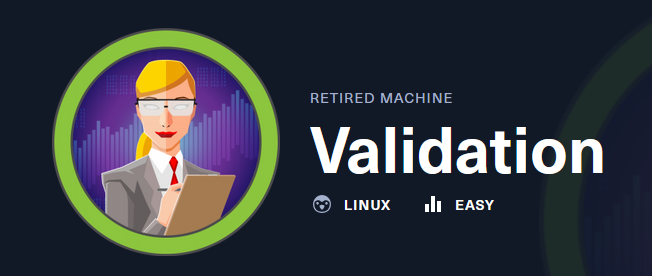 Validation is another box HTB made for the UHC competition. It is a qualifier box, meant to be easy and help select the top ten to compete later this month. Once it was done on UHC, HTB makes it available. In this box, I’ll exploit a second-order SQL injection, write a script to automate the enumeration, and identify the SQL user has FILE permissions. I’ll use that to write a webshell, and get execution. For root, it’s simple password reuse from the database. In Beyond Root, I’ll look at how this box started and ended in a container.
Validation is another box HTB made for the UHC competition. It is a qualifier box, meant to be easy and help select the top ten to compete later this month. Once it was done on UHC, HTB makes it available. In this box, I’ll exploit a second-order SQL injection, write a script to automate the enumeration, and identify the SQL user has FILE permissions. I’ll use that to write a webshell, and get execution. For root, it’s simple password reuse from the database. In Beyond Root, I’ll look at how this box started and ended in a container.

 All SQL Injection labs of PortSwigger with additional CheetSheet.
All SQL Injection labs of PortSwigger with additional CheetSheet.

 Active is an easy to medium difficulty machine, which features two very prevalent techniques to gain privileges within an Active Directory environment.
Active is an easy to medium difficulty machine, which features two very prevalent techniques to gain privileges within an Active Directory environment.

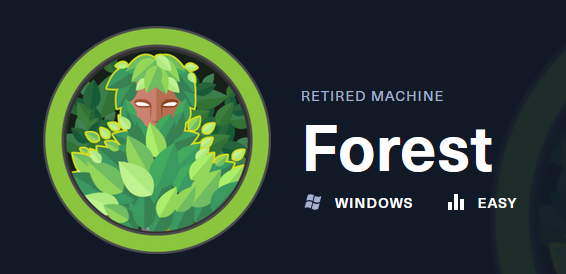 Forest is an easy Windows machine that showcases a Domain Controller (DC) for a domain in which Exchange Server has been installed. The DC allows anonymous LDAP binds, which are used to enumerate domain objects. The password for a service account with Kerberos pre-authentication disabled can be cracked to gain a foothold. The service account is found to be a member of the Account Operators group, which can be used to add users to privileged Exchange groups. The Exchange group membership is leveraged to gain DCSync privileges on the domain and dump the NTLM hashes, compromising the system.
Forest is an easy Windows machine that showcases a Domain Controller (DC) for a domain in which Exchange Server has been installed. The DC allows anonymous LDAP binds, which are used to enumerate domain objects. The password for a service account with Kerberos pre-authentication disabled can be cracked to gain a foothold. The service account is found to be a member of the Account Operators group, which can be used to add users to privileged Exchange groups. The Exchange group membership is leveraged to gain DCSync privileges on the domain and dump the NTLM hashes, compromising the system.

 Sauna is an easy difficulty Windows machine that features Active Directory enumeration and exploitation. Possible usernames can be derived from employee full names listed on the website. With these usernames, an ASREPRoasting attack can be performed, which results in hash for an account that doesn't require Kerberos pre-authentication. This hash can be subjected to an offline brute force attack, in order to recover the plaintext password for a user that is able to WinRM to the box. Running WinPEAS reveals that another system user has been configured to automatically login and it identifies their password. This second user also has Windows remote management permissions. BloodHound reveals that this user has the DS-Replication-Get-Changes-All extended right, which allows them to dump password hashes from the Domain Controller in a DCSync attack. Executing this attack returns the hash of the primary domain administrator, which can be used with Impacket-psexec.py in order to gain a shell on the bo...
Sauna is an easy difficulty Windows machine that features Active Directory enumeration and exploitation. Possible usernames can be derived from employee full names listed on the website. With these usernames, an ASREPRoasting attack can be performed, which results in hash for an account that doesn't require Kerberos pre-authentication. This hash can be subjected to an offline brute force attack, in order to recover the plaintext password for a user that is able to WinRM to the box. Running WinPEAS reveals that another system user has been configured to automatically login and it identifies their password. This second user also has Windows remote management permissions. BloodHound reveals that this user has the DS-Replication-Get-Changes-All extended right, which allows them to dump password hashes from the Domain Controller in a DCSync attack. Executing this attack returns the hash of the primary domain administrator, which can be used with Impacket-psexec.py in order to gain a shell on the bo...

 Tenet is a Medium difficulty machine that features an Apache web server. It contains a Wordpress blog with a few posts. One of the comments on the blog mentions the presence of a PHP file along with it's backup. It is possible after identificaiton of the backup file to review it's source code. The code in PHP file is vulnerable to an insecure deserialisation vulnerability and by successful exploiting it a foothold on the system is achieved. While enumerating the system it was found that the Wordpress configuration file can be read and thus gaining access to a set of credentials. By using them we can move laterally from user ‘www-data’ to user ‘Neil’. Further system enumeration reveals that this user have root permissions to run a bash script through ‘sudo’. The script is writing SSH public keys to the ‘authorized_keys’ file of the ‘root’ user and is vulnerable to a race condition. After successful exploitation, attackers can write their own SSH keys to the ‘authorized_keys’ file and use t...
Tenet is a Medium difficulty machine that features an Apache web server. It contains a Wordpress blog with a few posts. One of the comments on the blog mentions the presence of a PHP file along with it's backup. It is possible after identificaiton of the backup file to review it's source code. The code in PHP file is vulnerable to an insecure deserialisation vulnerability and by successful exploiting it a foothold on the system is achieved. While enumerating the system it was found that the Wordpress configuration file can be read and thus gaining access to a set of credentials. By using them we can move laterally from user ‘www-data’ to user ‘Neil’. Further system enumeration reveals that this user have root permissions to run a bash script through ‘sudo’. The script is writing SSH public keys to the ‘authorized_keys’ file of the ‘root’ user and is vulnerable to a race condition. After successful exploitation, attackers can write their own SSH keys to the ‘authorized_keys’ file and use t...

 Writer is a medium Linux machine that outlines poor coding practices and presents how a file read vulnerability through SQL injection can lead to disclosure of source code files which include credentials. The combination of password reuse on the SMB service with a blind SSRF exploitation via an image upload function can lead to a foothold on the system. By abusing Django features it is possible to extract and crack user credentials. Further abusing multiple misconfigurations in Postfix service leads to exploit privileges in the apt service folders allowing those users to execute commands as root through a script that updates the machine every minute.
Writer is a medium Linux machine that outlines poor coding practices and presents how a file read vulnerability through SQL injection can lead to disclosure of source code files which include credentials. The combination of password reuse on the SMB service with a blind SSRF exploitation via an image upload function can lead to a foothold on the system. By abusing Django features it is possible to extract and crack user credentials. Further abusing multiple misconfigurations in Postfix service leads to exploit privileges in the apt service folders allowing those users to execute commands as root through a script that updates the machine every minute.

 Artificial Season 8 (Week 6)
Artificial Season 8 (Week 6)

 Heal is a medium-difficult Linux machine that features a website vulnerable to arbitrary file read, allowing us to extract sensitive credentials. The server also hosts a LimeSurvey instance, where the leaked credentials can be used to log in as an administrator. Since administrators can upload plugins, we can exploit this to upload a malicious plugin and gain a reverse shell as the ‘www-data’ user. Further enumeration reveals the database password for LimeSurvey, which is reused by the system user ‘ron’, allowing us to escalate access. The server also runs a local instance of the Consul Agent as ‘root’. By registering a malicious service via the Consul API, we can escalate privileges and gain root access.
Heal is a medium-difficult Linux machine that features a website vulnerable to arbitrary file read, allowing us to extract sensitive credentials. The server also hosts a LimeSurvey instance, where the leaked credentials can be used to log in as an administrator. Since administrators can upload plugins, we can exploit this to upload a malicious plugin and gain a reverse shell as the ‘www-data’ user. Further enumeration reveals the database password for LimeSurvey, which is reused by the system user ‘ron’, allowing us to escalate access. The server also runs a local instance of the Consul Agent as ‘root’. By registering a malicious service via the Consul API, we can escalate privileges and gain root access.

 Pit is a medium difficulty Linux machine that focuses on SNMP enumeration and exploitation, while introducing basic SELinux restrictions and web misconfigurations. By enumerating SNMP via the default insecure public community, information about filesystems and users can be obtained. This allows attackers to discover and gain access to a vulnerable SeedDMS instance, which was incorrectly patched by applying Apache .htaccess rules to an Nginx server where they are not effective. Exploiting CVE-2019-12744 results in Remote Command Execution (with some SELinux restrictions) and subsequent access to a Cockpit console via password reuse. Privileges are escalated by writing a Bash script that is executed as an SNMP extension when the corresponding OID is queried.
Pit is a medium difficulty Linux machine that focuses on SNMP enumeration and exploitation, while introducing basic SELinux restrictions and web misconfigurations. By enumerating SNMP via the default insecure public community, information about filesystems and users can be obtained. This allows attackers to discover and gain access to a vulnerable SeedDMS instance, which was incorrectly patched by applying Apache .htaccess rules to an Nginx server where they are not effective. Exploiting CVE-2019-12744 results in Remote Command Execution (with some SELinux restrictions) and subsequent access to a Cockpit console via password reuse. Privileges are escalated by writing a Bash script that is executed as an SNMP extension when the corresponding OID is queried.

 Union is an medium difficulty linux machine featuring a web application that is vulnerable to SQL Injection. There are filters in place which prevent SQLMap from dumping the database. Users are intended to manually craft union statements to extract information from the database and website source code. The database contains a flag that can be used to authenticate against the machine and upon authentication the webserver runs an iptables command to enable port 22. The credentials for SSH are in the PHP Configuration file used to authenticate against MySQL. Once on the machine, users can examine the source code of the web application and find out by setting the X-FORWARDED-FOR header, they can perform command injection on the system command used by the webserver to whitelist IP Addresses.
Union is an medium difficulty linux machine featuring a web application that is vulnerable to SQL Injection. There are filters in place which prevent SQLMap from dumping the database. Users are intended to manually craft union statements to extract information from the database and website source code. The database contains a flag that can be used to authenticate against the machine and upon authentication the webserver runs an iptables command to enable port 22. The credentials for SSH are in the PHP Configuration file used to authenticate against MySQL. Once on the machine, users can examine the source code of the web application and find out by setting the X-FORWARDED-FOR header, they can perform command injection on the system command used by the webserver to whitelist IP Addresses.

 ‘Strutted’ is an medium-difficulty Linux machine featuring a website for a company offering image hosting solutions. The website provides a Docker container with the version of Apache Struts that is vulnerable to ‘CVE-2024-53677’, which is leveraged to gain a foothold on the system. Further enumeration reveals the ‘tomcat-users.xml’ file with a plaintext password used to authenticate as ‘james’. For privilege escalation, we abuse ‘tcpdump’ while being used with ‘sudo’ to create a copy of the ‘bash’ binary with the ‘SUID’ bit set, allowing us to gain a ‘root’ shell.
‘Strutted’ is an medium-difficulty Linux machine featuring a website for a company offering image hosting solutions. The website provides a Docker container with the version of Apache Struts that is vulnerable to ‘CVE-2024-53677’, which is leveraged to gain a foothold on the system. Further enumeration reveals the ‘tomcat-users.xml’ file with a plaintext password used to authenticate as ‘james’. For privilege escalation, we abuse ‘tcpdump’ while being used with ‘sudo’ to create a copy of the ‘bash’ binary with the ‘SUID’ bit set, allowing us to gain a ‘root’ shell.

 Compiled is a medium-difficulty Windows machine featuring a Gitea instance and a web application that clones Git repository URLs on the backend. The server’s Git version is vulnerable to CVE-2024-32002, which can be exploited to gain initial access with a Git Bash shell as Richard. By cracking the password hash retrieved from the Gitea database file, the password for user Emily can be obtained. Privilege escalation to Administrator is achieved by exploiting CVE-2024-20656, a vulnerability in the Visual Studio Code version installed on the server.
Compiled is a medium-difficulty Windows machine featuring a Gitea instance and a web application that clones Git repository URLs on the backend. The server’s Git version is vulnerable to CVE-2024-32002, which can be exploited to gain initial access with a Git Bash shell as Richard. By cracking the password hash retrieved from the Gitea database file, the password for user Emily can be obtained. Privilege escalation to Administrator is achieved by exploiting CVE-2024-20656, a vulnerability in the Visual Studio Code version installed on the server.

 Bolt is a medium difficulty Linux machine featuring a custom web application providing a docker image file having multiple layers with deleted files. Enumerating deleted database file reveals credentials for an application revealing hints to demo site. Further enumeration of the docker image reveals an invitation token which allows registration to the site. The site is found to be vulnerable to Server Side Template Injection. Foothold can be gained by exploiting the SSTI vulnerability. Enumerating passbolt configuration reveals database credentials that can be used to achieve lateral movement. Root password can be obtained by exploiting the passbolt server.
Bolt is a medium difficulty Linux machine featuring a custom web application providing a docker image file having multiple layers with deleted files. Enumerating deleted database file reveals credentials for an application revealing hints to demo site. Further enumeration of the docker image reveals an invitation token which allows registration to the site. The site is found to be vulnerable to Server Side Template Injection. Foothold can be gained by exploiting the SSTI vulnerability. Enumerating passbolt configuration reveals database credentials that can be used to achieve lateral movement. Root password can be obtained by exploiting the passbolt server.

 Instant is a medium difficulty machine that includes reverse engineering a mobile application, exploiting API endpoints, and cracking encrypted hashes and files. Players will analyze an APK to extract sensitive information and a hardcoded authorization token, then they will exploit an API endpoint vulnerable to Arbitrary File Read. Finally, they will achieve full system compromise by decrypting and analyzing encrypted session data from Solar-PuTTY.
Instant is a medium difficulty machine that includes reverse engineering a mobile application, exploiting API endpoints, and cracking encrypted hashes and files. Players will analyze an APK to extract sensitive information and a hardcoded authorization token, then they will exploit an API endpoint vulnerable to Arbitrary File Read. Finally, they will achieve full system compromise by decrypting and analyzing encrypted session data from Solar-PuTTY.

 Waldo is a medium difficulty machine, which highlights the risk of insufficient input validation, provides the challenge of rbash escape or bypassing, and showcases an interesting privilege escalation vector involving Linux Capabilities, all of which may be found in real environments.
Waldo is a medium difficulty machine, which highlights the risk of insufficient input validation, provides the challenge of rbash escape or bypassing, and showcases an interesting privilege escalation vector involving Linux Capabilities, all of which may be found in real environments.

Hawk is a medium to hard difficulty machine, which provides excellent practice in pentesting Drupal. The exploitable H2 DBMS installation is also realistic as web-based SQL consoles (RavenDB etc.) are found in many environments. The OpenSSL decryption challenge increases the difficulty of this machine.

Jeeves is not overly complicated, however it focuses on some interesting techniques and provides a great learning experience. As the use of alternate data streams is not very common, some users may have a hard time locating the correct escalation path.

Toolbox is an easy difficulty Windows machine that features a Docker Toolbox installation. Docker Toolbox is used to host a Linux container, which serves a site that is found vulnerable to SQL injection. This is leveraged to gain a foothold on the Docker container. Docker Toolbox default credentials and host file system access are leveraged to gain a privileged shell on the host.

 SolidState is a medium difficulty machine that requires chaining of multiple attack vectors in order to get a privileged shell. As a note, in some cases the exploit may fail to trigger more than once and a machine reset is required.
SolidState is a medium difficulty machine that requires chaining of multiple attack vectors in order to get a privileged shell. As a note, in some cases the exploit may fail to trigger more than once and a machine reset is required.

Devzat is a medium Linux machine that features a web server and the ‘Devzat’ chat application. Upon enumerating the web server, a new vhost called ‘pets’ can be discovered. The ‘pets’ vhost has a ‘.git’ directory with listing enabled, providing access to the source code of ‘pets’. Reviewing the source code, a command injection vulnerability is discovered allowing an attacker to gain a reverse shell as the user ‘patrick’. Logging to the ‘Devzat’ chat application as ‘patrick’ on the remote machine the chat history between ‘patrick’ and ‘admin’ reveals that ‘InfluxDB’ is installed on the remote system. Enumerating ‘InfluxDB’ it is discovered that the version installed is vulnerable to CVE-2019-20933, an authentication bypass vulnerability. Exploiting the aforementioned vulnerability an attacker is able to dump the contents of ‘InfluxDB’ revealing the password of the user ‘catherine’. Switching from ‘patrick’ to ‘catherine’ and logging in to the Devzat chat application as ‘catherine’ the chat history between t...

Shocker, while fairly simple overall, demonstrates the severity of the renowned Shellshock exploit, which affected millions of public-facing servers.

Previse is a easy machine that showcases Execution After Redirect (EAR) which allows users to retrieve the contents and make requests to accounts.php whilst unauthenticated which leads to abusing PHP ‘exec()’ function since user inputs are not sanitized allowing remote code execution against the target, after gaining a www-data shell privilege escalation starts with the retrieval and cracking of a custom MD5Crypt hash which consists of a unicode salt and once cracked allows users to gain SSH access to the target then abusing a sudo executable script which does not include absolute paths of the functions it utilises which allows users to perform PATH hijacking on the target to compromise the machine.

 Pilgrimage is an easy-difficulty Linux machine featuring a web application with an exposed ‘Git’ repository. Analysing the underlying filesystem and source code reveals the use of a vulnerable version of ‘ImageMagick’, which can be used to read arbitrary files on the target by embedding a malicious ‘tEXT’ chunk into a PNG image. The vulnerability is leveraged to obtain a ‘SQLite’ database file containing a plaintext password that can be used to SSH into the machine. Enumeration of the running processes reveals a ‘Bash’ script executed by ‘root’ that calls a vulnerable version of the ‘Binwalk’ binary. By creating another malicious PNG, ‘CVE-2022-4510’ is leveraged to obtain Remote Code Execution (RCE) as ‘root’.
Pilgrimage is an easy-difficulty Linux machine featuring a web application with an exposed ‘Git’ repository. Analysing the underlying filesystem and source code reveals the use of a vulnerable version of ‘ImageMagick’, which can be used to read arbitrary files on the target by embedding a malicious ‘tEXT’ chunk into a PNG image. The vulnerability is leveraged to obtain a ‘SQLite’ database file containing a plaintext password that can be used to SSH into the machine. Enumeration of the running processes reveals a ‘Bash’ script executed by ‘root’ that calls a vulnerable version of the ‘Binwalk’ binary. By creating another malicious PNG, ‘CVE-2022-4510’ is leveraged to obtain Remote Code Execution (RCE) as ‘root’.

‘PermX’ is an Easy Difficulty Linux machine featuring a learning management system vulnerable to unrestricted file uploads via CVE-2023-4220. This vulnerability is leveraged to gain a foothold on the machine. Enumerating the machine reveals credentials that lead to SSH access. A ‘sudo’ misconfiguration is then exploited to gain a ‘root’ shell.

 Nunchucks is a easy machine that explores a NodeJS-based Server Side Template Injection (SSTI) leading to an AppArmor bug which disregards the binary AppArmor profile while executing scripts that include the shebang of the profiled application.
Nunchucks is a easy machine that explores a NodeJS-based Server Side Template Injection (SSTI) leading to an AppArmor bug which disregards the binary AppArmor profile while executing scripts that include the shebang of the profiled application.

 This UHC qualifier box was a neat take on some common NodeJS vulnerabilities. First there’s a NoSQL authentication bypass. Then I’ll use XXE in some post upload ability to leak files, including the site source. With that, I’ll spot a deserialization vulnerability which I can abuse to get RCE. I’ll get the user’s password from Mongo via the shell or through the NoSQL injection, and use that to escalate to root. In Beyond Root, a look at characters that broke the deserialization payload, and scripting the NoSQL injection.
This UHC qualifier box was a neat take on some common NodeJS vulnerabilities. First there’s a NoSQL authentication bypass. Then I’ll use XXE in some post upload ability to leak files, including the site source. With that, I’ll spot a deserialization vulnerability which I can abuse to get RCE. I’ll get the user’s password from Mongo via the shell or through the NoSQL injection, and use that to escalate to root. In Beyond Root, a look at characters that broke the deserialization payload, and scripting the NoSQL injection.

 Nibbles is a fairly simple machine, however with the inclusion of a login blacklist, it is a fair bit more challenging to find valid credentials. Luckily, a username can be enumerated and guessing the correct password does not take long for most.
Nibbles is a fairly simple machine, however with the inclusion of a login blacklist, it is a fair bit more challenging to find valid credentials. Luckily, a username can be enumerated and guessing the correct password does not take long for most.

 Networked is an Easy difficulty Linux box vulnerable to file upload bypass, leading to code execution. Due to improper sanitization, a crontab running as the user can be exploited to achieve command execution. The user has privileges to execute a network configuration script, which can be leveraged to execute commands as root.
Networked is an Easy difficulty Linux box vulnerable to file upload bypass, leading to code execution. Due to improper sanitization, a crontab running as the user can be exploited to achieve command execution. The user has privileges to execute a network configuration script, which can be leveraged to execute commands as root.

 Netmon is an easy difficulty Windows box with simple enumeration and exploitation. PRTG is running, and an FTP server with anonymous access allows reading of PRTG Network Monitor configuration files. The version of PRTG is vulnerable to RCE which can be exploited to gain a SYSTEM shell.
Netmon is an easy difficulty Windows box with simple enumeration and exploitation. PRTG is running, and an FTP server with anonymous access allows reading of PRTG Network Monitor configuration files. The version of PRTG is vulnerable to RCE which can be exploited to gain a SYSTEM shell.

Mirai demonstrates one of the fastest-growing attack vectors in modern times; improperly configured IoT devices. This attack vector is constantly on the rise as more and more IoT devices are being created and deployed around the globe, and is actively being exploited by a wide variety of botnets. Internal IoT devices are also being used for long-term persistence by malicious actors.

Love is an easy windows machine where it features a voting system application that suffers from an authenticated remote code execution vulnerability. Our port scan reveals a service running on port 5000 where browsing the page we discover that we are not allowed to access the resource. Furthermore a file scanner application is running on the same server which is though effected by a SSRF vulnerability where it's exploitation gives access to an internal password manager. We can then gather credentials for the voting system and by executing the remote code execution attack as phoebe user we get the initial foothold on system. Basic windows enumeration reveals that the machine suffers from an elevated misconfiguration. Bypassing the applocker restriction we manage to install a malicious msi file that finally results in a reverse shell as the system account.

Legacy is a fairly straightforward beginner-level machine which demonstrates the potential security risks of SMB on Windows. Only one publicly available exploit is required to obtain administrator access.

 Lame is an easy Linux machine, requiring only one exploit to obtain root access. It was the first machine published on Hack The Box and was often the first machine for new users prior to its retirement.
Lame is an easy Linux machine, requiring only one exploit to obtain root access. It was the first machine published on Hack The Box and was often the first machine for new users prior to its retirement.

 Knife is an easy difficulty Linux machine that features an application which is running on a backdoored version of PHP. This vulnerability is leveraged to obtain the foothold on the server. A sudo misconfiguration is then exploited to gain a root shell.
Knife is an easy difficulty Linux machine that features an application which is running on a backdoored version of PHP. This vulnerability is leveraged to obtain the foothold on the server. A sudo misconfiguration is then exploited to gain a root shell.

Keeper is an easy-difficulty Linux machine that features a support ticketing system that uses default credentials. Enumerating the service, we are able to see clear text credentials that lead to SSH access. With ‘SSH’ access, we can gain access to a KeePass database dump file, which we can leverage to retrieve the master password. With access to the ‘Keepass’ database, we can access the root ‘SSH’ keys, which are used to gain a privileged shell on the host.

Jerry is an easy-difficulty Windows machine that showcases how to exploit Apache Tomcat, leading to an ‘NT Authority\SYSTEM` shell, thus fully compromising the target.

 Irked is a pretty simple and straight-forward box which requires basic enumeration skills. It shows the need to scan all ports on machines and to investigate any out of the place binaries found while enumerating a system.
Irked is a pretty simple and straight-forward box which requires basic enumeration skills. It shows the need to scan all ports on machines and to investigate any out of the place binaries found while enumerating a system.

Granny, while similar to Grandpa, can be exploited using several different methods. The intended method of solving this machine is the widely-known Webdav upload vulnerability.

Grandpa is one of the simpler machines on Hack The Box, however it covers the widely-exploited CVE-2017-7269. This vulnerability is trivial to exploit and granted immediate access to thousands of IIS servers around the globe when it became public knowledge.

 Apuntes de Buffer Overflow con un ejemplo práctico (Spanish)
Apuntes de Buffer Overflow con un ejemplo práctico (Spanish)

 Horizontall is an easy difficulty Linux machine were only HTTP and SSH services are exposed. Enumeration of the website reveals that it is built using the Vue JS framework. Reviewing the source code of the Javascript file, a new virtual host is discovered. This host contains the ‘Strapi Headless CMS’ which is vulnerable to two CVEs allowing potential attackers to gain remote code execution on the system as the ‘strapi’ user. Then, after enumerating services listening only on localhost on the remote machine, a Laravel instance is discovered. In order to access the port that Laravel is listening on, SSH tunnelling is used. The Laravel framework installed is outdated and running on debug mode. Another CVE can be exploited to gain remote code execution through Laravel as ‘root’.
Horizontall is an easy difficulty Linux machine were only HTTP and SSH services are exposed. Enumeration of the website reveals that it is built using the Vue JS framework. Reviewing the source code of the Javascript file, a new virtual host is discovered. This host contains the ‘Strapi Headless CMS’ which is vulnerable to two CVEs allowing potential attackers to gain remote code execution on the system as the ‘strapi’ user. Then, after enumerating services listening only on localhost on the remote machine, a Laravel instance is discovered. In order to access the port that Laravel is listening on, SSH tunnelling is used. The Laravel framework installed is outdated and running on debug mode. Another CVE can be exploited to gain remote code execution through Laravel as ‘root’.

GoodGames is an Easy linux machine that showcases the importance of sanitising user inputs in web applications to prevent SQL injection attacks, using strong hashing algorithms in database structures to prevent the extraction and cracking of passwords from a compromised database, along with the dangers of password re-use. It also highlights the dangers of using render_template_string in a Python web application where user input is reflected, allowing Server Side Template Injection (SSTI) attacks. Privilege escalation involves docker hosts enumeration and shows how having admin privileges in a container and a low privilege user on the host machine can be dangerous, allowing attackers to escalate privileges to compromise the system.

Editorial is an easy difficulty Linux machine that features a publishing web application vulnerable to ‘Server-Side Request Forgery (SSRF)’. This vulnerability is leveraged to gain access to an internal running API, which is then leveraged to obtain credentials that lead to SSH access to the machine. Enumerating the system further reveals a Git repository that is leveraged to reveal credentials for a new user. The ‘root’ user can be obtained by exploiting CVE-2022-24439 and the sudo configuration.

Driver is an easy Windows machine that focuses on printer exploitation. Enumeration of the machine reveals that a web server is listening on port 80, along with SMB on port 445 and WinRM on port 5985. Navigation to the website reveals that it protected using basic HTTP authentication. While trying common credentials the ‘admin:admin’ credential is accepted and we are able to visit the webpage. The webpage provides a feature to upload printer firmwares on an SMB share for a remote team to test and verify. Uploading a Shell Command File that contains a command to fetch a remote file from our local machine, leads to the NTLM hash of the user ‘tony’ relayed back to us. Cracking the captured hash to retrieve a plaintext password we are able login as ‘tony’, using WinRM. Then, switching over to a meterpreter session it is discovered that the machine is vulnerable to a local privilege exploit that abuses a specific printer driver that is present on the remote machine. Using the exploit we can get a session as ‘NT...

Delivery is an easy difficulty Linux machine that features the support ticketing system osTicket where it is possible by using a technique called TicketTrick, a non-authenticated user to be granted with access to a temporary company email. This permits the registration at MatterMost and the join of internal team channel. It is revealed through that channel that users have been using same password variant "PleaseSubscribe!" for internal access. In channel it is also disclosed the credentials for the mail user which can give the initial foothold to the system. While enumerating the file system we come across the mattermost configuration file which reveals MySQL database credentials. By having access to the database a password hash can be extracted from Users table and crack it using the "PleaseSubscribe!" pattern. After cracking the hash it is possible to login as user root.

CozyHosting is an easy-difficulty Linux machine that features a ‘Spring Boot’ application. The application has the ‘Actuator’ endpoint enabled. Enumerating the endpoint leads to the discovery of a user's session cookie, leading to authenticated access to the main dashboard. The application is vulnerable to command injection, which is leveraged to gain a reverse shell on the remote machine. Enumerating the application ‘JAR’ file, hardcoded credentials are discovered and used to log into the local database. The database contains a hashed password, which once cracked is used to log into the machine as the user ‘josh’. The user is allowed to run ‘ssh’ as ‘root’, which is leveraged to fully escalate privileges.

 Chemistry is an easy-difficulty Linux machine that showcases a Remote Code Execution (RCE) vulnerability in the pymatgen (CVE-2024-23346) Python library by uploading a malicious CIF file to the hosted CIF Analyzer website on the target. After discovering and cracking hashes, we authenticate to the target via SSH as rosa user. For privilege escalation, we exploit a Path Traversal vulnerability that leads to an Arbitrary File Read in a Python library called AioHTTP (CVE-2024-23334) which is used on the web application running internally to read the root flag.
Chemistry is an easy-difficulty Linux machine that showcases a Remote Code Execution (RCE) vulnerability in the pymatgen (CVE-2024-23346) Python library by uploading a malicious CIF file to the hosted CIF Analyzer website on the target. After discovering and cracking hashes, we authenticate to the target via SSH as rosa user. For privilege escalation, we exploit a Path Traversal vulnerability that leads to an Arbitrary File Read in a Python library called AioHTTP (CVE-2024-23334) which is used on the web application running internally to read the root flag.

 Cap is an easy difficulty Linux machine running an HTTP server that performs administrative functions including performing network captures. Improper controls result in Insecure Direct Object Reference (IDOR) giving access to another user’s capture. The capture contains plaintext credentials and can be used to gain foothold. A Linux capability is then leveraged to escalate to root.
Cap is an easy difficulty Linux machine running an HTTP server that performs administrative functions including performing network captures. Improper controls result in Insecure Direct Object Reference (IDOR) giving access to another user’s capture. The capture contains plaintext credentials and can be used to gain foothold. A Linux capability is then leveraged to escalate to root.

 BoardLight is an easy difficulty Linux machine that features a Dolibarr instance vulnerable to CVE-2023-30253. This vulnerability is leveraged to gain access as www-data. After enumerating and dumping the web configuration file contents, plaintext credentials lead to SSH access to the machine. Enumerating the system, a SUID binary related to enlightenment is identified which is vulnerable to privilege escalation via CVE-2022-37706 and can be abused to leverage a root shell.
BoardLight is an easy difficulty Linux machine that features a Dolibarr instance vulnerable to CVE-2023-30253. This vulnerability is leveraged to gain access as www-data. After enumerating and dumping the web configuration file contents, plaintext credentials lead to SSH access to the machine. Enumerating the system, a SUID binary related to enlightenment is identified which is vulnerable to privilege escalation via CVE-2022-37706 and can be abused to leverage a root shell.

 Blocky is fairly simple overall, and was based on a real-world machine. It demonstrates the risks of bad password practices as well as exposing internal files on a public facing system. On top of this, it exposes a massive potential attack vector: Minecraft. Tens of thousands of servers exist that are publicly accessible, with the vast majority being set up and configured by young and inexperienced system administrators.
Blocky is fairly simple overall, and was based on a real-world machine. It demonstrates the risks of bad password practices as well as exposing internal files on a public facing system. On top of this, it exposes a massive potential attack vector: Minecraft. Tens of thousands of servers exist that are publicly accessible, with the vast majority being set up and configured by young and inexperienced system administrators.

 Bashed is a fairly easy machine which focuses mainly on fuzzing and locating important files. As basic access to the crontab is restricted.
Bashed is a fairly easy machine which focuses mainly on fuzzing and locating important files. As basic access to the crontab is restricted.

 Antique is an easy Linux machine featuring a network printer disclosing credentials through SNMP string which allows logging into telnet service. Foothold can be obtained by exploiting a feature in printer. CUPS administration service running locally. This service can be exploited further to gain root access on the server.
Antique is an easy Linux machine featuring a network printer disclosing credentials through SNMP string which allows logging into telnet service. Foothold can be obtained by exploiting a feature in printer. CUPS administration service running locally. This service can be exploited further to gain root access on the server.

 Alert is an easy-difficulty Linux machine with a website to upload, view, and share markdown files. The site is vulnerable to cross-site scripting (XSS), which is exploited to access an internal page vulnerable to Arbitrary File Read and leveraged to gain access to a password hash. The hash is then cracked to reveal the credentials leveraged to gain ‘SSH’ access to the target. Enumeration of processes running on the system shows a ‘PHP’ file that is being executed regularly, which has excessive privileges for the management group our user is a member of and allows us to overwrite the file for code execution as root.
Alert is an easy-difficulty Linux machine with a website to upload, view, and share markdown files. The site is vulnerable to cross-site scripting (XSS), which is exploited to access an internal page vulnerable to Arbitrary File Read and leveraged to gain access to a password hash. The hash is then cracked to reveal the credentials leveraged to gain ‘SSH’ access to the target. Enumeration of processes running on the system shows a ‘PHP’ file that is being executed regularly, which has excessive privileges for the management group our user is a member of and allows us to overwrite the file for code execution as root.

 In this machine, we are exploiting XSS to perform CSRF and abusing APIs to achieve RCE. Additionally, we are taking advantage of a Golang binary with sudoers configuration.
In this machine, we are exploiting XSS to perform CSRF and abusing APIs to achieve RCE. Additionally, we are taking advantage of a Golang binary with sudoers configuration.

 On this machine, we are exploiting Insecure Cookie Handling, Time-Based SQL Injection, DOM XXE, and SUID with PATH Hijacking. Additionally, we performed brute force on an FTP user and achieved a file upload with a bypass.
On this machine, we are exploiting Insecure Cookie Handling, Time-Based SQL Injection, DOM XXE, and SUID with PATH Hijacking. Additionally, we performed brute force on an FTP user and achieved a file upload with a bypass.

 We are exploiting the Log4Shell vulnerability (CVE-2021-44228) on this machine and taking advantage of MongoDB misconfiguration.
We are exploiting the Log4Shell vulnerability (CVE-2021-44228) on this machine and taking advantage of MongoDB misconfiguration.

 In this machine, we take advantage of an FTP misconfiguration to obtain credentials and crack hashes. Additionally, we exploit a PostgreSQL database using SQL Injection and leverage the sudoers file.
In this machine, we take advantage of an FTP misconfiguration to obtain credentials and crack hashes. Additionally, we exploit a PostgreSQL database using SQL Injection and leverage the sudoers file.
 Python TCP Port Scanner Script.
Python TCP Port Scanner Script.
 Python ICMP Port Scanner Script.
Python ICMP Port Scanner Script.
 Macchanger Script.
Macchanger Script.
 Keylogger Malware Script.
Keylogger Malware Script.
 HTTP Spoofing (MITM Attack).
HTTP Spoofing (MITM Attack).
 HTTP Sniffer (MITM Attack).
HTTP Sniffer (MITM Attack).
 Forward Shell Script.
Forward Shell Script.
 DNS Sniffer (MITM Attack).
DNS Sniffer (MITM Attack).
 DNS Poisoning (MITM Attack).
DNS Poisoning (MITM Attack).
 Browser Stealer Script.
Browser Stealer Script.
 ARP Scanner Script.
ARP Scanner Script.
 ARP Poisoning (MITM Attack).
ARP Poisoning (MITM Attack).

 In this machine, we are exploiting an IDOR with RCE. With respect to privilege escalation, we are taking advantage of leaked credential files and exploiting SUID files through PATH Hijacking.
In this machine, we are exploiting an IDOR with RCE. With respect to privilege escalation, we are taking advantage of leaked credential files and exploiting SUID files through PATH Hijacking.

 Apuntes de la vulnerabilidad ShellShock (Spanish)
Apuntes de la vulnerabilidad ShellShock (Spanish)

 Apuntes de la vulnerabilidad Mass-Asignment o Parameter Binding (Spanish)
Apuntes de la vulnerabilidad Mass-Asignment o Parameter Binding (Spanish)

 Apuntes de abuso de subidas de archivos (Spanish)
Apuntes de abuso de subidas de archivos (Spanish)

 Docker Commands Cheat Sheet (Spanish)
Docker Commands Cheat Sheet (Spanish)

 Apuntes de ataques de deserialización (Spanish)
Apuntes de ataques de deserialización (Spanish)

 Ejemplos de abuso de APIs (Spanish)
Ejemplos de abuso de APIs (Spanish)

 In this machine, we take advantage of an SMB misconfiguration, exploit an MSSQL database, and escalate privileges through regular expressions in a Windows system.
In this machine, we take advantage of an SMB misconfiguration, exploit an MSSQL database, and escalate privileges through regular expressions in a Windows system.

 In this machine, we exploit LLMNR/NBT-NS poisoning to capture NTLMv2 hashes and crack them.
In this machine, we exploit LLMNR/NBT-NS poisoning to capture NTLMv2 hashes and crack them.

 In this machine we are taking advantage of misconfigured MariaDB server credentials.
In this machine we are taking advantage of misconfigured MariaDB server credentials.

 In this machine, we are exploiting a misconfigured Redis service that has no credentials.
In this machine, we are exploiting a misconfigured Redis service that has no credentials.

 In this machine, we are taking advantage of FTP anonymous login and exploiting the login anel with Hydra.
In this machine, we are taking advantage of FTP anonymous login and exploiting the login anel with Hydra.

 In this machine, we are exploiting an SQL Injection in the login panel.
In this machine, we are exploiting an SQL Injection in the login panel.

 In this machine, we are taking advantage of a misconfigured Telnet service using blank password.
In this machine, we are taking advantage of a misconfigured Telnet service using blank password.

 In this machine we are taking advantage of ftp anonymous login.
In this machine we are taking advantage of ftp anonymous login.

 In this machine we are taking advantage of resource sharing misconfiguration in SMB service.
In this machine we are taking advantage of resource sharing misconfiguration in SMB service.